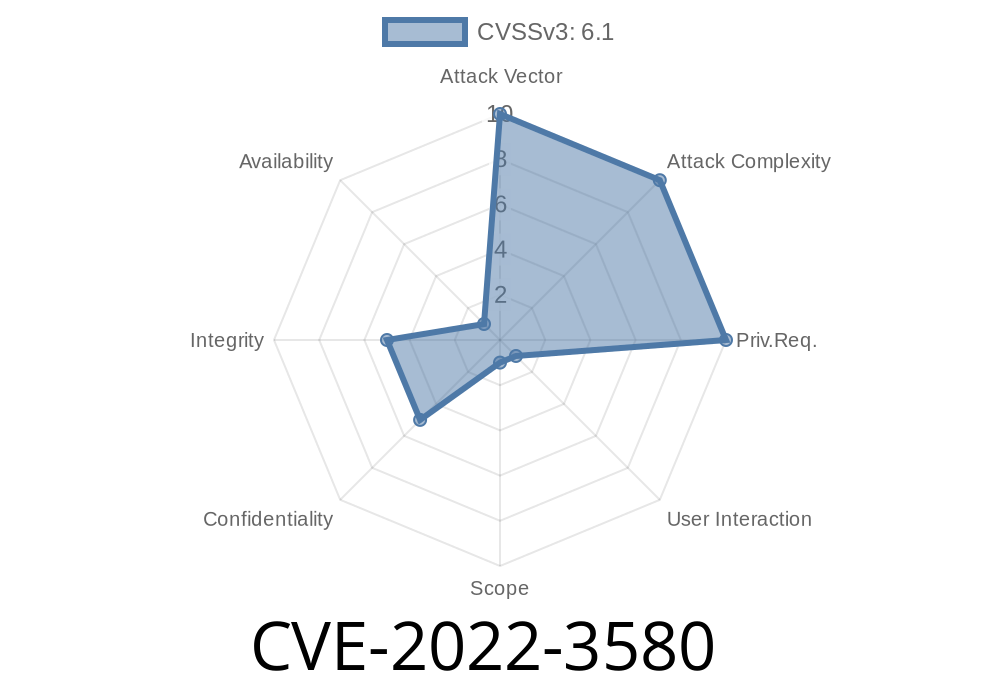
The problem arises due to insufficient validation of user input. Thus, it may be exploited by malicious users to conduct various actions that may cause significant damage to the enterprise. Such actions may include:
Changing the administrator role.
Changing the billing address.
Modifying the password.
Setting another user as administrator.
The users of the affected site will be able to exploit this vulnerability if they have access to the source code. The risk of exploitation may be increased if we compare the version of the component with the version of the server. It has been confirmed that the exploitation of this vulnerability is possible only if the source code is accessible. The source code is available for download from the vendor’s website.
Vulnerability overview
This article discusses the vulnerabilities of the software. It provides a brief overview of the vulnerability and risk levels associated with it. In particular, it discusses:
The nature of the problem and what it may be exploited for.
Any known exploits related to this vulnerability.
The significance of any mitigation strategies available to address this vulnerability.
Limitations and Patching Instructions
This is a server-side vulnerability.
All versions of the affected software are vulnerable.
The vulnerability may only be exploited with access to the source code of the component.
References: https://en.wikipedia.org/wiki/Cross-site_scripting
http://www.owasp.org/index.php/Cross-Site_Scripting_(XSS)
VENDOR RESPONSE & MITIGATION
The vendor has not given a public response to this vulnerability. The company has offered no evidence that the vulnerability has been fixed.
Timeline
Published on: 10/18/2022 11:15:00 UTC
Last modified on: 10/19/2022 03:17:00 UTC