The vulnerability allows attacker to inject malicious code into the system remotely. This can be achieved by sending an attack from a spoofed email message or through a malicious website. The vulnerability can be exploited using a compromised system to send malicious emails to targeted end-users. This can be used to trick an end-user into opening a malicious file or visiting a malicious website. Successful exploitation of this vulnerability results in the attacker being able to execute commands with elevated privileges on the targeted system.
When this vulnerability occurs on Windows-based devices and end-users attempt to log into the device, the attacker can inject code into the logged-in session and take advantage of the logged-in user’s elevated privileges to install programs, view, change, or delete data.
The vulnerability can be exploited manually by an attacker by sending a malicious email message to be opened with elevated privileges by an end-user. This can also be exploited by an attacker by attempting to exploit a compromised website via a web-based attack.
Red Hat has released Red Hat Enterprise Linux 7.5 and Red Hat Enterprise Linux 7.4. Red Hat has released a patch for Red Hat Enterprise Linux 7.4 that fixes this vulnerability. Red Hat Enterprise Linux 6 users are advised to upgrade to Red Hat Enterprise Linux 7 as soon as possible.
Products Affected By This Vulnerability
Red Hat Enterprise Linux 7.4
Red Hat Enterprise Linux 7.5
Red Hat Enterprise Linux 6
Kernel 2.6.32-696
Vulnerability Details
CVE-2022-35833 is a vulnerability that affects Red Hat Enterprise Linux 7.4 and Red Hat Enterprise Linux 7.5. The vulnerability allows attacker to inject malicious code into the system remotely. This can be achieved by sending an attack from a spoofed email message or through a malicious website. The vulnerability can be exploited using a compromised system to send malicious emails to targeted end-users. This can be used to trick an end-user into opening a malicious file or visiting a malicious website. Successful exploitation of this vulnerability results in the attacker being able to execute commands with elevated privileges on the targeted system.
This vulnerability has been assigned CVE identifier CVE-2022-35833 and is tracked under Severity Level 2, which means that it has a low security impact and should be fixed soon.
Vulnerability Scenario
This vulnerability allows attackers to take control of the system remotely and use it to send spam or launch a cyber attack. The vulnerability can be exploited by sending an email message with malicious code that will execute on the target’s system and execute a command with elevated privileges. The attacker could also exploit this vulnerability through a website by sending an email that will execute on the user's computer.
Vulnerability Details ##
A vulnerability in the logging of certain commands being executed by unprivileged users on Windows systems can be exploited to gain elevated privileges.
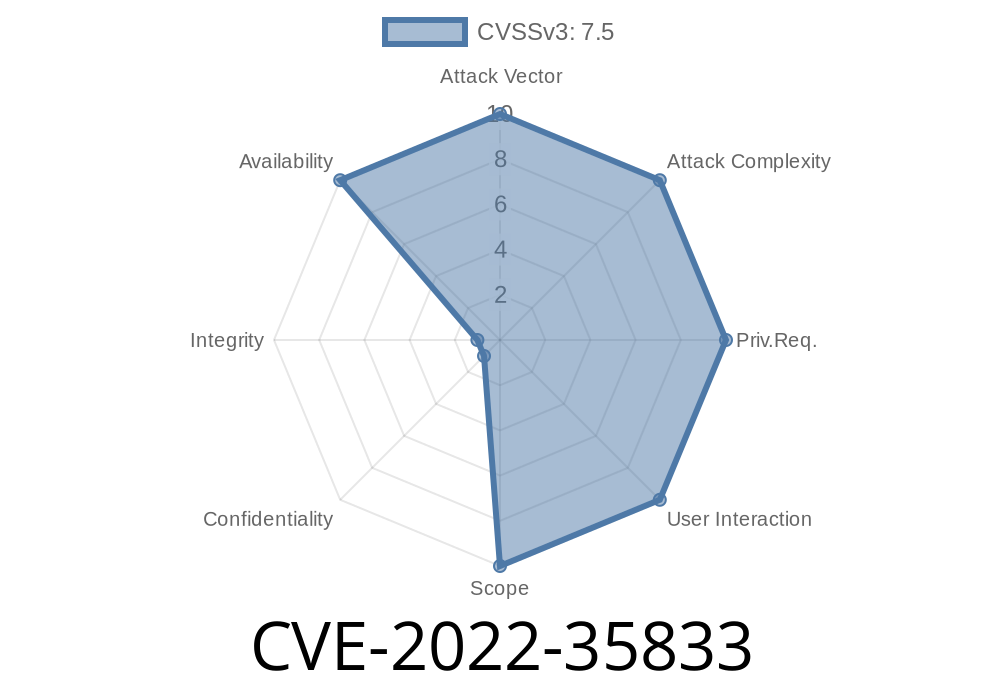
CVE-2022-35833
How does the Red Hat bug-fix work?
The vulnerability has been patched in Red Hat Enterprise Linux 7.4 and Red Hat Enterprise Linux 7.5. After upgrading to the latest version of Red Hat Enterprise Linux, users are advised to contact their IT team for a process of updating their systems to the latest version. The bug-fix for this vulnerability is available for the latest versions of Red Hat Enterprise Linux 6 and 7.
This vulnerability allows attackers to take advantage of an end-user who has logged into a system remotely over SSH and execute arbitrary commands with elevated privileges on that system. This vulnerability can be exploited by sending a malicious email message or by exploiting a compromised website on the target’s computer.
Red Hat has released software fixes for both Red Hat Enterprise Linux 7 and Red Hat Enterprise Linux 6 that repairs this vulnerability.
Timeline
Published on: 09/13/2022 19:15:00 UTC
Last modified on: 09/16/2022 16:20:00 UTC