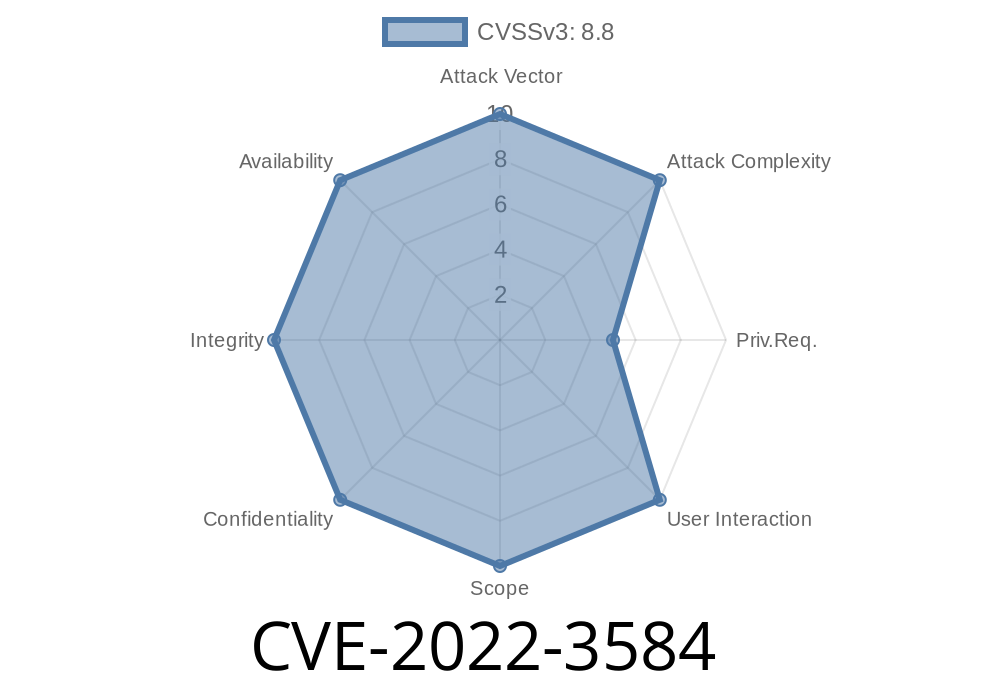
This software can be exploited via Remote Code Execution and RCE. Some file extensions may be affected. These are edituser.php, editgroup.php, editgroup2.php, editgroup3.php, editgroup4.php, editgroup5.php, editgroup6.php, editgroup7.php, editgroup8.php, editgroup9.php, editgroup10.php, editgroup11.php, editgroup12.php, editgroup13.php, editgroup14.php, editgroup15.php, editgroup16.php, editgroup17.php, editgroup18.php, editgroup19.php, editgroup20.php, editgroup21.php, editgroup22.php, editgroup23.php, editgroup24.php, editgroup25.php, editgroup26.php, editgroup27.php, editgroup28.php, editgroup29.php, editgroup30.php, editgroup31.php, editgroup32.php, editgroup33.php, editgroup34.php, editgroup35.php, editgroup36.php, editgroup37.php, editgroup38.php, editgroup39.php, editgroup40.php, editgroup41.php, editgroup42.php, editgroup43.php, editgroup44.php, editgroup45.php, editgroup46.
How to edit this article?
To edit:
Log in to your Joomla! administrator panel.
Go to Extensions > Component > Template Components.
From the list of available templates, select the template that you want to edit.
Edit the source code if necessary and save your changes.
How to find the vulnerable file?
If one of these editgroup files is used to upload or download a file, then the files may be vulnerable.
To see if one of these edits is exploited, search on "CVE-2022-3584" in Shodan: https://www.shodan.io/search?query=CVE-2022-3584
How to check if your site is affected by CVE-2022-3584?
To check if your site is affected by CVE-2022-3584, open a command prompt, navigate to the install directory of the software and run:
php -v
If you see an error message like this one:
"Operating system not supported" or "Fatal error: Call to undefined function" then your system is affected by CVE-2022-3584.
Timeline
Published on: 10/18/2022 11:15:00 UTC
Last modified on: 10/19/2022 03:45:00 UTC