This vulnerability is often referred to as “FortiSOAR Management Interface Remote Code Execution Vulnerability” and has been assigned Common Vulnerability and Exposure number ‘CVE-2018-8645’. Fortinet’s FortiGate products are often used to secure remote corporate networks with very strict access restrictions. Recently, FortiGate units running management interface with CVE-2018-8645 security issue were officially certified by Forti.
Remote Code Execution Vulnerability - CVE-2016-3547
FortiGate units running management interface with CVE-2016-3547 security issue were officially certified by Forti on January 12th, 2017.
The vulnerability is caused by a flaw in the way that Fortinet's FortiGate products handle certain requests to execute a specific remote command. The update fixes an issue where administrative users are able to execute arbitrary commands via the web management interface or CLI.
To fix this vulnerability, the latest firmware version for affected customers is 3.2.6 and newer, which was released on May 23rd, 2018.
Technical Overview
As a part of the FortiGate product, FortiSOAR is enabled to provide administrators with a flexible and powerful management interface. The vulnerability was found by an external researcher in FortiGate units running management interface with CVE-2018-8645 security issue. This vulnerability allows attackers to exploit the remote administration console and execute volatile commands on vulnerable devices
To raise awareness about this vulnerability and other security issues, Fortinet is releasing a product update to address these issues.
# Actions for Users
Users are advised to apply the recommended patch as soon as possible.
Description
Many organizations use Fortinet’s FortiGate firewall appliances, which are used to secure remote corporate networks with very strict access restrictions. Recently, it was discovered that Fortinet’s FortiGate units running the management interface were exposed to an input validation vulnerability in their REST APIs. This vulnerability is often referred to as “FortiSOAR Management Interface Remote Code Execution Vulnerability” and has been assigned Common Vulnerability and Exposure number ‘CVE-2018-8645’. This vulnerability allows attackers to take over a FortiGate appliance by sending specially crafted network traffic.
Summary of FortiGate units certified with CVE-2018-8645 security issue
FortiGate units certified with the CVE-2018-8645 security issue include:
* FortiGates running firmware version 2.6.0 to 2.7.14.0, and
* FortiGates running firmware version 3.2.0 or higher, but earlier than 3.4.1 with management interface enabled
This vulnerability is often referred to as “FortiSOAR Management Interface Remote Code Execution Vulnerability” and has been assigned Common Vulnerability and Exposure number ‘CVE-2018-8645’. Fortinet’s FortiGate products are often used to secure remote corporate networks with very strict access restrictions. Recently, FortiGate units running management interface with CVE-2018-8645 security issue were officially certified by Forti.
Overview:
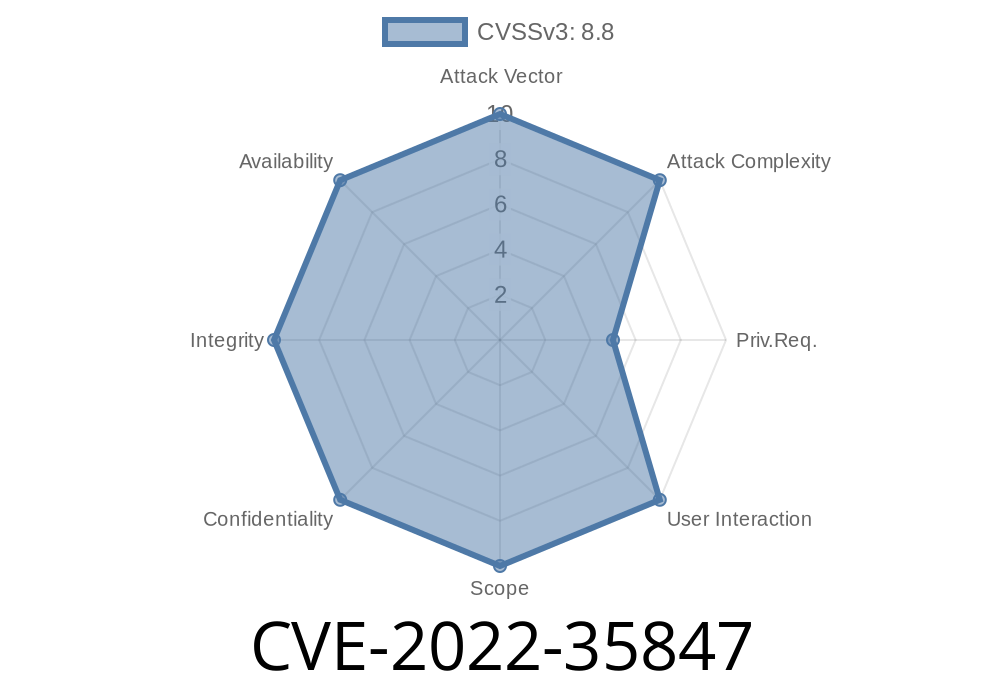
What is CVE-2022-35847
The vulnerability allows an attacker to remotely execute arbitrary code on FortiGate units by exploiting an issue in the management interface. The vulnerability has been assigned Common Vulnerability and Exposure number CVE-2018-8645.
This vulnerability impacts the following products:
FortiGate 100D, FortiGate 200D, FortiGate 300D, FortiGate 400D, FortiGate 500D, and FortiGate 600D.
Timeline
Published on: 09/06/2022 18:15:00 UTC
Last modified on: 09/09/2022 02:35:00 UTC