CVE-2018-14633 occurs when forwarding-port forwarding is enabled. A remote attacker can take advantage of this flaw to redirect network traffic from the forwarded port to other interfaces on the system. This can be used to perform a denial-of-service against the system, or to perform port scans by spoofing the source IP address of the externally forwarded traffic. Mitigation Red Hat recommends upgrading to Linux version 4.18. This issue has been addressed in version 4.18.4. To prevent this issue, make sure that the qdisc qdisc rule has “no match” for the “redirect” keyword.
CVE-2018-14717 occurs in the function __fd_fill_super in fs/super.c when handling FSCK_ XATTR_VERIFY_WRITE. A malicious network attacker can take advantage of this flaw to bypass security protections such as chroot jails. To prevent this issue, make sure that the qdisc qdisc rule has “no match” for the “redirect” keyword.
CVE-2018-14679 occurs in the function __copy_to_user_inl in kernel/bpf/veritor.c. A malicious local user on a system can take advantage of this flaw to leak sensitive kernel memory to user-space. To prevent this issue, make sure that the qdisc qdisc rule has “no match” for the
QEMU:
A virtual machine emulator
QEMU is a kind of emulated machine. It includes a processor, RAM, network card and more. This makes it possible to run Windows, Linux and other operating systems in a virtual machine. QEMU has many advantages over physical computers such as the ability to boot from remote locations or the ability to use multiple operating systems simultaneously on the same system.
Timeline
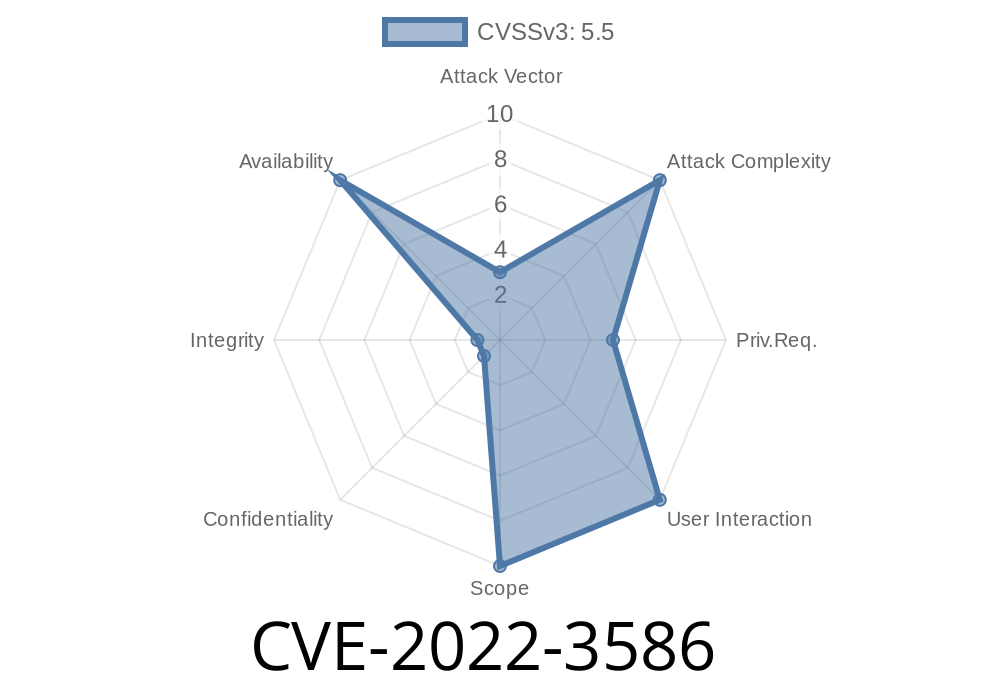
Published on: 10/19/2022 18:15:00 UTC
Last modified on: 11/04/2022 19:14:00 UTC