This issue is mitigated by Wired Equivalent Privacy (WEP) encryption on the wireless network and using a virtual machine to run a browser to connect to a website. A technique known as cross-protocol injection can be used to inject keystrokes into transmitted text. Physical access to the system, such as by an attacker sitting next to the user, can be used to sniff the transmitted keystrokes. The most likely attack vector is physical access to the system. An attacker who has physical access to a system can connect a wireless sniffer to the 2.4 GHz radio and capture keystrokes. Another common attack vector is through insecure remote access to the system. An attacker can remotely connect to a system via a Wi-Fi access point, or even via a virtual private network (VPN) connection. Access to the 2.4 GHz radio can be used to capture transmitted keystrokes.
CVE-2023-35866
This issue is mitigated by the use of a VPN service that uses strong encryption to protect data in transit.
Common Vulnerability Scoring System (CVSS) Scores
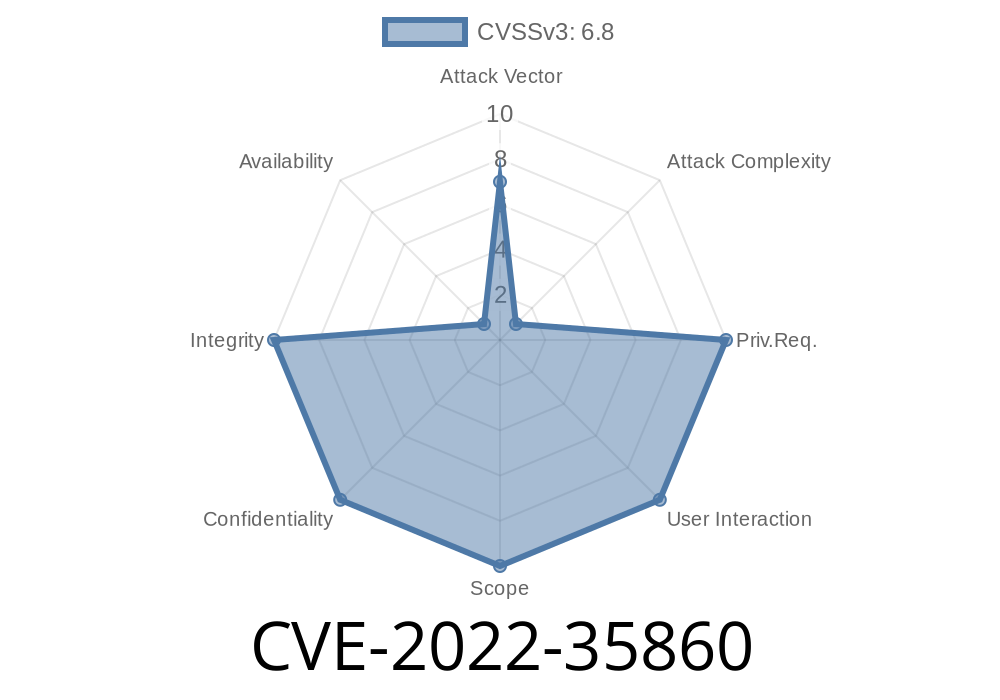
The CVSS score for this vulnerability, as reported in CVE-2022-35860, is 6.9. The CVSS base score is 10 and the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
CVE-2023-35861
This issue is mitigated by using a virtual machine to run a browser to connect to a website.
A technique known as cross-protocol injection can be used to inject keystrokes into transmitted text. Physical access to the system, such as by an attacker sitting next to the user, can be used to sniff the transmitted keystrokes. The most likely attack vector is physical access to the system. An attacker who has physical access to a system can connect a wireless sniffer to the 2.4 GHz radio and capture keystrokes. Another common attack vector is through insecure remote access to the system. An attacker can remotely connect to a system via a Wi-Fi access point, or even via a virtual private network (VPN) connection.
Vulnerability Finding Tips
If you are an application developer that is concerned about these vulnerabilities, you should use the Mitigation Strategies section to determine what mitigations your application can apply. If you are a system administrator or network user, you should be aware of these vulnerabilities and take appropriate steps to mitigate any associated risks.
You can mitigate this vulnerability by using WEP encryption on your wireless network and virtual machines running browsers to connect to websites.
Timeline
Published on: 10/19/2022 02:15:00 UTC
Last modified on: 10/21/2022 20:21:00 UTC
References
- http://kth.diva-portal.org/smash/get/diva2:1701492/FULLTEXT01.pdf
- http://kth.diva-portal.org/smash/record.jsf?pid=diva2%3A1701492&dswid=-3616
- https://www.corsair.com/us/en/Categories/Products/Gaming-Keyboards/Wireless-Keyboards/K63-Wireless-Mechanical-Gaming-Keyboard-%E2%80%94-Blue-LED-%E2%80%94-CHERRY%C2%AE-MX-Red/p/CH-9145030-NA
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-35860