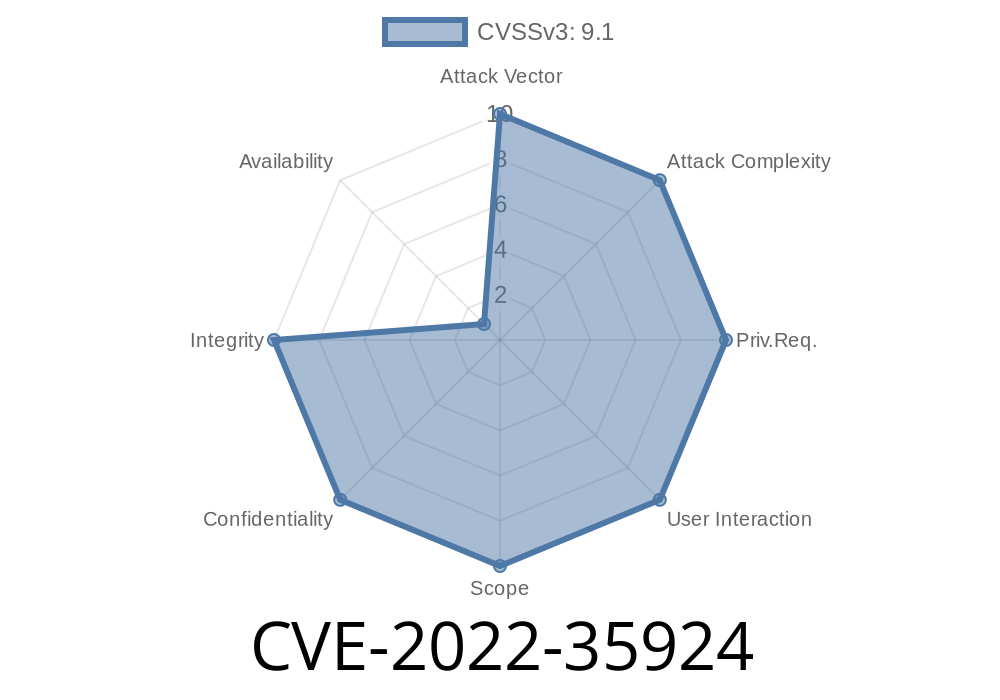
This update has been released to ensure users of Next.js apps using `EmailProvider` do not fall victim to this security flaw. ## On March 23rd 2018 the Next.js team published an update for their authentication library to protect users against a malicious attacker. NextAuth.js is an open source authentication library for Next.js applications that can be used with a variety of sign-in providers. A security patch was applied to the NextAuth.js library to protect users against a malicious attacker. This update was released after it was discovered that an attacker could forge a request to Next.js that caused NextAuth to send emails to an attacker and victim's email address. This could have had a very serious impact on Next.js users. You can read about the details of the vulnerability here: https://nextjs.org/blog/2018/3/23/next-auth-vulnerability/
How to check if you are affected by this vulnerability?
The vulnerability was released on March 23rd and it has been fixed. To check if you are currently affected, use the following command:
node --version
Next.js versions 1.0.0 to 1.9.2 have been patched for this vulnerability, meaning that you will not be affected by this issue anymore if you are using one of these versions of Next.js. There is no patch available for any version of Next.js before v1.0.0 and the vulnerability is not present in v1.0.x because all calls to `EmailProvider` were deprecated in v1.0.x releases.
What does this update protect against?
The vulnerability allowed a malicious attacker to send emails to the victim's email address and Next.js's email address, creating an opportunity for the attacker to gain access to users' private information.
What do I need to do after updating?
After updating your app, you will need to add `email` to your `providers` object in your application's config.json file. You will also need to change the default email provider from `EmailProvider` to one of the other providers that matches the spec of the patch.
How to check if you are affected by the vulnerability?
If you are using the version of NextAuth.js that is affected by this vulnerability, you must update your app in order to protect yourself. To check if your app is affected and needs to be updated follow these steps:
1. Open the console on your application and type `app.versions.versions`
2. If you have an older version of NextAuth, like before v2.0-beta-28, then your app is not affected by this vulnerability.
Timeline
Published on: 08/02/2022 18:15:00 UTC
Last modified on: 08/10/2022 14:56:00 UTC
References
- https://next-auth.js.org/configuration/callbacks#sign-in-callback
- https://github.com/nextauthjs/next-auth/security/advisories/GHSA-xv97-c62v-4587
- https://en.wikipedia.org/wiki/Email_address#Local-part
- https://next-auth.js.org/providers/email#normalizing-the-e-mail-address
- https://next-auth.js.org/providers/email
- https://github.com/nextauthjs/next-auth/commit/afb1fcdae3cc30445038ef588e491d139b916003
- https://next-auth.js.org/configuration/initialization#advanced-initialization
- https://nodemailer.com/message/addresses
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-35924