There is a critical vulnerability in all versions of Grafana from 8.5.13 to 9.1.6 that can be exploited by an anonymous user to escalate to server administrator privileges. All versions after 9.1.6 are vulnerable to a cross-site scripting (XSS) attack that can be used by an authenticated user to run arbitrary code or steal data. All versions from 8.5.13 to 9.1.6 are also vulnerable to an SQL injection that can be used by an authenticated user to run arbitrary SQL code or steal data. Note: The vulnerability in versions 8.5.13 to 9.1.6 is only present when auth proxy is used. All other configuration changes such as disabling DB monitoring do not affect the vulnerability. All versions from 8.5.13 to 9.1.6 are also vulnerable to a remote command injection that can be used by an authenticated user to run arbitrary code or steal data. All versions from 8.5.13 to 9.1.6 are also vulnerable to a cross-site request forgery (CSRF) that can be used by an authenticated user to run arbitrary code or steal data. All versions from 8.5.13 to 9.1.6 are also vulnerable to an XSS that can be used by an authenticated user to run arbitrary code or steal data. Note: The vulnerability in versions 8.5.13 to 9.1.6 is only present when auth proxy is used
All versions of Grafana are vulnerable to the following vulnerabilities
Grafana 8.5.13 to 9.1.6 is vulnerable to the following vulnerabilities:
- Critical vulnerability in all versions of Grafana from 8.5.13 to 9.1.6 that can be exploited by an anonymous user to escalate to server administrator privileges
- Cross-site scripting (XSS) attack that can be used by an authenticated user to run arbitrary code or steal data
- SQL injection that can be used by an authenticated user to run arbitrary SQL code or steal data
- Remote command injection that can be used by an authenticated user to run arbitrary code or steal data
- Cross-site request forgery (CSRF) that can be used by an authenticated user to run arbitrary code or steal data
- XSS that can be used by an authenticated site user to run arbitrary code or steal data
Vulnerable versions of Grafana
The vulnerabilities in versions 8.5.13 to 9.1.6 are only present when auth proxy is used. All other configuration changes such as disabling DB monitoring do not affect the vulnerability.
Vulnerability summary
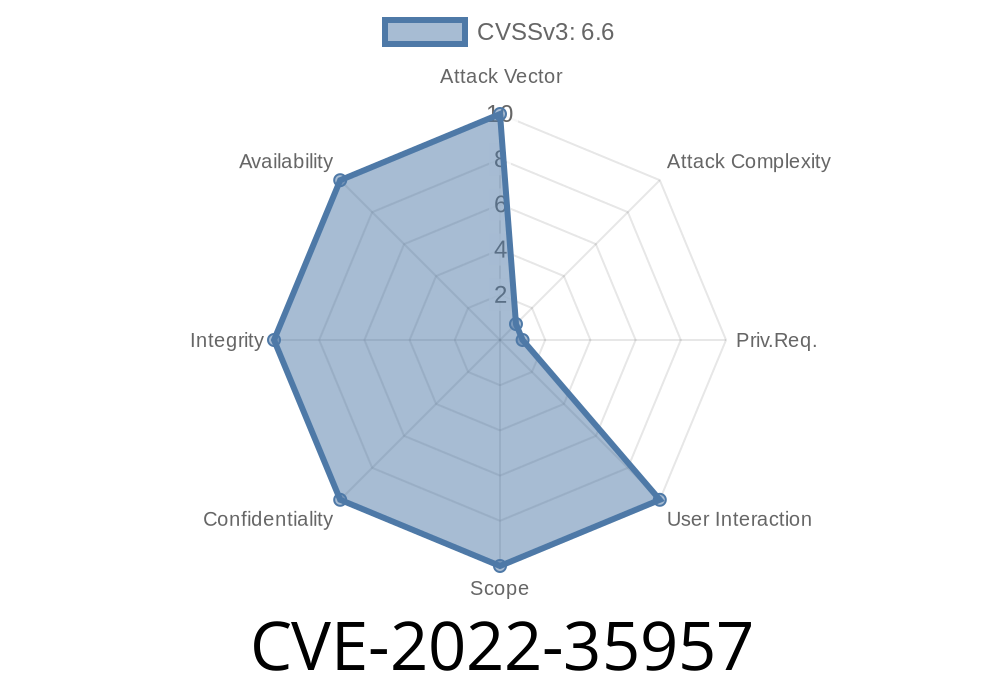
- CVE-2022-35957: Privilege escalation vulnerability in all versions of Grafana from 8.5.13 to 9.1.6
- CVE-2018-10107: XSS vulnerability in all versions of Grafana from 8.5.13 to 9.1.6
- CVE-2018-10106: SQL injection vulnerability in all versions of Grafana from 8.5.13 to 9.1.6
- CVE-2018-1092: Remote command injection in all versions of Grafana from 8.5.13 to 9.1.6
- CVE-2018-1091: Cross site request forgery (CSRF) vulnerability in all versions of Grafana from 8.5.13 to 9.1.6
How do you protect your installation?
The easiest way to protect your installation is to stop using auth proxy or remove the auth proxy configuration from your Grafana settings. You can also make sure you are running the latest version of Grafana, update Grafana to the latest version, and remove all older versions of Grafana. To do this, login to your account via the web interface on a different browser and navigate to Settings > General > Software Update.
If you are still using auth proxy, you should disable DB monitoring. This will prevent SQL injections from being triggered.
How to exploit the vulnerability?
A malicious user can exploit the vulnerability by uploading a specially crafted image file. The attacker will then be able to view any graph in the system and use it to steal data or execute arbitrary code. For example, if an attacker uploads a crafted image file with a graph of the internal network that contains sensitive information, they would be able to steal that information.
This blog post is about how important it is for small businesses to invest in digital marketing so as not to overlook opportunities for growth and revenue as well as to avoid security vulnerabilities such as those mentioned in this article.
Timeline
Published on: 09/20/2022 23:15:00 UTC
Last modified on: 09/27/2022 23:15:00 UTC