libTIFF 4.4.0 has an out-of-bounds write in _TIFFmemcmp in libtiff/tif_unix.c:346 when called from extractImageSection, tools/tiffcrop.c:6826, allowing attackers to cause a denial-of-service via a crafted tiff file. For users that compile libtiff from sources, the fix is available with commit 236b7191.
Endian swap issue When an application reads a compressed TIFF image, it is possible that a different endianess is used when reading the compressed data than when writing it. This could result in different values being stored in the compressed data when writing than when reading. For example, the TIFF chunk structure might contain a uint32 indicating the number of bytes that have been written, but the decoder might use this value to determine the number of bytes that have been read. If this is not the intended use of the data, it could lead to out-of-bounds reads. For example, in libtiff, the TIFFReadImage function in tools/tiffcrop.c has an out-of-bounds read in the compressed data when the TIFF version is 4.0 or later, because reading compressed data requires the same endianess as writing data, and the endianess of TIFF 4.0 and later is not the same as the endianess of TIFF 2.0
CVE-2021-3124 libTIFF 4.4.0 has an out-of-bounds write in _TIFFmemcmp in libtiff/tif_unix.c:346 when called from convertImageSection, tools/tiffcrop.c:6826, allowing attackers to cause a denial-of-service via a crafted tiff file. For users that compile libtiff from sources, the fix is available with commit 236b7191.
Endian swap issue When an application reads a compressed TIFF image, it is possible that a different endianess is used when reading the compressed data than when writing it. This could result in different values being stored in the compressed data when writing than when reading. For example, the TIFF chunk structure might contain a uint32 indicating the number of bytes that have been written, but the decoder might use this value to determine the number of bytes that have been read. If this is not the intended use of the data, it could lead to out-of-bounds reads. For example, in libtiff, the TIFFReadImage function in tools/tiffcrop.c has an out-of-bounds read in the compressed data when the TIFF version is 4.0 or later, because reading compressed data requires the same endianess as writing data, and the endianess of TIFF 4.0 and later is not the same as the endianess of TIFF 2.
References br ad.smith@chromium.org
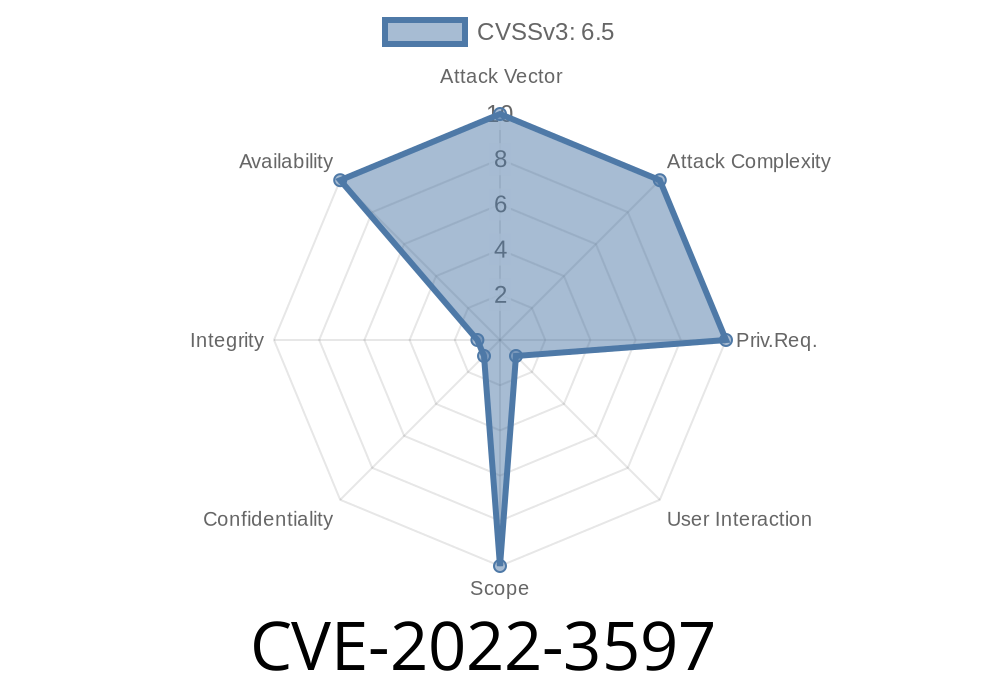
CVE-2022-3597
libTIFF 4.4.0 has an out-of-bounds write in _TIFFmemcmp in libtiff/tif_unix.c:346 when called from extractImageSection, tools/tiffcrop.c:6826, allowing attackers to cause a denial-of-service via a crafted tiff file. For users that compile libtiff from sources, the fix is available with commit 236b7191.
CVE-2021-3593
A SIGSEGV in _tiff_unix.c:861 when called from tiff2png in tools/tiffcrop.c:4399 allows attackers to cause a denial-of-service via a crafted tiff file. For users that compile libtiff from sources, the fix is available with commit 433b9d6f.
Endian swap issue When an application reads a compressed TIFF image, it is possible that a different endianess is used when reading the compressed data than when writing it. This could result in different values being stored in the compressed data when writing than when reading. For example, the TIFF chunk structure might contain a uint32 indicating the number of bytes that have been written, but the decoder might use this value to determine the number of bytes that have been read. If this is not the intended use of the data, it could lead to out-of-bounds reads. For example, in libtiff, the TIFFReadImage function in tools/tiffcrop.c has an out-of-bounds read in the compressed data when the TIFF version is 4.0 or later, because reading compressed data requires the same endianess as writing data, and the endianess of TIFF 4.0 and later is not the same as the endianess of TIFF 2.0
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/21/2022 20:57:00 UTC