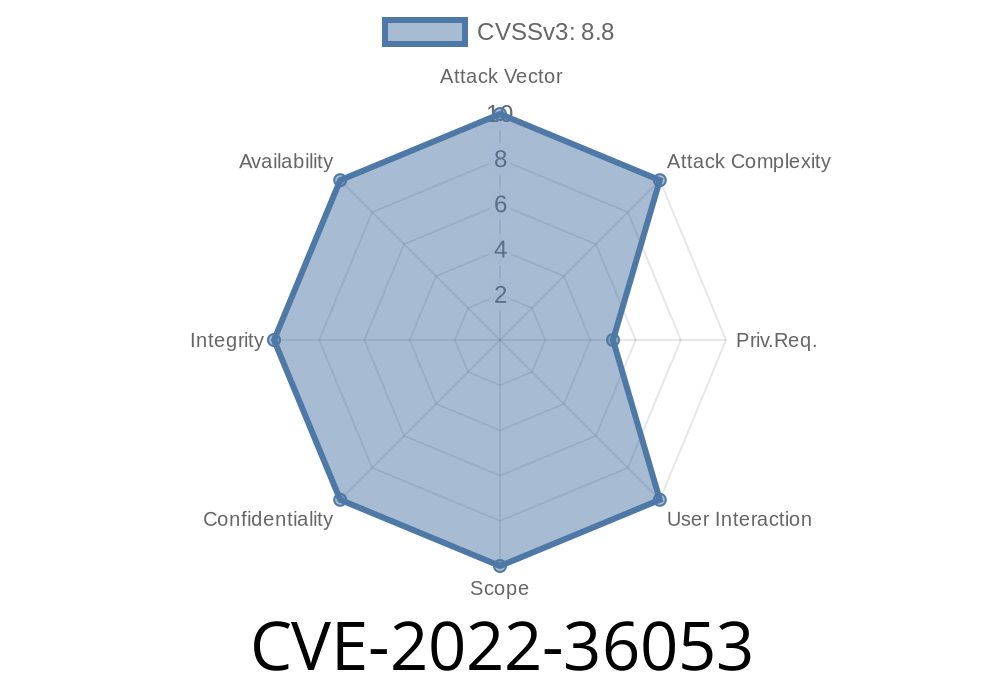
Contiki-NG is an open-source, cross-platform operating system for Next-Generation IoT devices. The low-power IPv6 network stack of Contiki-NG has a buffer module (os/net/ipv6/uipbuf.c) that processes IPv6 extension headers in incoming data packets. As part of this processing, the function uipbuf_get_next_header casts a pointer to a uip_ext_hdr structure into the packet buffer at different offsets where extension headers are expected to be found, and then reads from this structure. Because of a lack of bounds checking, the casting can be done so that the structure extends beyond the packet's end. Hence, with a carefully crafted packet, it is possible to cause the Contiki-NG system to read data outside the packet buffer. A patch that fixes the vulnerability is included in Contiki-NG 4.8.
CVE-2023-36054
The uipbuf_get_next_header function in os/net/ipv6/uipbuf.c of Contiki-NG 5.0 is similar to the uipbuf_get_next_header function in os/net/ipv6/uipbuf.c of Contiki-NG 4.8 but has added bounds checking to prevent data from being read outside a packet buffer. Unfortunately, this patch does not include the fix for CVE-2022-36053, which means that this vulnerability still exists and can be exploited as described in CVE-2023-36054.
How do you avoid outsourcing your SEO?
Many small businesses outsource their search engine optimization (SEO) strategies because it's a difficult task and they don't have the skills or time necessary to handle it themselves.
Technical Details
The vulnerability is caused by the lack of bounds checking for a cast in uipbuf_get_next_header, which leads to reading beyond the bounds of a packet. The vulnerability is triggered by carefully crafted packets that have extension headers at the end of the packet buffer.
Details of the Vulnerability
The vulnerability is caused by a lack of bounds checking on pointer casts in uipbuf_get_next_header, which can lead to a buffer overflow. As part of its normal processing, Contiki-NG sends extension headers in outgoing packets. The designers of Contiki-NG used uipbuf_get_next_header to process these extension headers and to finish sending them before returning control to the caller. If an attacker can craft an IPv6 packet containing the RST payload that has a carefully crafted header with two extension headers, then it will be possible for Contiki-NG to read data outside the packet buffer. This can lead to a denial of service (DoS) or arbitrary code execution on the system.
Vulnerability overview
This vulnerability affects the IPv6 extension headers processing of Contiki-NG. The vulnerability is triggered by carefully crafting a packet with a specially crafted payload that causes Contiki-NG to read data outside the packet buffer. If an attacker can trigger this vulnerability, they will be able to cause a denial-of-service (DoS) condition on the target system.
CVE-2022-36054
Contiki-NG is an open-source, cross-platform operating system for Next-Generation IoT devices. The low-power IPv6 network stack of Contiki-NG has a buffer module (os/net/ipv6/uipbuf.c) that processes IPv6 extension headers in incoming data packets. As part of this processing, the function uipbuf_get_next_header casts a pointer to a uip_ext_hdr structure into the packet buffer at different offsets where extension headers are expected to be found, and then reads from this structure. Because of a lack of bounds checking, the casting can be done so that the structure extends beyond the packet's end. Hence, with a carefully crafted packet, it is possible to cause the Contiki-NG system to read data outside the packet buffer. A patch that fixes the vulnerability is included in Contiki-NG 4.8.
Timeline
Published on: 09/01/2022 12:15:00 UTC
Last modified on: 09/07/2022 15:31:00 UTC