Matrix is an open standard for secure, decentralized, real-time communication. If you use Element or other web Matrix chat clients, you’re probably relying on matrix-react-sdk under the hood.
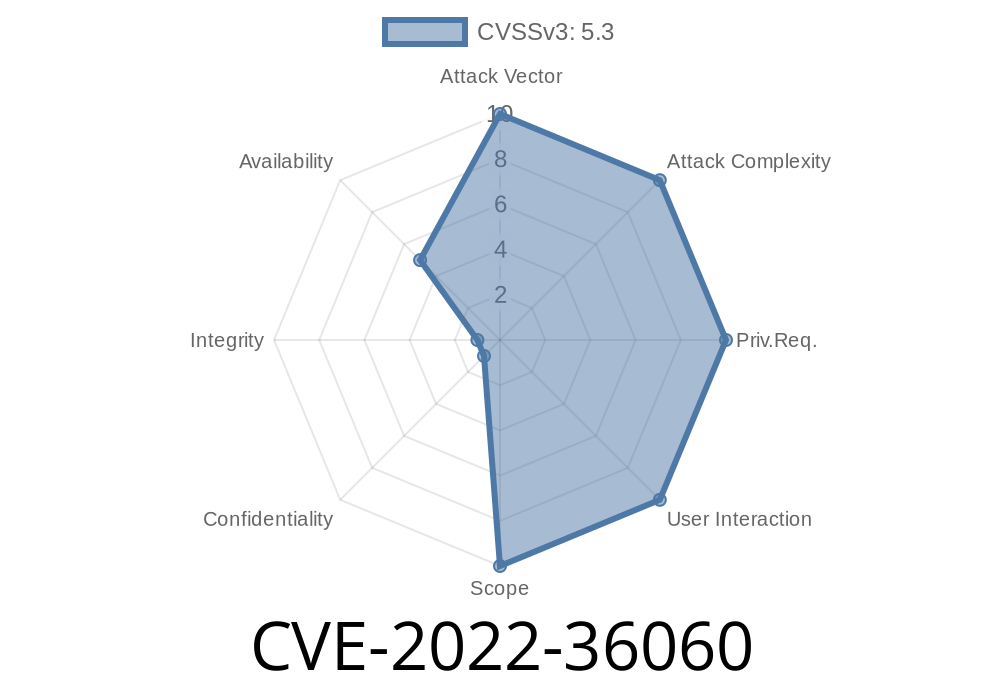
But in August 2022, a critical vulnerability was found: CVE-2022-36060. With a very specific kind of message, attackers could silently cripple individual Matrix rooms, leaving users unable to see messages, join discussions, or even load affected chat threads. The rest of the app looked fine—but some rooms were dead.
Here’s a simple explainer (with code!) of what went wrong, how it was fixed, and why it mattered.
What is matrix-react-sdk?
matrix-react-sdk is a set of JavaScript tools and React components for building Matrix chat web apps—like the official Element client. It “renders” rooms, conversations, messages, and events that come from the Matrix protocol.
These messages (“events”) arrive as JSON blobs from the server and can include user messages, state changes, files, invites... and more.
The Vulnerability: Strings That Crash Chat Rooms
matrix-react-sdk wasn't always careful handling certain incoming messages. If an attacker crafted a room message or event with strange or “malformed” string data in specific fields (such as out-of-bounds Unicode, or deeply nested objects where strings were expected), it would cause unhandled JavaScript exceptions during rendering.
When any user’s web client tried to show the poisoned message, parts of the UI (mainly the affected room’s timeline or event tile) would crash. The whole app wasn't completely down—but the infected room might be impossible to use.
Example of a Malicious Event
Let’s say an attacker injects the following event into a public Matrix room using the low-level Matrix API or a custom bot:
{
"type": "m.room.message",
"content": {
"msgtype": "m.text",
"body": "\udc80" // Invalid Unicode string (lone surrogate)
},
"sender": "@attacker:example.org",
"room_id": "!roomid:example.org"
}
This message contains an *invalid* Unicode character. When matrix-react-sdk tries to render this message as a React component, it may trigger errors such as:
// Simplified pseudo-code
function renderMessage(event) {
return <span>{event.content.body}</span>; // May throw if body has bad string
}
If this body field isn’t sanitized, an exception like URIError: URI malformed might result, which can break the rendering of the timeline or the entire room.
Other rooms and parts of the app still work (unless also infected).
- The vulnerability could be used for simple denial of service (DoS) in open/public chat rooms.
There's no workaround except deleting the offending event—which is *not* possible in Matrix if someone else sends it.
No Workarounds
The maintainers confirmed:
> There are no known workarounds for this vulnerability.
(Reference)
Fix Details
The fix (merged in PR #8597) was to harden all React components and event handling so that any untrusted string or event cannot crash the UI. This included things like:
Using “error boundaries” in React to catch exceptions.
Patched version: matrix-react-sdk 3.53.
Release note:
> “Malformed event data will no longer crash room timelines. Clients are advised to upgrade as soon as possible.”
How to Protect Yourself
- Upgrade! If you run a Matrix client based on matrix-react-sdk (e.g. custom forks, self-hosted Element Web), update to 3.53. or later.
If you run a public Matrix instance, alert your users or upgrade your web clients.
- There is *no way* to sanitize incoming events at the server/proxy layer (events are encrypted end-to-end).
Technical References
- Original security advisory
- matrix-react-sdk v3.53. changelog
- Fix PR #8597
- Matrix.org Home
Summary
CVE-2022-36060 was a subtle but serious bug: a single malformed message could knock out whole chat rooms in popular Matrix web apps. This is a reminder: always sanitize and validate what you show your UI!
If you operate a chat system or fork Element Web, make sure you’re not vulnerable—and encourage your users to update. This was caught in time, but similar vulnerabilities can lurk in many chat applications. Stay safe and keep your apps up to date!
*Want to see more technical writeups like this? Leave a message below!*
Timeline
Published on: 03/28/2023 21:15:00 UTC
Last modified on: 04/05/2023 00:15:00 UTC