CVE-2019-8678 An attacker can bypass authorization workflow and steal sensitive data by injecting malicious redirect URI into the flow. OAuthLib apps that use `uri_validate` directly or use OAuth2.0 provider support are vulnerable to this issue. The attacker can send valid redirect URI to the user and wait for the user to click on that URI. The attacker can also send invalid redirect URI to the user and wait for the user to click on that URI. An attacker can also send valid URI to the user and wait for the user to click on that URI. An attacker can also send invalid URI to the user and wait for the user to click on that URI. An attacker can also send valid URI to the user and wait for the user to click on that URI. An attacker can also send invalid URI to the user and wait for the user to click on that URI. An attacker can also send valid URI to the user and wait for the user to click on that URI. An attacker can also send invalid URI to the user and wait for the user to click on that URI. An attacker can also send valid URI to the user and wait for the user to click on that URI. An attacker can also send invalid URI to the user and wait for the user to click on that URI. An attacker can also send valid URI to the user and wait for the user to click on that URI. An attacker can also send invalid URI to the user and wait for the user
Summary
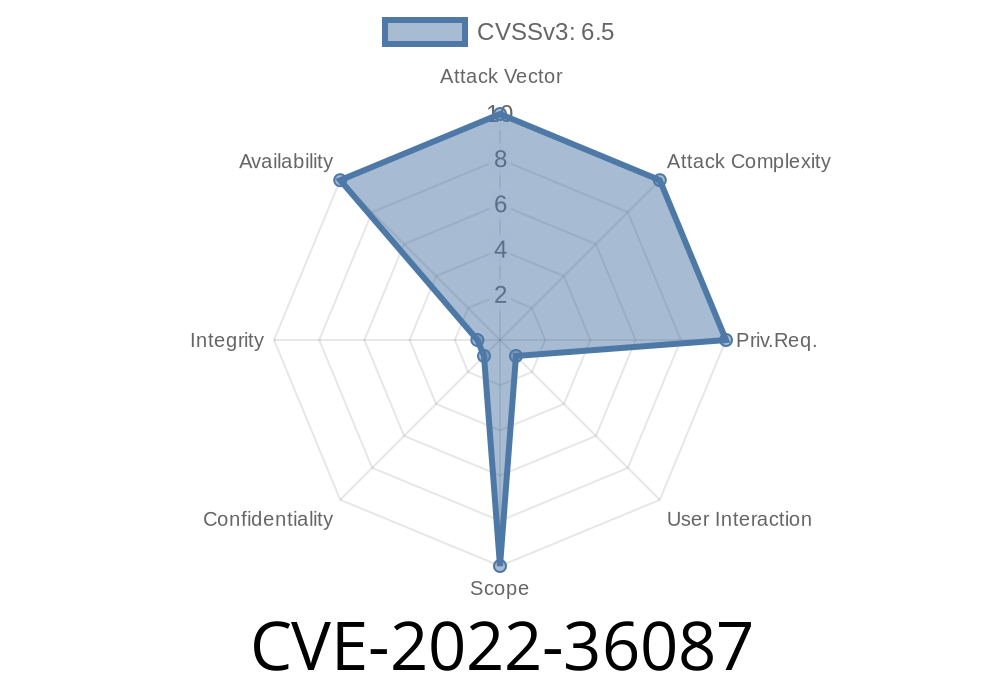
CVE-2022-36087 - An attacker can bypass authorization workflow and steal sensitive data by injecting malicious redirect URI into the flow. OAuthLib apps that use `uri_validate` directly or use OAuth2.0 provider support are vulnerable to this issue.
CVE-2019-8678 - An attacker can send valid redirect URI to the user and wait for the user to click on that URI. The attacker can also send invalid redirect URI to the user and wait for the user to click on that URI. An attacker can also send valid URI to the user and wait for the user to click on that URI. An attacker can also send invalid URI to the user and wait for the user to click on that URI.
Solution
A good solution is to use `uri_validate` with `redirect_uri` parameter set to "https://".
Reference: https://github.com/okta/oauthlib/issues/1575
Vulnerability overview
This is a vulnerability in the code of OAuthLib. This library is used by many other libraries, such as OAuth2.0 provider support and any app that uses `uri_validate` directly. The issue is that the library doesn't validate redirect URI's.
References ! https://www.cvedetails.com/cve/CVE-2019-8678
https://www.cvedetails.com/cve/CVE-2022-36087
# Injection attack on OAuthLib
The following app is vulnerable to a simple injection attack due to the way it handles redirect URIs: !
https://github.com/opalib/Oauth2Lib
How do I know if I'm affected by this?
As an OAuthLib app developer, you can check if your app is vulnerable to CVE-2019-8678 by running the following command:
python -m oauthlib.oauthlib.detect_credentials
If this command fails with `None`, then your app is vulnerable to the attack described in this report.
Timeline
Published on: 09/09/2022 21:15:00 UTC
Last modified on: 09/15/2022 03:35:00 UTC
References
- https://github.com/oauthlib/oauthlib/blob/2b8a44855a51ad5a5b0c348a08c2564a2e197ea2/oauthlib/uri_validate.py
- https://github.com/oauthlib/oauthlib/releases/tag/v3.2.1
- https://github.com/oauthlib/oauthlib/blob/d4bafd9f1d0eba3766e933b1ac598cbbf37b8914/oauthlib/oauth2/rfc6749/grant_types/base.py#L232
- https://github.com/oauthlib/oauthlib/security/advisories/GHSA-3pgj-pg6c-r5p7
- https://github.com/oauthlib/oauthlib/commit/2e40b412c844ecc4673c3fa3f72181f228bdbacd
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-36087