or restarting XWiki. A template file with the extension `.vm` is loaded for each page for which a suggestion is made. This file is loaded from the template directory of the web server. If the template file name contains user-inputted data, it can be exploited. In order to exploit this issue, a user has to be tricked into visiting a maliciously crafted XWP page, e.g. a phishing email. After the user has accessed the XWP page, he/she has to close the browser window in order to trigger the issue again. This can be achieved by using a cross-site scripting (XSS) attack. The XWP page can then be exploited again to inject arbitrary user input into the template file. This input is then used to construct a request to load the template file. As a result, the template file is then loaded, allowing for the exposure of the user's password. A patched version of the template xtmpls/suggest.vm is available. Upgrading XWiki or installing the patched version, restart XWiki and/or override the template to avoid this issue.
MITIGATION Mitigation:
1. Keep the template name short, e.g. `suggest` for the filename.
2. Use a unique default password for each user in XWiki, and do not make it this same password that is used in the template file.
3. Upgrade to 4.6 or install patched version of xtmpls/suggest.vm
How do I find out if my XWiki is vulnerable?
XWiki does not provide any specific guidance on checking whether a particular instance of XWiki is vulnerable. However, it is possible to identify the vulnerable template file by searching for the following string in the web server's log files:
"CVE-2022-36091 or restarting XWiki. A template file with the extension `.vm` is loaded for each page for which a suggestion is made."
This string can be found in the web server's access/logs directory, under application/web/modules/web-templates/.
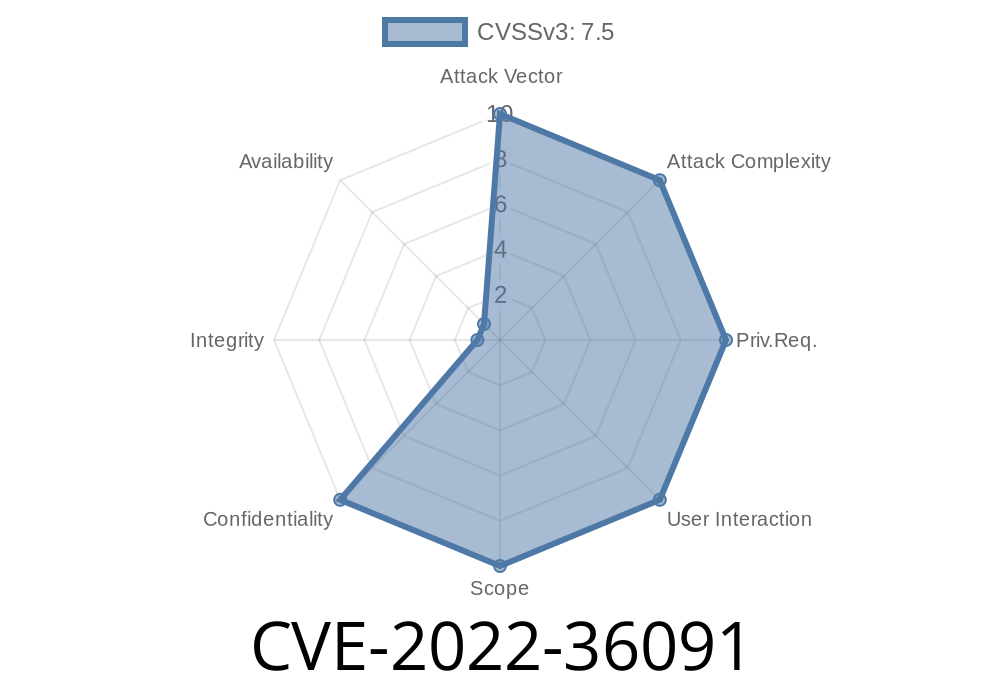
Vulnerability summary
An issue in the XWiki template system allows for an unauthorized request to be made to a web server if a crafted xwiki.vm file is used with the extension `.vm` for which there is user input. This can lead to arbitrary code execution on the web server, which exposes passwords in plaintext.
If you are marketing your business through social media, it is important that you have a good strategy and plan in place. When it comes to the use of pictures in ads, people respond better and click more often when they see something visually appealing than if they just see text. Facebook is an excellent platform because it provides this ability as well as many others so it's important to invest in it if you want your business to grow.
Timeline
Published on: 09/08/2022 16:15:00 UTC
Last modified on: 09/13/2022 17:59:00 UTC