To exploit this issue, an attacker must have permissions to the UpdateOfflineHelpData administrative function and must know and have access to the URL that a Blue Prism user would access to view the online help.
There are two ways this issue can be exploited:
1. By manipulating the Blue Prism user interface, allowing an attacker to change the offline help URL.
2. By directly manipulating the offline help data, allowing an attacker to change the offline help data. Either way, the attacker can now choose to host the offline help data on their own server, spoofing the help page to their liking.
CVE-2022-36122
To exploit this issue, an attacker must have permissions to the UpdateOfflineHelpData administrative function and must know and have access to the URL that a Blue Prism user would access to view the online help.
There are two ways this issue can be exploited:
1. By manipulating the Blue Prism user interface, allowing an attacker to change the offline help URL.
How does this issue occur?
The issue occurs because the URL for the offline help data is passed to (and stored at) an attacker who has permissions.
It is possible that by changing a non-important parameter in an update, the attacker can cause a problem with the offline help. For example, if this were the case, the attacker could change "http://mydomain.com/info/help/" to "http://evildomain.com/info/help/" without changing any other values and deceiving Blue Prism users into thinking they are viewing their own work product as opposed to a site they do not trust.
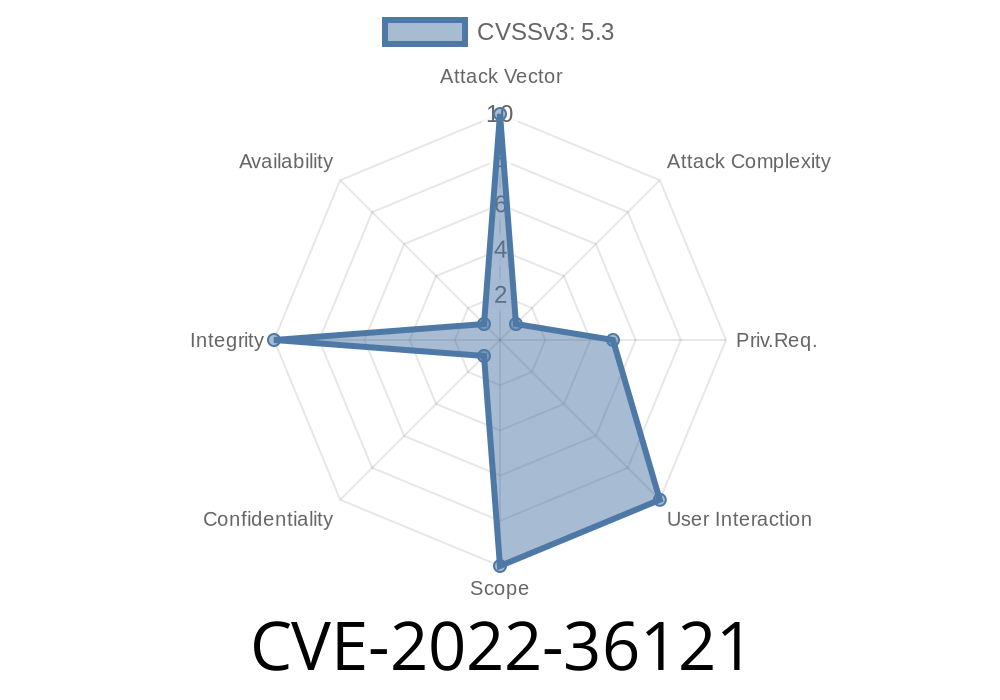
Vulnerability identifier CVE-2022-36121
How do I detect if my Blue Prism is vulnerable?
1. Check your online help URL. If you see a different URL, it is likely an attacker has manipulated the interface, allowing them to change the offline help URL.
2. Perform a local scan of your machine to detect if any files or folders have been changed. If any are found, it is likely that an attacker has manipulated the offline help data by directly manipulating the offline help data.
Timeline
Published on: 08/26/2022 00:15:00 UTC
Last modified on: 09/01/2022 18:33:00 UTC