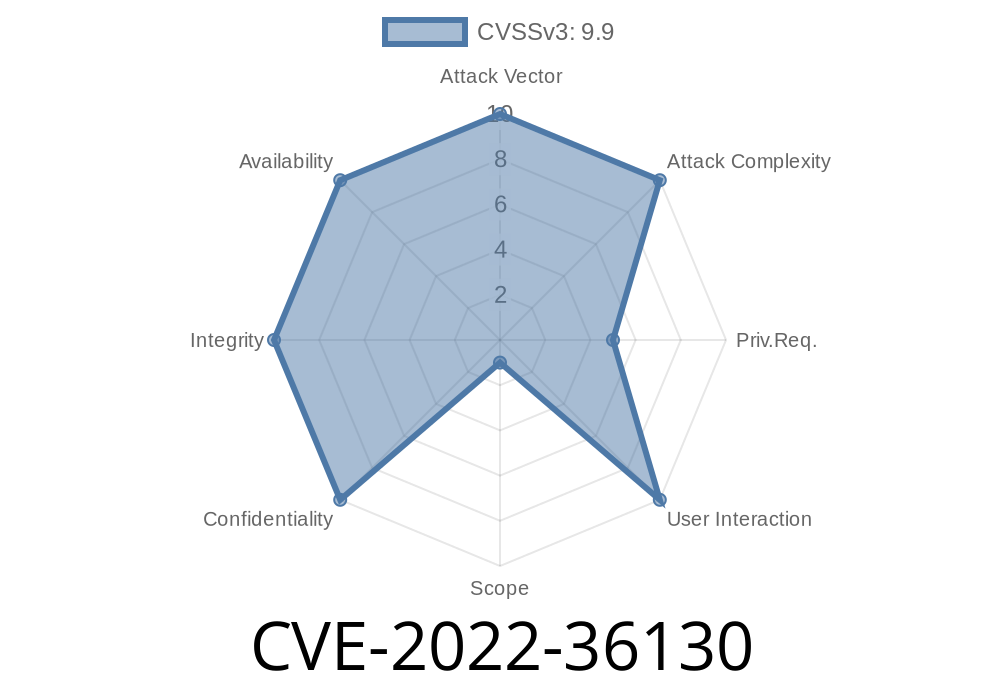
HashiCorp Boundary is a tool designed to help secure and control access to infrastructure components such as Kubernetes or OpenStack clouds, enabling organizations to enforce policies and limit access to third-party services through secure authentication and authorization. The risk with most security controls, of course, is that they can be misused or circumvented by malicious actors. In this case, the misusage was due to a security flaw that allowed Boundary administrators with a high enough privilege to push “boundary.nodes” scopes higher than the actual team or project where their nodes were located. This allowed Boundary administrators to associate their nodes with scopes other than the one they were actually assigned to, potentially allowing them to access nodes they were not authorized to. This vulnerability was fixed in Boundary 0.10.2. HashiCorp Boundary is a tool designed to help secure and control access to infrastructure components such as Kubernetes or OpenStack clouds, enabling organizations to enforce policies and limit access to third-party services through secure authentication and authorization. The risk with most security controls, of course, is that they can be misused or circumvented by malicious actors. In this case, the misusage was due to a security flaw that allowed Boundary administrators with a high enough privilege to push “boundary.nodes” scopes higher than the actual team or project where their nodes were located
Overview: Security Flaw in Boundary
One vulnerability that the project addressed in Boundary 0.10.2 was a security flaw that allowed Boundary administrators with a high enough privilege to push “boundary.nodes” scopes higher than the actual team or project where their nodes were located. This allowed Boundary administrators to associate their nodes with scopes other than the one they were actually assigned to, potentially allowing them to access nodes they were not authorized to.
Findings:
- Boundary administrators could push higher scopes than they were actually assigned to.
- This allowed them to effectively bypass the intended policy of the project they were attempting to access.
- This vulnerability was fixed in Boundary 0.10.2.
Background: How to Access a Node Without Authorization
A vulnerability was reported to HashiCorp on December 27th, 2018 in the Boundary software. The vulnerability allowed Boundary administrators with sufficient privileges to push “boundary.nodes” scopes higher than the actual team or project where their nodes were located. This allowed Boundary administrators to associate their nodes with scopes other than the one they were actually assigned to.
Overview of Boundary
HashiCorp Boundary is a tool designed to help secure and control access to infrastructure components such as Kubernetes or OpenStack clouds, enabling organizations to enforce policies and limit access to third-party services through secure authentication and authorization. The risk with most security controls, of course, is that they can be misused or circumvented by malicious actors. In this case, the misusage was due to a security flaw that allowed Boundary administrators with a high enough privilege to push “boundary.nodes” scopes higher than the actual team or project where their nodes were located.
Read more about Boundary and the vulnerability
If you are looking to learn more about this vulnerability and how it was fixed, please see the following blog post on HashiCorp's website: https://www.hashicorp.com/blog/2018-09-26/security-update-boundary
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
Timeline
Published on: 09/01/2022 02:15:00 UTC
Last modified on: 09/09/2022 14:17:00 UTC