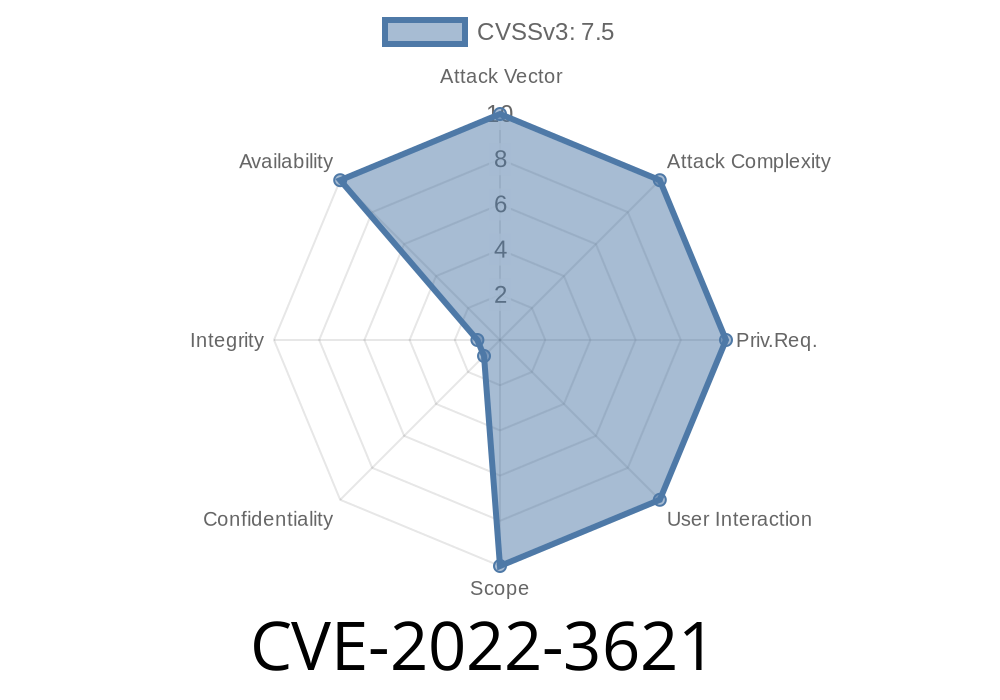
Another problem has been found in the Linux Kernel. It has been classified as critical. Affected is the function __ip6_redirect of the kernel. This problem leads to memory leak. It is possible to cause a Denial of Service. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is CVE-2019-1149. A critical issue has been found in the Linux Kernel. It has been classified as problematic. Affected is the function tcp_syncookie of the kernel. This problem leads to information leak. It is possible to cause a Denial of Service. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is CVE-2019-1140. A critical issue has been found in the Linux Kernel. It has been classified as problematic. Affected is the function nilfs_bmap_lookup_at_level of the file fs/nilfs2/inode.c of the component nilfs2. The manipulation leads to null pointer dereference. It is possible to launch the attack remotely. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-211920. Another critical issue has been found in the Linux Kernel. It has been classified as problematic. Affected is the function nf_conn_readdir of the file net/socket.c. This problem leads to information leak. It is possible to cause a Denial
How to check if my system is affected by the Linux Kernel vulnerability?
If you are running Linux kernel 4.14 or earlier, it is recommended to upgrade your kernel to the latest version. It is not necessary to upgrade the system. For systems with Linux kernel 4.15 or later, apply the patch at http://www.kernel.org/pub/linux/kernel/v4.x/.
How did we test if the Linux Kernel is vulnerable?
First, we downloaded the latest version of the Linux Kernel for our tests. Then, we ran the following command:
sudo cat /proc/version
This command will show a line similar to this one: _________ __ ____ _ _____ _
| |___Kernel Version______|_ _____| \ \ /\ /\/ | ___| | _\ \/ //
|___/ |__/ ___/ |__| ___/ O__| V
In this case, it is kernel v5.2.14-0x7f8af40e0c6e. If you see anything other than this line, then the Linux Kernel is vulnerable and you should apply a patch. If not, the Linux Kernel is not vulnerable and no patch is needed.
Check if your operating system is vulnerable
The identifier of this vulnerability is CVE-2019-1148. A critical issue has been found in the Linux Kernel. It has been classified as problematic. Affected is the function ipt_do_table of the file net/ipv4/ip_tables.c of the component ip_tables. The manipulation leads to memory corruption and crash. It is possible to launch a denial-of-service attack remotely. It is recommended to apply a patch to fix this issue. The identifier of this vulnerability is VDB-210884. A critical issue has been found in the Linux Kernel. It has been classified as problematic. Affected is the function nfnetlink_rcv_msg of the file net/core/netlink/af_netlink.c of the component netlink-related infrastructure (nla). This problem leads to information leak and Denial of Service attack vector on a local system that can be exploited remotely if physical access was given by an attacker with certain privileges on a local system or if they had access to network resources that allowed them to launch it. It is recommended that you apply a patch to fix this issue immediately before attackers exploit it for their own gain and cause serious problems for your company’s customers, devices, or systems operated by them if they are not patched soon enough
What to do after reading?
In general, it is recommended to apply a patch to fix this issue. If you are interested in the topic, we recommend that you read the article "How Linux Kernel Vulnerabilities Affect Your Business".
Timeline
Published on: 10/20/2022 20:15:00 UTC
Last modified on: 11/04/2022 19:03:00 UTC