libtiff is used by many applications and libraries, such as Python, Go, Firefox, and Qt. As such, users that rely on the integrity of libtiff should upgrade as soon as possible. End users who are concerned about the integrity of their system can run the provided script that detects vulnerable packages and attempts to install a patched version.
Potential Impact of A Vulnerability
The vulnerability is found in the libtiff library and can lead to remote code execution on systems. Applications that use libtiff might be vulnerable and could be exploited. For example, if an attacker sends a maliciously crafted email with an attachment containing a TIFF file to a victim, they could execute arbitrary code on the system.
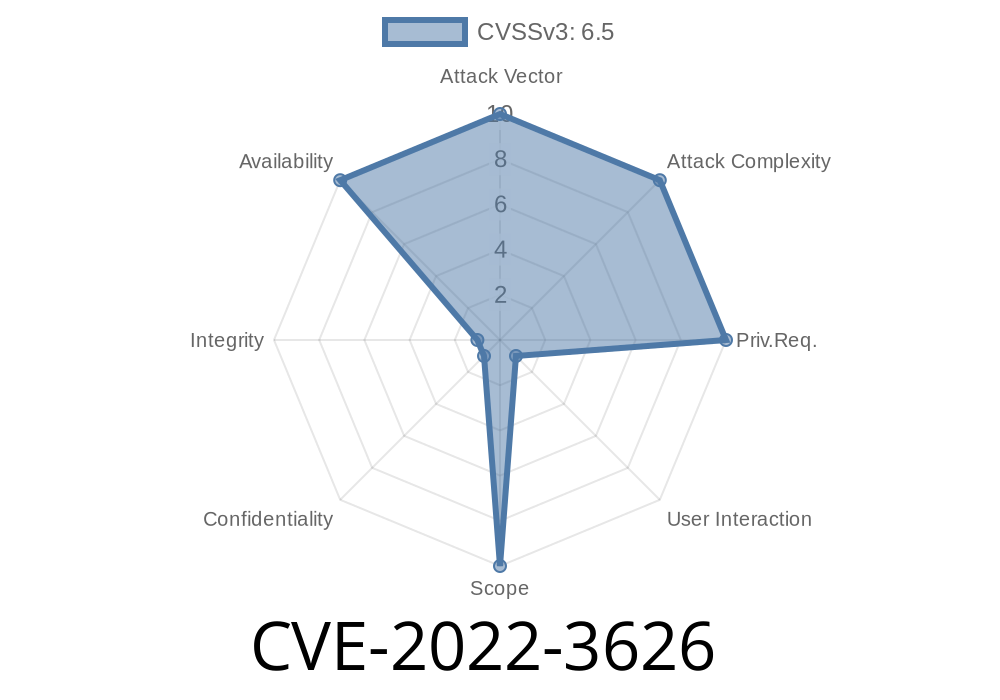
As soon as the patch was available, CVE-2022-3626 was created. In order to receive the patch, users should upgrade their software immediately.
References:
Vendor A. Patch for CVE-2022-3626
Users who are concerned about the integrity of their system can run the provided script that detects vulnerable packages and attempts to install a patched version.
https://www.libtiff.org/blog/2017/10/CVE-2022-3626.html
Source: https://helpx.adobe.com/security/products/flash-player/apsb18-10.html
Adobe has released new security updates for Flash Player to address vulnerabilities in the legacy versions of Flash Player that are used by many applications and libraries, such as Python, Go, Firefox, and Qt. This vulnerability is a critical security risk that could allow an attacker to take control of your system and access sensitive information. You should update immediately if you use any applications or libraries that rely on the integrity of libtiff to protect your computer from this threat.
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/21/2022 20:58:00 UTC