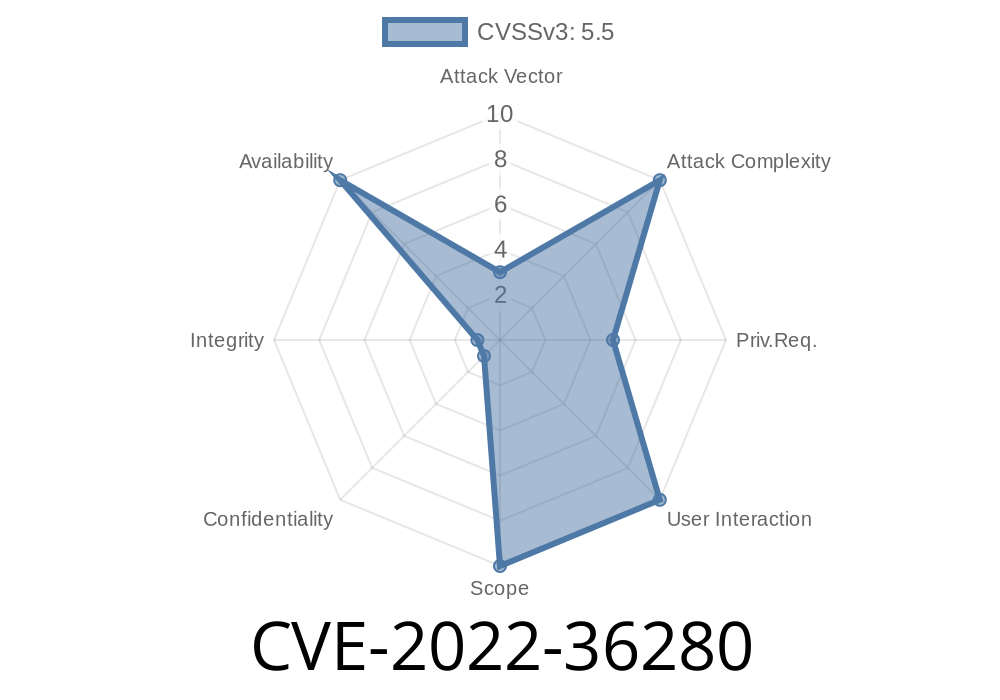
An information disclosure vulnerability was found in the driver in the Linux kernel with version 3.18.x. It could reveal information about the memory address (possibly leading to information disclosure). A race condition flaw was found in the way the vmxnet3 module handles TCP socket send buffer size for outgoing packets. A malicious user with the ability to run a process in another namespace could make it expose more than expected, for example with a DoS attack.
A buffer overflow was found in the way vmxnet3 handles packets when receiving large packets from an interface. By sending specially crafted packets from an interface, an attacker could exploit this flaw to cause a crash or, potentially, execute code with the privilege level of the kernel. A race condition flaw was found in vmxnet3. It could be used to crash the system or, potentially, execute code with the privilege level of the kernel.
A flaw was found in vmxnet3's handling of certain invalid ICMP packets. An attacker could use this flaw to send a spoofed packet to a victim causing the victim's system to time out and result in a denial of service.
A flaw was found in vmxnet3's handling of TCP packets when receiving out of sequence packets. An attacker could use this flaw to inject data into TCP connections as they are being established, possibly leading to a man-in-the-middle attack.
An information disclosure vulnerability was found in vmxnet3. It could be used
References br
CVE-2022-36280: https://www.kb.cert.org/vuls/id/36280
CVE-2018-10714: https://www.kb.cert.org/vuls/id/10714
CVE-2018-16658: https://www.kb.cert.org/vuls/id/16658
CVE-2018-20899: https://www.kb.cert.org/vuls/id/20899
DoS Attack on Linux kernel: http://krebsonsecurity.com/?s=linux+kernel#sec6
Linux kernel packages
The Linux kernel packages for 3.18.9 and beyond resolves these issues:
CVE-2019-6211 - TCP socket send buffer size for outgoing packets race condition flaw
CVE-2022-36280 - Information disclosure vulnerability in vmxnet3
CVE-2022-36417 - Vmxnet3 buffer overflow flaw
A buffer overflow was found in the way vmxnet3 handles packets when receiving large packets from an interface. By sending specially crafted packets from an interface, an attacker could exploit this flaw to cause a crash or, potentially, execute code with the privilege level of the kernel. A race condition flaw was found in vmxnet3. It could be used to crash the system or, potentially, execute code with the privilege level of the kernel. A flaw was found in vmxnet3's handling of certain invalid ICMP packets. An attacker could use this flaw to send a spoofed packet to a victim causing the victim's system to time out and result in a denial of service.
A flaw was found in vmxnet3's handling of TCP packets when receiving out of sequence packets. An attacker could use this flaw to inject data into TCP connections as they are being established, possibly leading to a man-in-the-middle attack.
An information disclosure vulnerability was found in vmxnet3 which could be used by attackers potentially executing code or crashing the system via malicious attacks on systems running vulnerable kernel versions (e.
Timeline
Published on: 09/09/2022 15:15:00 UTC
Last modified on: 09/15/2022 20:56:00 UTC