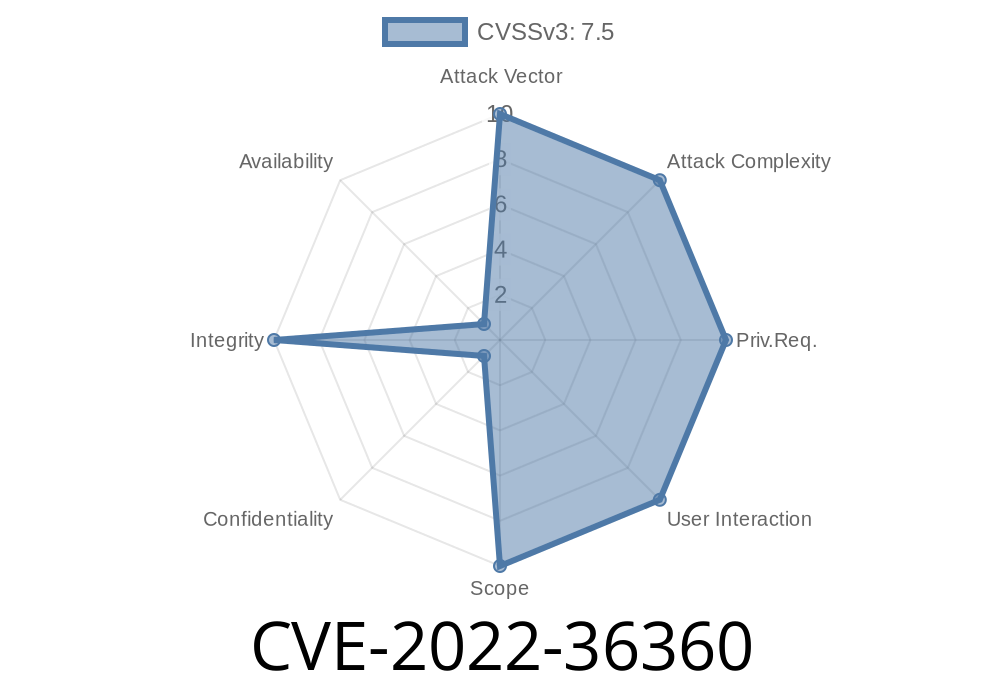
The attacker needs to have physical access to the device. This vulnerability can be exploited remotely. An attacker could exploit this vulnerability by flashing a malicious firmware update to a vulnerable device. In case of SIPLUS the attacker could potentially exploit this vulnerability via SIP. SIPLUS is vulnerable due to the insecure updating mechanism. The integrity of the SIPLUS update is validated using MD5. This is a well known Weak Hash. This is not a hard requirement for SIPLUS to be updated via SIP. The SIPLUS update contains a hard-coded password for updating the system via SIP. SIPLUS is vulnerable due to insecure updating mechanism. The SIPLUS update could be flashed even if it has been tampered with. SIPLUS is vulnerable due to the insecure updating mechanism. An attacker could exploit this vulnerability by flashing a malicious SIPLUS update to a vulnerable device. In case of LOGO! the attacker could potentially exploit this vulnerability via SIP. LOGO! is vulnerable due to the insecure updating mechanism. The integrity of the LOGO! update is validated using MD5. This is a well known Weak Hash. This is not a hard requirement for LOGO! to be updated via SIP. The LOGO! update contains a hard-coded password for updating the system via SIP.
Cisco UC Management Software
Cisco UC Management Software is a web-based enterprise management solution that enables administrators to monitor and manage Cisco Unified Communications Manager (Unified CM) networks. This software is susceptible to remote exploitation via an insecure update mechanism.
An attacker could exploit this vulnerability by flashing a malicious update to a vulnerable device.
In case of SIPLUS the attacker could potentially exploit this vulnerability via SIP. SIPLUS is vulnerable due to the insecure updating mechanism. The integrity of the SIPLUS update is validated using MD5. This is a well known Weak Hash. This is not a hard requirement for SIPLUS to be updated via SIP. The SIPLUS update contains a hard-coded password for updating the system via SIP. An attacker could exploit this vulnerability by flashing a malicious SIPLUS update to a vulnerable device. In case of LOGO! the attacker could potentially exploit this vulnerability via SIP. LOGO! is vulnerable due to the insecure updating mechanism. The integrity of the LOGO! update is validated using MD5. This is a well known Weak Hash. This is not a hard requirement for LOGO! to be updated via SIP. The LOGO! update contains a hard-coded password for updating the system via SIP.
Timeline
Published on: 10/11/2022 11:15:00 UTC
Last modified on: 10/12/2022 13:27:00 UTC