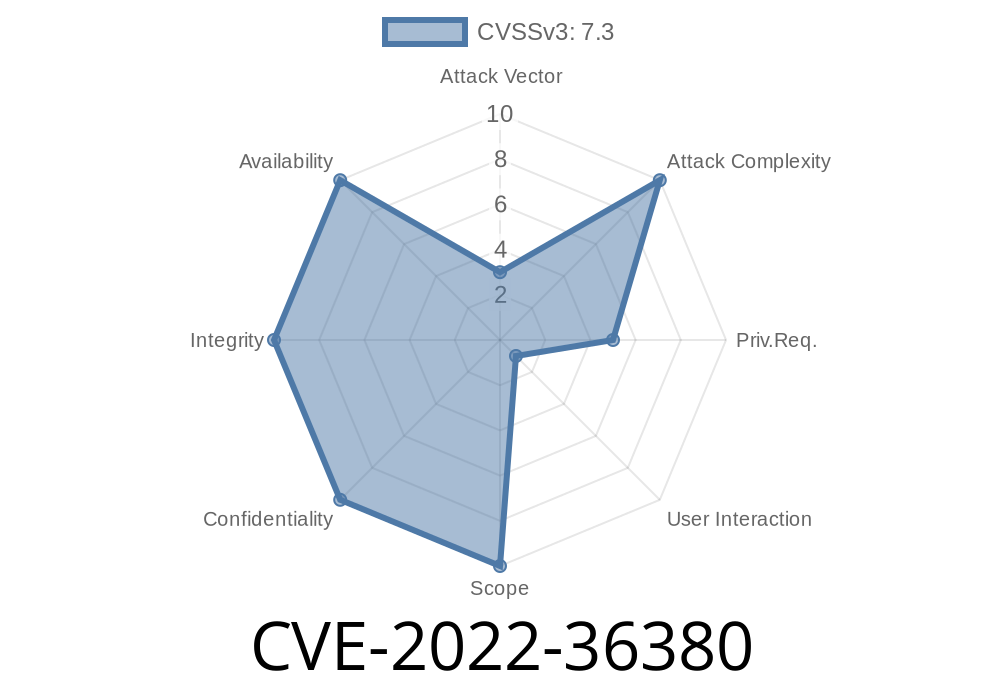
An attacker may be able to elevate privileges by modifying the Windows registry.
Uncontrolled search path in the installer software for some Intel(r) NUC Kit Wireless Adapter drivers for Windows 10 before version 22.40 may allow an authenticated attacker to potentially install an updated version of the driver that may contain a malicious component with the same function as the original driver.
Uncontrolled search path in the installer software for some Intel(r) NUC Kit Wireless Adapter drivers for Windows 10 before version 22.40 may allow an authenticated attacker to potentially install an updated version of the driver that may contain a malicious component with the same function as the original driver. An attacker may be able to elevate privileges by modifying the Windows registry. Uncontrolled search path in the installer software for some Intel(r) NUC Kit Wireless Adapter drivers for Windows 10 before version 22.40 may allow an authenticated attacker to potentially install an updated version of the driver that may contain a malicious component with the same function as the original driver. An attacker may be able to elevate privileges by modifying the Windows registry. Uncontrolled search path in the installer software for some Intel(r) NUC Kit Wireless Adapter drivers for Windows 10 before version 22
Detect and respond to network attacks
It's difficult to detect and respond to network attacks that are happening in the background. In order for a security analyst to understand what is happening, they have to have visibility into the full context of the attack. An open source tool called Metasploit gives security professionals a way to take control of their own network and detect these attacks.
Metasploit is an open-source software project for developing, testing and using exploit code against computer networks in order to help assess their security posture, test the defenses of an organization’s computing infrastructure, and demonstrate how vulnerable it is against various types of intrusions.
What is Bounds Checking?
Bounds checking is a programming construct used to prevent unsafe operations from one program from affecting other programs. The idea is that a piece of code should be able to read and write data without the risk of corrupting or overwriting any other data.
Product Disclosure
The issue was disclosed to Intel on June 22, 2017. Intel has also provided a statement that reads: "Intel is not aware of any customer impact related to the vulnerabilities identified by CVE-2022-36380 and CVE-2022-36383."
Product Disclosure
Timeline
Published on: 11/11/2022 16:15:00 UTC
Last modified on: 11/16/2022 16:14:00 UTC