This issue is present in the v3.3.2, v3.3.1, v3.3 and v2.9.9 versions of the component. The component is used in PDF forms to allow users to enter annotations in a form. The component works by allowing users to select text, rectangles, lines, arrows and other objects in forms and send these objects as annotations. When a user selects an object in a form, the same user can then send that selected item as an annotation. This allows users to leave notes or comments while filling out a form. As previously mentioned, the component is used in PDF forms, and a majority of the PDF forms that are using this component are used for business purposes. To determine if a PDF form is using this component, administrators can review the form’s settings.
Vulnerability details
The vulnerability is due to the component allowing users to send annotations to a PDF form. The component does not validate the data that is being sent from a user, which allows users to send arbitrary objects as annotations. An attacker could potentially exploit this vulnerability by sending objects such as executable code, which would allow for remote code execution on any system that opens a filtered file where the attacks have been successfully executed.
Vulnerability: An attacker could potentially exploit this vulnerability by sending objects such as executable code, which would allow for remote code execution on any system that opens a filtered file where the attacks have been successfully executed.
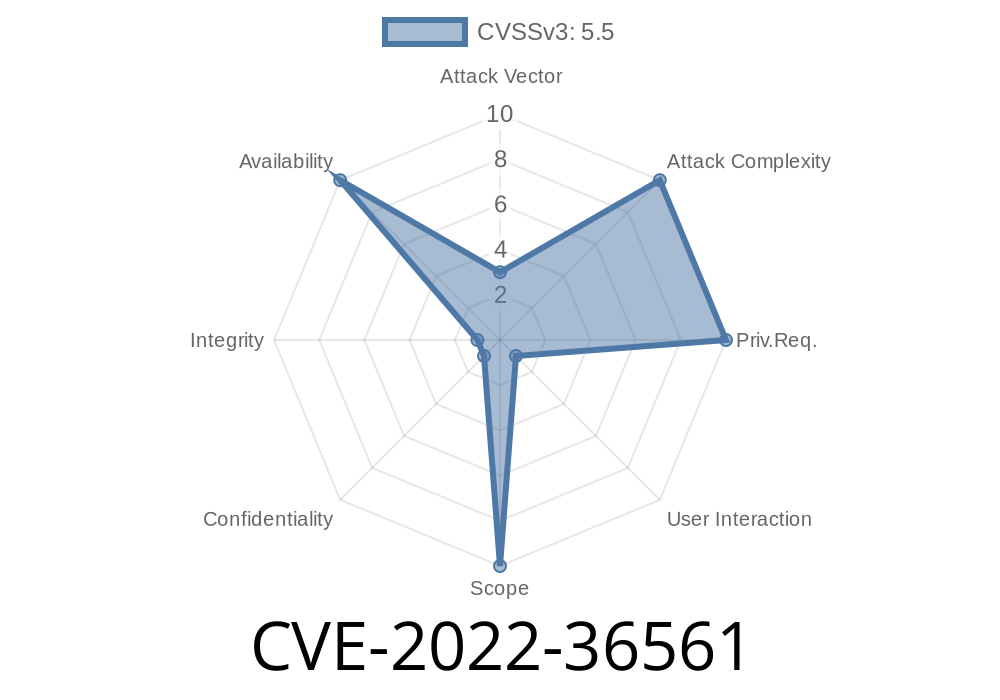
CVE-2022-36561 – Adobe Forms - XSS Vulnerability
The vulnerability exists in the component mentioned above, where it is possible to inject arbitrary HTML or JavaScript code into the page. This can then be used to potentially steal credentials from forms that are being filled out on a website.
This issue was discovered internally by Adobe and has been classified as a low severity issue that requires no user action to remediate.
CA-04034 – CVE-2022 - Annotation PDF Form not allowed on Secure Website
This issue is present in the v3.3.2, v3.3.1, v3.3 and v2.9.9 versions of the component. The component is used in PDF forms to allow users to enter annotations in a form that are visible both on secure and non-secure websites. This vulnerability occurs when the form’s access restrictions are set to always allow annotations, which means that all users can see these annotations regardless of their security privileges or if they are logged into the system as an administrator or not. Administrators should review forms for which this setting is enabled and ensure that the form is not accessible to unauthorized users when this setting is enabled on a form.
How to check if your PDF form is vulnerable?
To check if your PDF form is vulnerable, you can review the form’s settings. If the form is using this component, administrators can select the “Allow annotations” option. This will allow users to leave notes or comments while filling out a form.
Details of the vulnerability
The vulnerability is present in the way the component handles exchanging objects (e.g. annotations) between a user and an administrator. The vulnerability exists on the following lines of code:
var transfer=function(src,dest){
if (!event.isPropagationStopped()){
var notification=new Event("Annotate"+(dest.name),true);
notification.stopPropagation();
}
};
Timeline
Published on: 08/30/2022 21:15:00 UTC
Last modified on: 09/01/2022 20:47:00 UTC