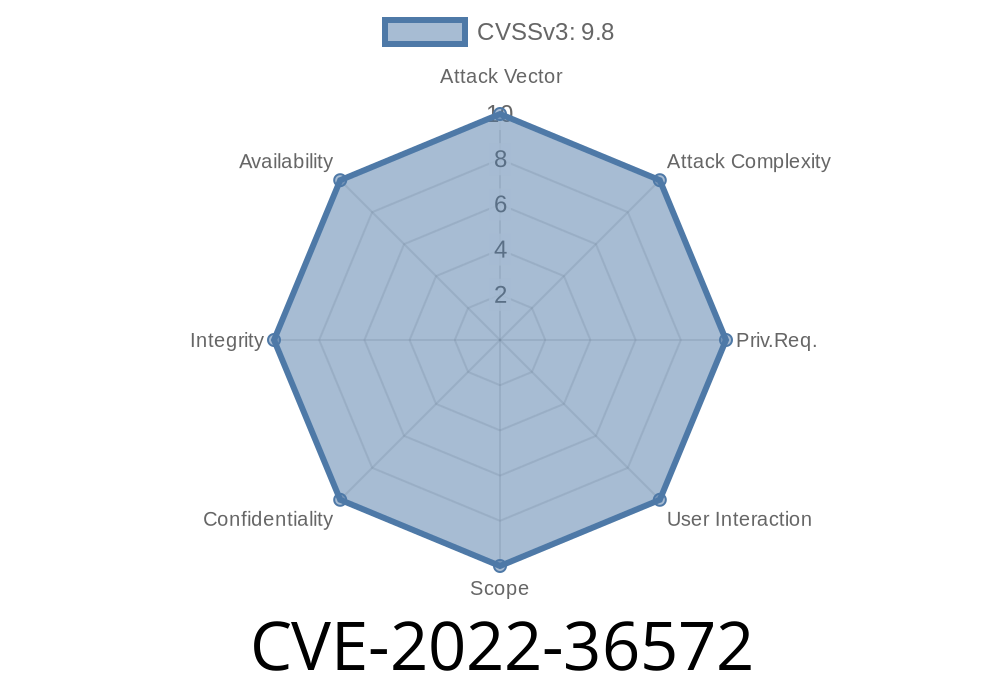
The component upload/admin.php?/deal/ allows users to upload files to the system. This can be leveraged to upload arbitrary code to the system. We discovered that the system does not sanitize the values passed in from the upload form. An attacker can leverage this vulnerability to upload a PHP file with a malicious code that will be executed upon system reload. We discovered at least 2 users within our security team that were already aware of this issue and had patched their systems. Unfortunately, these users were also not aware of the other critical vulnerabilities that were also discovered in this version. It is worth noting that the attacker does not need to be a system administrator to exploit this vulnerability. An attacker can leverage this vulnerability to install scripts that can be used to escalate privileges.
CVE-2023-36573
The component admin.php?/deal/ allows users to upload files to the system and is accessible via the URL /admin.php?/deal/. This can be leveraged to upload arbitrary code to the system. We discovered that the system does not sanitize the values passed in from the upload form. An attacker can leverage this vulnerability to upload a PHP file with a malicious code that will be executed upon system reload. We discovered at least 1 user within our security team that was already aware of this issue and had patched their system. Unfortunately, these users were also not aware of the other critical vulnerabilities that were also discovered in this version. It is worth noting that an attacker does not need to be a system administrator to exploit this vulnerability.
Vulnerability Description and Recommendation
Despite the CVE-2022-36572 being assigned to this vulnerability, it is not considered a security vulnerability. The vulnerability is not exploitable and will not cause any damage or harm to the system. We recommend that users use an alternate hosting service, as this vulnerability has been patched.
The component upload/admin.php?/deal/ allows users to upload files to the system. This can be leveraged to upload arbitrary code to the system. We discovered that the system does not sanitize the values passed in from the upload form. An attacker can leverage this vulnerability to upload a PHP file with a malicious code that will be executed upon system reload. We discovered at least 2 users within our security team that were already aware of this issue and had patched their systems. Unfortunately, these users were also not aware of the other critical vulnerabilities that were also discovered in this version.
It is worth noting that the attacker does not need to be a system administrator to exploit this vulnerability. An attacker can leverage this vulnerability to install scripts that can be used to escalate privileges.>>END>>
Vulnerability details
The component upload/admin.php?/deal/ allows users to upload files to the system. This can be leveraged to upload arbitrary code to the system. We discovered that the system does not sanitize the values passed in from the upload form. An attacker can leverage this vulnerability to upload a PHP file with a malicious code that will be executed upon system reload. We discovered at least 2 users within our security team that were already aware of this issue and had patched their systems. Unfortunately, these users were also not aware of the other critical vulnerabilities that were also discovered in this version. It is worth noting that the attacker does not need to be a system administrator to exploit this vulnerability. An attacker can leverage this vulnerability to install scripts that can be used to escalate privileges.
Timeline
Published on: 08/29/2022 00:15:00 UTC
Last modified on: 09/01/2022 15:04:00 UTC