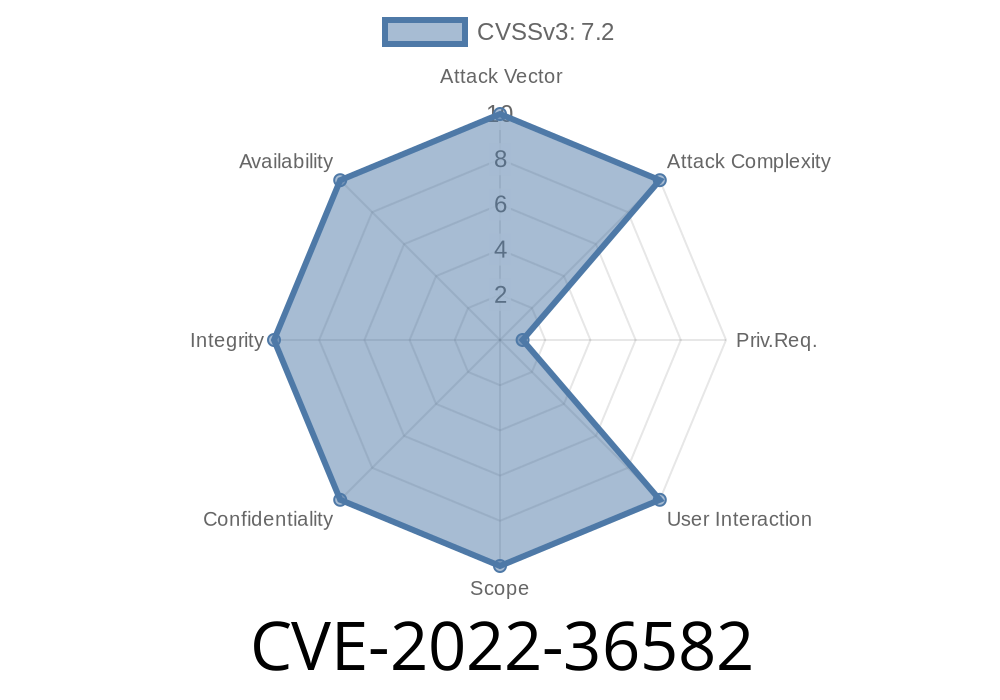
This is a file upload vulnerability and a user with file upload privileges can upload malicious files or corrupt files via the component /php_action/createProduct.php. This allows attackers to execute arbitrary code on the system or cause a Denial of Service condition. In addition, user can delete arbitrary files via the component /php_action/createProduct.php. This allows attackers to gain full control of the affected system.
This arbitrary file upload vulnerability can be exploited by an attacker by letting him/her to upload a PHP file to the component /php_action/createProduct.php. An attacker can upload a PHP file to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php. An attacker can upload a PHP code to the component /php_action/createProduct.php.
Vulnerability description:
This is a file upload vulnerability and user with file upload privileges can upload malicious files or corrupt files via the component /php_action/createProduct.php. This allows attackers to execute arbitrary code on the system or cause a Denial of Service condition. In addition, user can delete arbitrary files via the component /php_action/createProduct.php. This allows attackers to gain full control of the affected system.
Timeline
Published on: 08/31/2022 20:15:00 UTC
Last modified on: 09/02/2022 22:32:00 UTC