The D-Link DAP1650 v1.04 firmware contains fileaccess.cgi script which is used to provide information about the features of the router. When fileaccess.cgi script is accessed, a buffer overflow vulnerability can be exploited by an unauthenticated attacker to execute arbitrary code on the router. The router’s version information is stored in the fileaccess.cgi script. If an attacker sends a specially crafted request to the vulnerable firmware version, a buffer overflow can be triggered to execute malicious code on the router. The fileaccess.cgi script is vulnerable to a buffer overflow caused by the strncpy function. The D-Link DAP1650 v1.04 firmware contains the fileaccess.cgi script. If a user visits the following URL from a web browser, the router will show the router’s version information:
/cgi-bin/fileaccess.cgi?support_dir=/&dir=/&lang=en
/cgi-bin/fileaccess.cgi?support_dir=/&dir=/&lang=en If an attacker sends a specially crafted request to this URL, the script will prompt the user to view the router’s version information. If the user accepts this prompt, an attacker can use a buffer overflow to execute arbitrary code on the router.
If the user declines the prompt, the router will not show the vulnerable version information. The fileaccess.cgi script is vulnerable to a buffer overflow.
Vulnerability Details
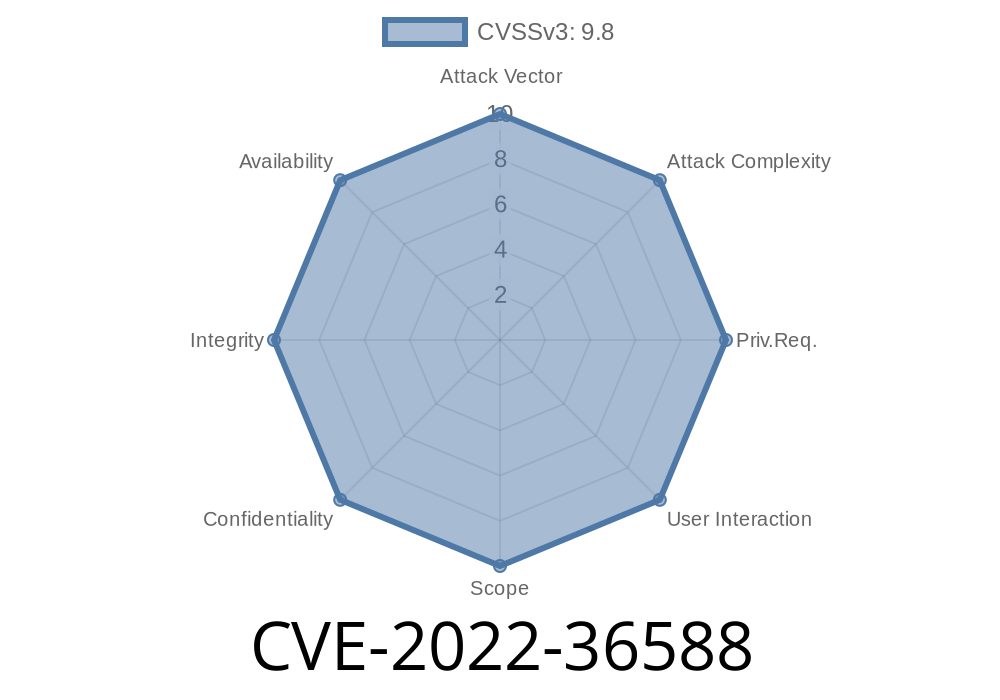
CVE-2022-36588 : Buffer overflow vulnerability in D-Link DAP1650 v1.04 firmware.
D-Link DAP1650 v1.04 fileaccess.cgi script is vulnerable to buffer overflow caused by the strncpy function.
Attacker- controlled variable
The D-Link DAP1650 v1.04 firmware contains the fileaccess.cgi script. The fileaccess.cgi script is vulnerable to a buffer overflow caused by the strncpy function, which is defined in string.h as follows:
int strncpy(char *dest, const char *src, size_t n)
The strncpy function can be exploited by an attacker to execute arbitrary code on the router with a crafted input argument. The vulnerable code snippet from the fileaccess.cgi script is as follows:
if (support_dir==="/" && dir==="/") {
if (lang == "en") {
printf("%s", VERSION);
} else {
do { printf("%s ", VERSION); sprintf(VERSION, "%d)", VERSION+1); } while ((digit+) = (digit) % 4);
}
} else if (support_dir==="/" && dir==="/") {
printf("%s", VERSION);
} else if (support_dir!="/" && support_dir!="/var/tmp") { printf("%s", VERSION); }
Vulnerability details
The fileaccess.cgi script is vulnerable to a buffer overflow caused by the strncpy function. The D-Link DAP1650 v1.04 firmware contains the fileaccess.cgi script. If a user visits the following URL from a web browser, the router will show the router’s version information:
/cgi-bin/fileaccess.cgi?support_dir=/&dir=/&lang=en
If an attacker sends a specially crafted request to this URL, the script will prompt the user to view the router’s version information. If the user accepts this prompt, an attacker can use a buffer overflow to execute arbitrary code on the router.
Vulnerability Details
The fileaccess.cgi script is vulnerable to a buffer overflow caused by the strncpy function. The D-Link DAP1650 v1.04 firmware contains the fileaccess.cgi script which is used to provide information about the features of the router. When fileaccess.cgi script is accessed, a buffer overflow vulnerability can be exploited by an unauthenticated attacker to execute arbitrary code on the router. The vulnerability occurs when an attacker sends a specially crafted request to the vulnerable firmware version, and requests for version information are accepted. If this happens, an attacker can use a buffer overflow to execute malicious code on the router using a specially crafted request from any web browser that has access to it.
CVE-2022-36588
Timeline
Published on: 09/08/2022 00:15:00 UTC
Last modified on: 09/09/2022 14:58:00 UTC