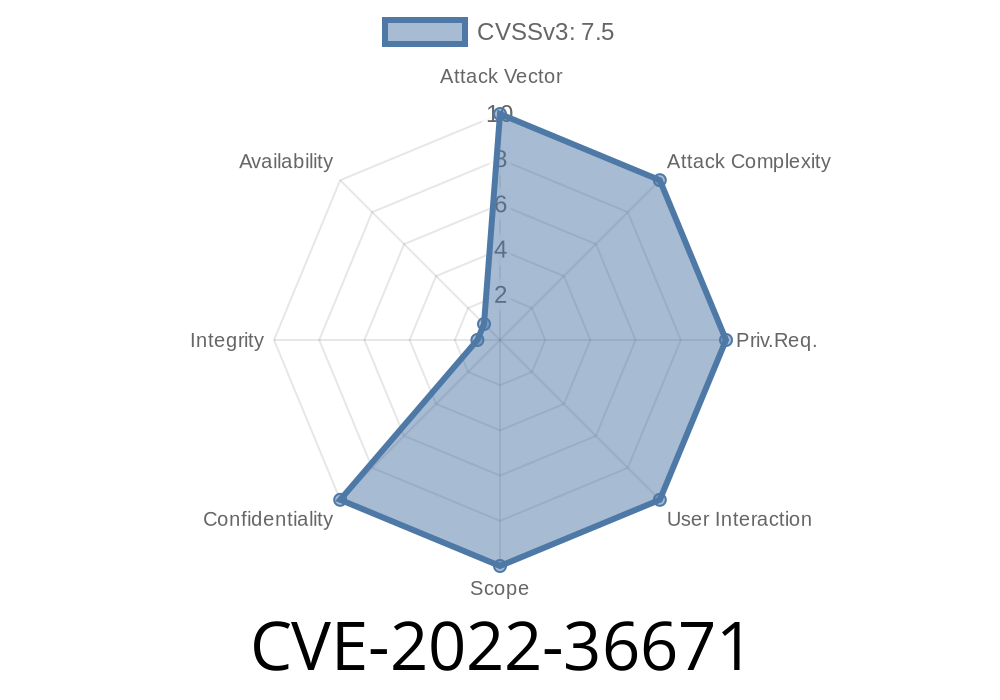
This issue was discovered in the Novel-Plus v3.6.2 plugin through the background file download API. An attacker could exploit this vulnerability by tricking the user into visiting a malicious website or accepting a malicious file via a malicious link. An attacker could also exploit this vulnerability by tricking the user into installing a malicious plugin through a malicious link. In either case, this vulnerability could allow the attacker to download an arbitrary file on the user’s computer. To exploit this issue, the user must accept the file download in the background. A malicious user could install a malicious plugin on the user’s website and link to that plugin in the novel update notification email. In this way, the attacker could exploit this issue without requiring the user to click on a link or accept the installation of a plugin. Users are advised to be cautious when installing plugins through third-party websites.
CVE-2023-36674
This issue was discovered in the Novel-Plus v3.6.2 plugin through the background file download API. An attacker could exploit this vulnerability by tricking the user into visiting a malicious website or accepting a malicious file via a malicious link. An attacker could also exploit this vulnerability by tricking the user into installing a malicious plugin through a malicious link. In either case, this vulnerability could allow the attacker to download an arbitrary file on the user’s computer. To exploit this issue, the user must accept the file download in the background. A malicious user could install a malicious plugin on the user’s website and link to that plugin in the novel update notification email. In this way, the attacker could exploit this issue without requiring the user to click on a link or accept the installation of a plugin. Users are advised to be cautious when installing plugins through third-party websites.
Vulnerability Scoring System
Vulnerability scoring system is a technique in which a security researcher rates the severity of vulnerabilities. This system can be used to measure the risk of software flaws and determine the impact they may have on users.
In this particular case, the researcher assigned three points to this vulnerability: Low = 0 points Medium = 1 point High = 2 points.
- CVSS 3 Score Score Description 0 None 1 Unauthenticated user access 2 Authenticated user access3 System compromise4 Multiple systems affected5 Denial of service6 Data loss7 Compromised integrity8 Resource exhaustion9 Unacceptable business impact10 Elevated privilege11 User takeover12 Network disruption13 System malfunction14 Unauthorized disclosure15 Other (not listed)
Vulnerability Details
This vulnerability was discovered in the Novel-Plus v3.6.2 plugin via the background file download API. An attacker could exploit this vulnerability by tricking the user into visiting a malicious website or accepting a malicious file via a malicious link. If a user is tricked into visiting a malicious website, an attacker can install their own plugin that has malicious code in it and then link to that plugin in the novel update notification email.
The following are resources for learning more about this issue:
https://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-36671
https://novellasolutionsblog.com/2018/03/20/novel-plus-v3-6-2s-plugin-vulnerability/#comment-137960
Timeline
Published on: 09/01/2022 03:15:00 UTC
Last modified on: 09/09/2022 14:38:00 UTC