A hacker can inject arbitrary SQL queries that will be executed if a user visits a maliciously crafted URL or if they try to edit a user’s details. In a case when a user is authenticated, the hacker can also see and modify various system tables and records, as well as get full access to the database. Any system that allows users to create or edit user details should be secured.
SQL injection and why it is dangerous
SQL injection is one of the most common vulnerabilities in web applications. It allows hackers to inject SQL queries that will be executed on a database, if a user visits a maliciously crafted website or tries to edit user information. A hacker can also use this vulnerability to get full access to the database and perform various actions that range from modifying system tables and records, to getting full access to the database.
As a result, it’s imperative that you secure your site against this type of attack by restricting access to just users with appropriate keys.
Interactive SQL Editor
An interactive SQL Editor is a tool that lets a user execute SQL queries without having to enter them manually. The tool allows the user to make changes to the query and execute it immediately. It also has various features, such as auto-completion, syntax highlighting, and table navigation. These features make it easy for any developer or power user to work with the tool.
The Interactive SQL Editor can be used as a powerful development tool when paired with other tools like a unit testing framework. With these tools in place, developers can quickly iterate on different pieces of code and test out how they will perform before implementing them on the server side.
Interactive SQL Editors are also great for power users who might not have the necessary knowledge or time to learn how to write queries in SQL but still need to make changes or execute them.
SQL Injection Tutorial: Introduction to SQL Injection Attacks
SQL injection is a type of injection attack that enables malicious users to execute arbitrary SQL commands on a web application. This can allow the attacker to read and write data in the database, or even take full control over the database.
In a SQL injection attack, an attacker sends malformed input that results in unexpected behavior by the Web application. The input can be stored in a database as part of its normal functioning, which then causes unexpected behavior when accessed later. This could lead to message boxes not being displayed properly, system tables getting altered and so on. There are various scenarios where this vulnerability could arise:
1) The Web application does not properly sanitize user input before it is passed to the database for processing
2) The Web application incorrectly parses user-supplied values to always use quotes around values if they have any double quotes within them
3) The Web application does not properly escape characters used by SQL queries
4) There are multiple ways for an attacker to send malicious input with some examples including: HTTP GET requests, POST requests and malformed XML data
5) An active XSS vulnerability can enable attackers to inject SQL into an otherwise legitimate URL
6) A PHP file with user input that is improperly processed by a MySQL server These vulnerabilities are often combined together with other vulnerabilities such as directory traversal where an attacker can access files on disk without authentication or SOP bypass where the weakness in default settings allows attackers to bypass security restrictions like permissions or file
How do hackers exploit this vulnerability?
A hacker can exploit this vulnerability by injecting arbitrary SQL queries that will be executed if a user visits a maliciously crafted URL or if they try to edit a user’s details. In a case when a user is authenticated, the hacker can also see and modify various system tables and records, as well as get full access to the database. Any system that allows users to create or edit user details should be secured.
SQL Injection - a threat to any website
SQL Injection is a threat to any website. So, if you want to avoid it, make sure that your website uses a secure authentication system (such as one that runs on ASP.NET). Protect your site from SQL injection vulnerabilities by using the following:
1) Login validation controls
2) Regular expressions for input validation
3) Database encryption
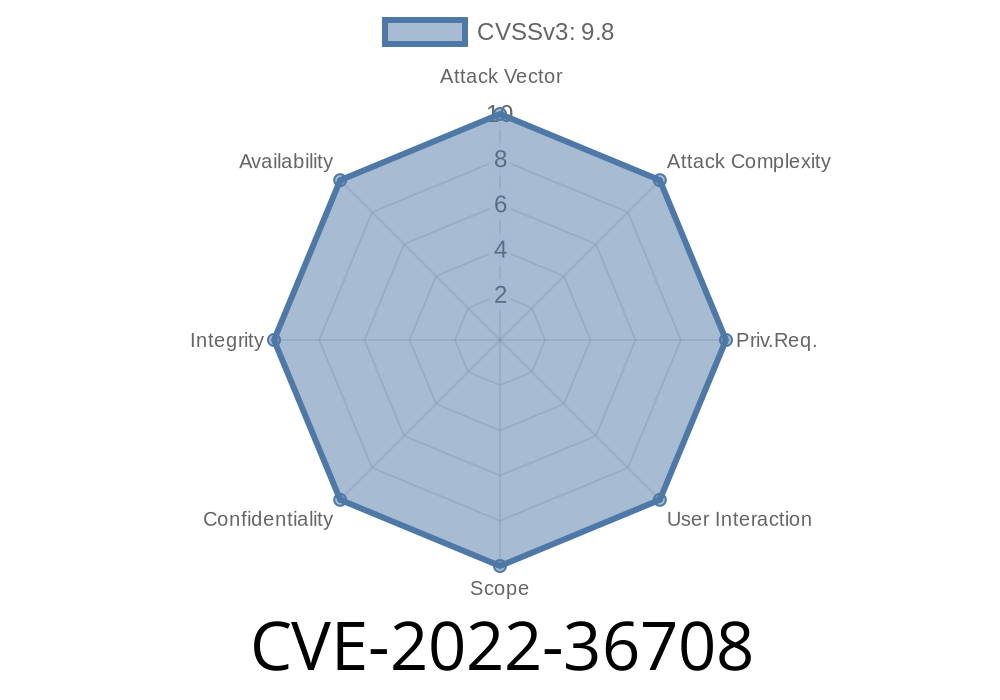
Timeline
Published on: 08/28/2022 23:15:00 UTC
Last modified on: 09/01/2022 13:18:00 UTC