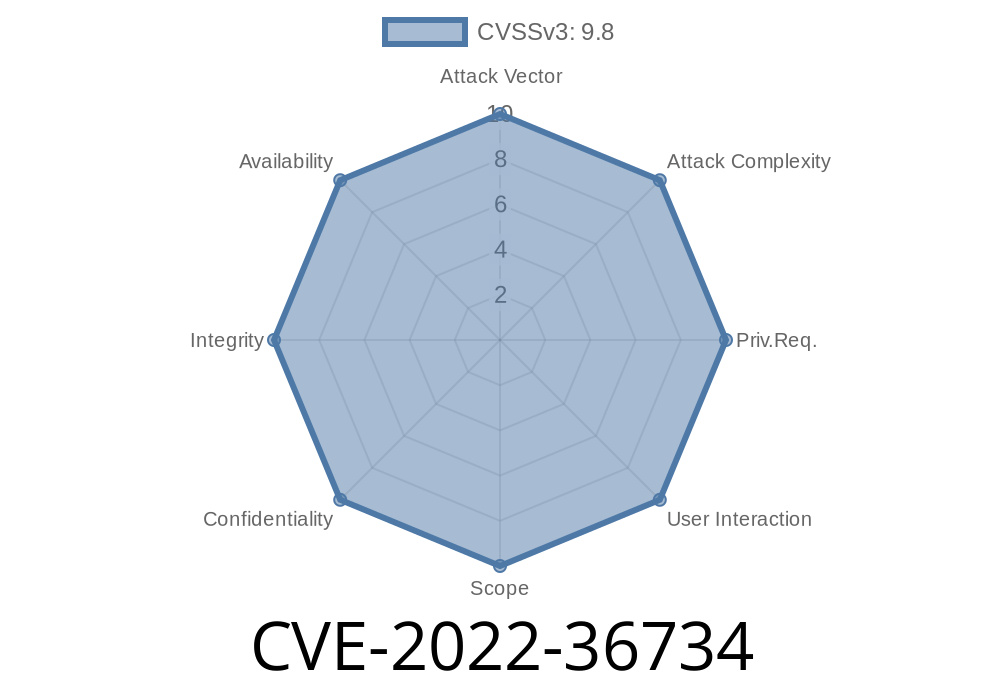
A remote attacker could leverage this vulnerability to execute arbitrary SQL commands, resulting in a complete control of the affected application. In certain cases, the SQL injection could also result in information disclosure and/or privilege escalation.
It was reported that Home Library Management System v1.0 is prone to another injection issue at /admin/convert.php. If a user is logged in with the “System Administrator” role, a malicious user could exploit this issue to inject SQL commands and obtain SQL injection results.
Technical Operations
A remote attacker could leverage this vulnerability to execute arbitrary SQL commands, resulting in a complete control of the affected application. In certain cases, the SQL injection could also result in information disclosure and/or privilege escalation.
Vulnerable Parameter :
- id
- convert
- ctime
- cid
- ids
- stream
SQL Injection in Home Library Management System
Discovered by Qualys, this issue is a result of the lack of input validation in the system. The application would allow any user to inject commands into it. This could lead to executing arbitrary SQL commands, resulting in a complete control of the affected application. In certain cases, the SQL injection could also result in information disclosure and/or privilege escalation.
Vulnerability discovery and exploitation
Vulnerability discovery:
An attacker can use the SQLi vulnerability to gain access to the admin panel of a system. The following URL is vulnerable to SQL injection: https://server/admin/convert.php?lang=en&type=book
Vulnerability exploitation:
The attacker could then execute arbitrary SQL commands, resulting in a complete control of the affected application. In certain cases, the SQL injection could also result in information disclosure and/or privilege escalation.
Timeline
Published on: 08/30/2022 21:15:00 UTC
Last modified on: 09/01/2022 07:01:00 UTC