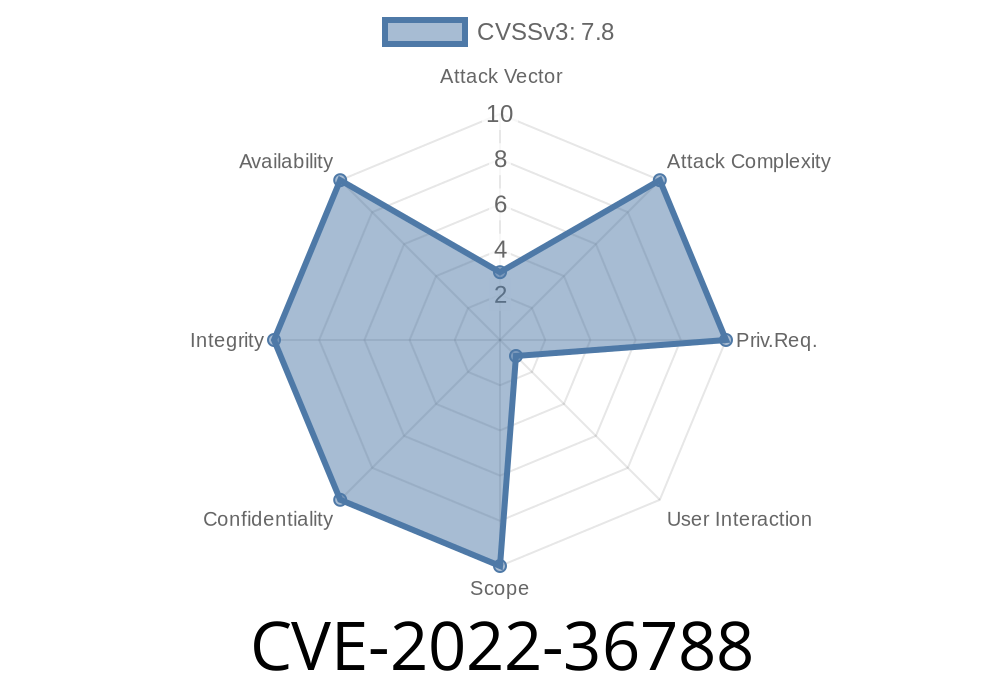
A major vulnerability, CVE-2022-36788, was discovered in Slic3r’s libslic3r — a library core used by the popular open-source 3D printing slicer Slic3r, version 1.3. and the master commit b1a550. This flaw is a heap-based buffer overflow that occurs during the *clone functionality* of the TriangleMesh class. Its true danger? A specially-crafted STL file can trigger it, giving attackers a route to execute arbitrary code by just making you open a 3D file. Let's understand this vulnerability step by step, in straightforward language, with code snippets and references for those who want to dig deeper.
What is Slic3r?
Slic3r is a widely used tool to convert 3D models (usually in STL format) into instructions (G-code) that a 3D printer understands. Slic3r’s heart — the libslic3r component — crunches STL files and prepares them for printing.
The Problem: Heap Buffer Overflow in clone()
The vulnerable code lives in the libslic3r library, in the function that duplicates a TriangleMesh object. When cloning mesh data, the function over-allocates memory when leaf data of the STL is copied, but does not check that incoming data fits the destination buffer. If an attacker creates an STL file that contains more vertices or faces than expected, the function will write past the buffer’s end.
Simplified Vulnerable Code
Here’s a reconstructed snippet that shows the issue (based on public code and the vulnerability description):
// libslic3r/src/libslic3r/TriangleMesh.cpp
TriangleMesh TriangleMesh::clone() const {
TriangleMesh mesh;
// Assume vertices is a vector of structs, faces is similar
mesh.vertices = new Vertex[this->vertices_count]; // Heap allocation
// No check: this->vertices_count can be from a malicious STL
memcpy(mesh.vertices, this->vertices, this->vertices_count * sizeof(Vertex));
// Same for faces...
mesh.faces = new Face[this->faces_count];
memcpy(mesh.faces, this->faces, this->faces_count * sizeof(Face));
return mesh;
}
If the input STL lies about how many vertices or faces it holds, the clone functionality will allocate memory based on that *believed* count, but malicious data can overflow this, especially if there's mis-parsing or out-of-bounds copies in complex STL structures or deserialization logic.
Exploitation Details
Attackers need no special access or privileges — they just need to trick someone into opening a booby-trapped STL file with a vulnerable version of Slic3r (or another tool that uses libslic3r). On opening, the heap buffer overflows, typically resulting in the program crashing. But much worse is possible: Carefully crafted files can overwrite control data in memory, leading to arbitrary code execution.
A proof of concept (PoC) STL file might have more vertices than real data, or contain out-of-bounds data fields padded in binary format.
Example of Malicious STL File Structure (pseudo-hex)
solid expl
facet normal ...
outer loop
vertex X Y Z
vertex X Y Z # Repeated, possibly overflowing legitimate count
vertex X Y Z
endloop
endfacet
... (malformed data follows)
endsolid
By exploiting parsing inconsistencies and buffer calculations, this malformed file overflows allocated heap, corrupting memory.
What’s the Real-World Risk?
- Remote Code Execution: By running arbitrary code, attackers could install malware, access sensitive files, or take over the machine.
- Crash/Denial of Service: Even minor exploitation can cause Slic3r to crash, disrupting work.
- Supply Chain Attacks: Any downstream projects using libslic3r or forked versions are also vulnerable unless patched.
Slic3r users with v1.3. and any installation using commit b1a550 or earlier.
- Downstream forks/projects using vulnerable libslic3r.
Update Immediately:
Check for patches or merge requests on Slic3r GitHub.
At the time of writing, full fixes may not be available in all downstream forks, so check your vendor.
Check For Fixes:
- Official patch (if available)
- CVE NVD listing
Automatic Testing:
If you’re developing or deploying in an automated pipeline, fuzz STL input or use tools like American Fuzzy Lop to test for buffer overflows.
References
- CVE-2022-36788 at NVD
- Slic3r source code
- Original advisories and PoC discussions
Conclusion
CVE-2022-36788 isn’t just a 3D-printing nerd’s problem — it’s a classic example of how file parsing bugs can become massive security holes. If you use Slic3r or libraries derived from it, make sure you’ve updated, and remember: treat 3D files just like any other untrusted software. Don’t get pwned by a plastic figurine!
Got questions or want to know about other vulnerabilities in open-source software? Drop them below!
Timeline
Published on: 04/20/2023 16:15:00 UTC
Last modified on: 05/02/2023 15:05:00 UTC