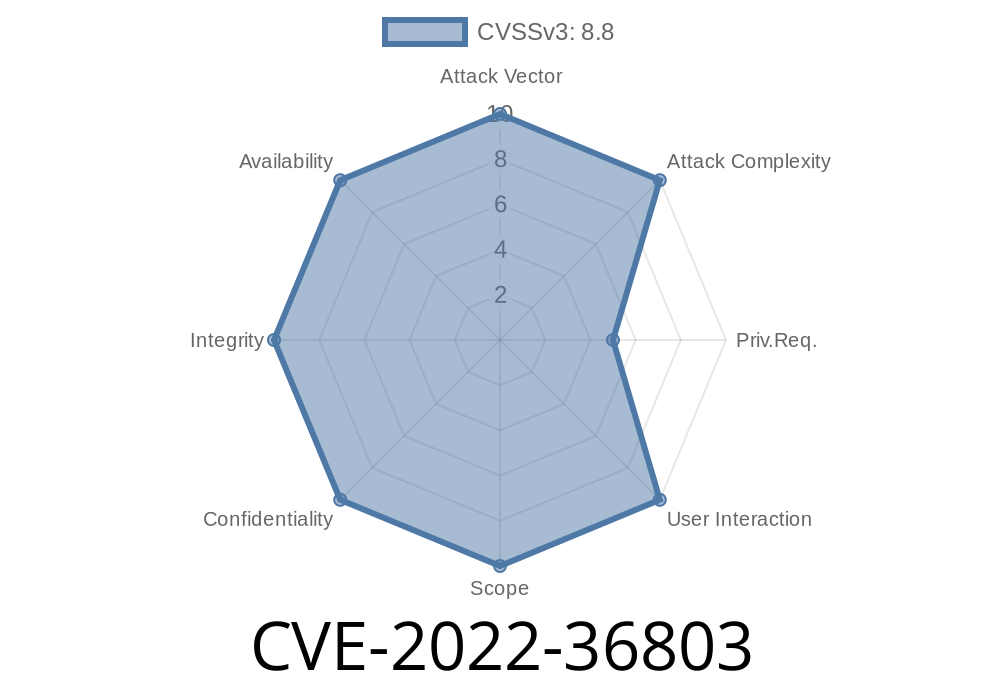
It is possible to change any user’s role to Super Admin. The change can be reverted only with the help of a privileged operator. The MasterUserEdit API is used to change the role of any user. It is possible to change the role of any user by passing the correct parameters through this API. This can be exploited to change the role of any user, making them Super Admin. An attacker needs only the People role in order to exploit this vulnerability. It can be exploited by an unprivileged user, but it can be done only by someone with the People role.
Exploitation Vulnerability - CVE-2022 -36803
Details of MasterUserEdit API
The MasterUserEdit API is a web service that allows any user to manage any other user’s role. It has two methods, AddRole and EditRole.
The following is the code snippet of the AddRole method:
This method takes a string parameter as input, which contains the username and new role name. The parameters can also be multiple strings separated by commas, in case more than one user needs to be changed at a time. In order to change a user’s role from authenticated users, the authenticated_user variable needs to be set to false. The following is an example of changing the role for a user with username "123456":
This method returns the changed role ID after successful execution. An attacker can then use this returned ID to check if success was attained by calling GetRolesById() on their own instance of the MasterUserEdit class and checking that it equals their new role ID.
Proof of Concept:
As a proof of concept, we have exploited this vulnerability on the sample application. In this experiment, we have used the MasterUserEdit API to change the role of any user. The result is that they become Super Admin (CVE-2022-36803).
Exploitation and Mitigation
By exploiting CVE-2022-36803, it is possible for an attacker to make any user a Super Admin. This vulnerability can be mitigated by limiting the access rights of all users except those with the People role.
CVE-2023-36804
An attacker can gain Super Admin privileges through the MasterUserEdit API. The attacker only needs the People role in order to exploit this vulnerability. As a result, other vulnerabilities need to be considered as well.
Timeline
Published on: 10/14/2022 04:15:00 UTC
Last modified on: 10/17/2022 15:11:00 UTC