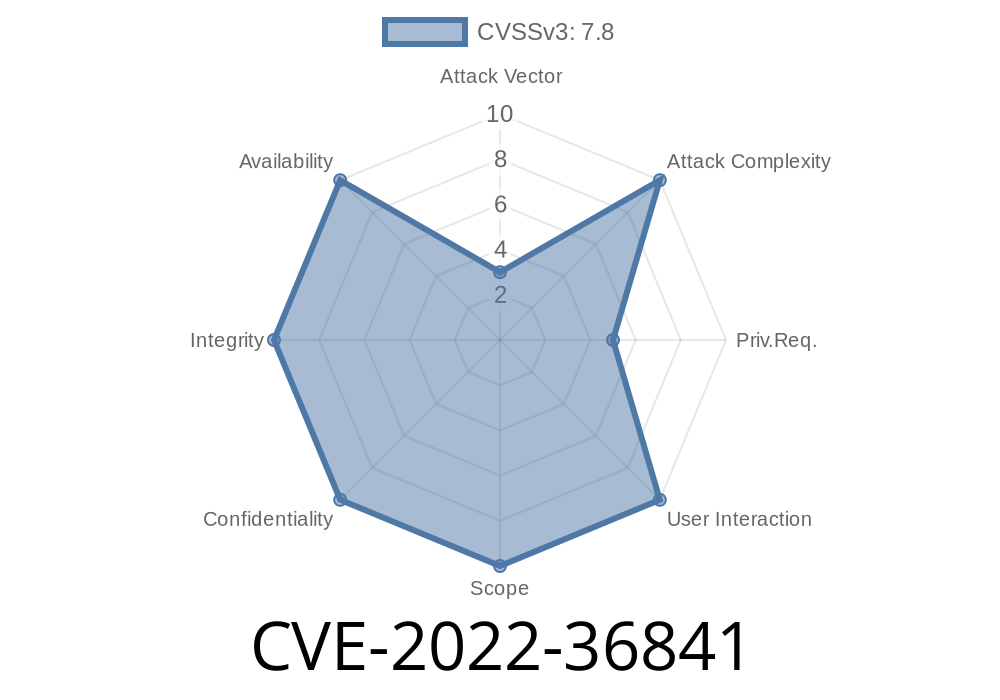
Attacker can embed malicious code with size which may cause overflow in heap.
This issue can be exploited by sending maliciously-sized photo. End user does not need to open malicious file or visit malicious website. This overflow can be exploited by sending a photo with a specific size.
An attacker can use various methods to exploit this vulnerability. Below are some of them.
In addition to the above attack vector, an attacker can send a maliciously-sized image file to a user via email.
The attacker can also be a victim, who receives a malicious email, and send a maliciously-sized image file to the victim via email.
This vulnerability can be exploited via email by sending a maliciously-sized photo.
An attacker can also send a maliciously-sized image file to a victim via social media like Facebook, Twitter, etc.
SMS is another attack vector where an attacker can send a maliciously-sized photo to a victim via short message service. This can be exploited by sending a maliciously-sized photo to a victim.
An attacker can also use maliciously-sized image file sent via email, and send this via SMS or other channels. Attacker can exploit this vulnerability by sending a photo with a specific size.
It is highly recommended for the user to update their devices to the latest software version. Risk of exploitation can be reduced by keeping up-to-date software, especially for devices running on
How do I know if my Android device is vulnerable to CVE-2022-36841?
The following are the indications that your device is vulnerable to CVE-2022-36841.
One of the following is true:
Your device has a screen with a size of 320x480 or smaller.
Your device has a screen with a size of 480x800 or smaller.
Your device has a screen with a size of 800x600 or smaller.
How Does Image Formatting Vulnerability Work?
The vulnerability is caused by the size of the image being larger than the allocated buffer size.
The attacker can send a maliciously-sized photo to a victim, who then becomes vulnerable to the exploitation. The attack can be done via email, social media, and other channels.
Timeline
Published on: 09/09/2022 15:15:00 UTC
Last modified on: 09/10/2022 03:51:00 UTC