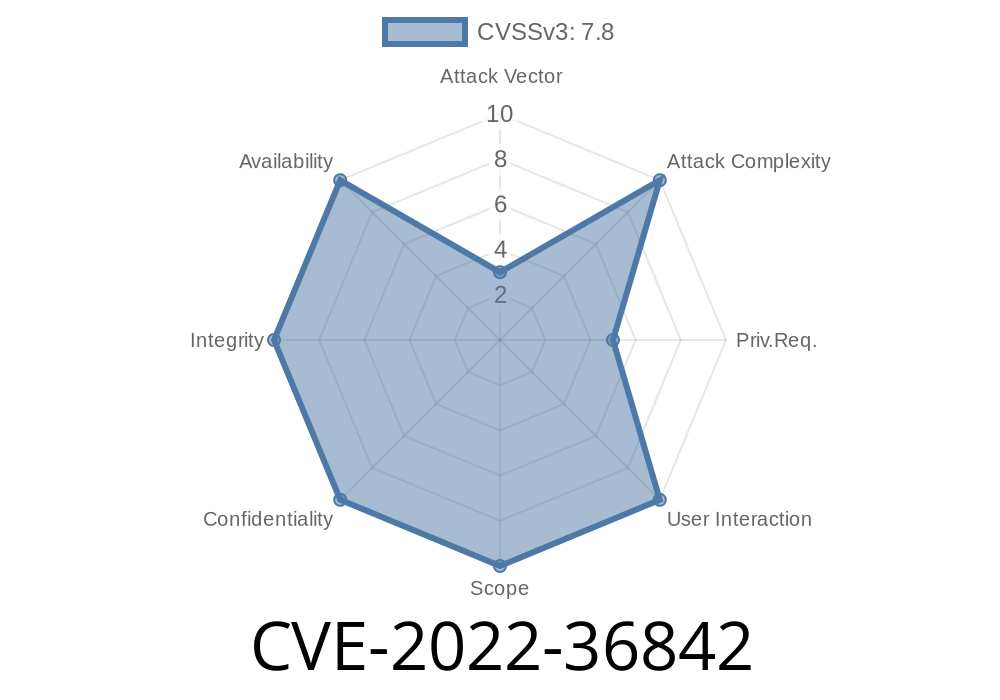
Attacker can exploit this issue to cause remote code execution in the context of the current user. This issue has been fixed in SMR Sep-2022 Release 1.
It is possible to exploit these vulnerabilities. Exploitation of these vulnerabilities requires no special user capability unless the user has physical access to the device.
Vendors/products should update their devices to the latest version.
Vendor information about these vulnerabilities can be found here.
It is recommended to monitor for the latest updates. Stay Vigilant! -PIO On this Weak Sign-off Day, we have 3 vulnerabilities to keep in mind.
Vulnerability summary for day 5
The first vulnerability is CVE-2022-36842. This issue has been fixed in SMR Sep-2022 Release 1.
To exploit this issue, an attacker would need to have physical access to the device. Exploitation of these vulnerabilities requires no special user capability unless the user has physical access to the device. Vendors should update their devices to the latest version after receiving notification from their vendor. Vendor information about these vulnerabilities can be found here. Stay Vigilant!
CVE-2022-36981
Attacker can exploit this issue to gain unauthorized access to files and data.
No special user capability is required for exploitation of these vulnerabilities.
Vendor information about these vulnerabilities can be found here.
It is recommended to monitor for the latest updates. Stay Vigilant! -PIO
Vulnerability discovery and discovery process
Vulnerability details for SMR Sep-2022 Release 1
-CVE-2022-36842: Weak Sign-off Day Issue: Remote Code Execution in the Context of the Current User -Vendor information about this vulnerability can be found here.
Timeline
Published on: 09/09/2022 15:15:00 UTC
Last modified on: 09/10/2022 03:51:00 UTC