This issue was addressed by implementing a new control flow for data transfer to and from the Web Console, which now uses encrypted HTTPS. The new control flow was implemented by removing the Data.toString() function call from the Web Console. As a result, untrusted data can no longer be deserialized, and the risk of a successful remote code execution is significantly reduced. As always, an organization can implement a risk assessment to determine if this issue is a concern for their environment.
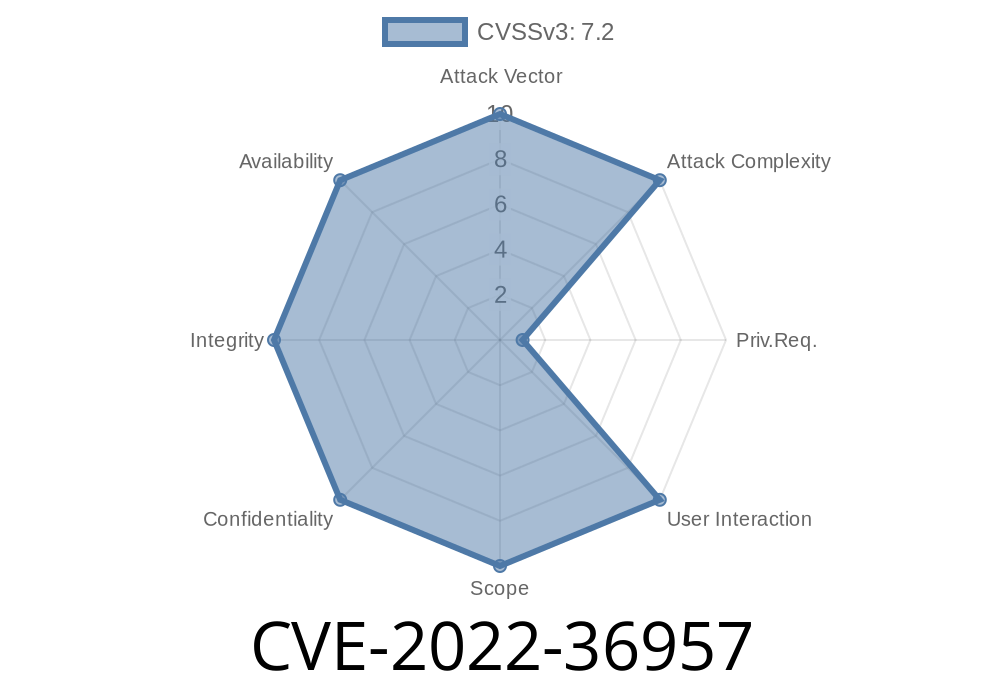
Summary of CVE-2022-36957
The following is a summary of CVE-2022-36957:
A vulnerability in the Web Console found in Cisco Prime Infrastructure (PI) could allow an unauthenticated, remote attacker to execute code on an affected system. The vulnerability is due to improper sanitization of user input, which may lead to deserialization of malicious data. An attacker could exploit this vulnerability by sending a crafted serialized object over HTTP. As a result, the attacker could execute arbitrary code on the target system with the privileges of the user running PI. To exploit this vulnerability, an attacker would have to send a specially crafted URL that includes serialized objects and host header data for a server running PI.
Vulnerability summary
This vulnerability is a low to medium risk.
Vulnerabilities are always a concern, but this particular vulnerability was addressed by implementing the new control flow for data transfer to and from the Web Console. This fix does not address any other vulnerabilities in their product or any of its components. However, an organization can determine if this issue is a concern for them by conducting their own risk assessment with regards to how much remote code execution could impact their environment.
Monitoring Recommendations
Organizations should monitor for this issue, as it is necessary to remediate. By monitoring their environment, they can determine whether the risk is appropriate for their environment.
As a result of this fix, an organization should use a control flow that encrypts data sent over HTTPS.
Timeline
Published on: 10/20/2022 21:15:00 UTC
Last modified on: 10/21/2022 18:53:00 UTC