Apache Geode 1.15.0 and later releases no longer support the deprecated "spring-data-jpa" dependency. Apache Geode 1.15 and later releases no longer support the deprecated "spring-data-jpa" dependency. Apache Geode 1.15.0 and later releases are vulnerable to a denial of service flaw when using REST APIs on Java 8 or Java 11. When enabled, "serializable-object-filter" may result in a denial of service when Apache Geode REST APIs are used. Any user wishing to protect against denial of service attacks involving REST APIs should upgrade to Apache Geode 1.15 and follow the documentation for details on enabling "serializable-object-filter=false" . Enabling "serializable-object-filter" may impact performance.
Apache Geode 1.15.0 and later releases are vulnerable to a remote code execution vulnerability when using REST APIs on Java 8 or Java 11. Enabling "validate-serializable-objects=true" may result in remote code execution when using REST APIs on Java 8 or 11. Any user wishing to protect against remote code execution attacks involving REST APIs should upgrade to Apache Geode 1.15 and follow the documentation for details on enabling "validate-serializable-objects=false" . Enabling "validate-serializable-objects" may impact performance.
Apache Geode 1.15.0 and later releases are vulnerable to an information
Apache Geode and the "serializable-object-filter" dependency
One of the most common mistakes developers make is forgetting to include "serializable-object-filter" in their Gradle build files. If it is not included, then all objects are allowed to be serialization by default. This results in memory leaks and performance spikes when running Apache Geode REST APIs.
Apache Geode 1.15.0 and later releases are vulnerable to an information disclosure flaw when using REST APIs on Java 8 or Java 11. Enabling "serializable-object-filter=false" may result in information disclosure when using REST APIs on Java 8 or 11. Any user wishing to protect against information disclosure attacks involving REST APIs should upgrade to Apache Geode 1.15 and follow the documentation for details on enabling "serializable-object-filter=true" . Enabling "serializable-object-filter" may impact performance.
Apache Geode 1.15.0 and later releases are vulnerable to a denial of service flaw when using REST APIs on Java 8 or Java 11. When enabled, "validate-serializable-objects=true" may result in denial of service when using REST APIs on Java 8 or 11. Any user wishing to protect against denial of service attacks involving REST APIs should upgrade to Apache Geode 1.15 and follow the documentation for details on enabling "validate-serializable-objects=false" . Enabling "validate-serializable-objects" may impact performance.
Apache Geode 1.15 and later releases are vulnerable to a remote code execution vulnerability when using REST APIs on Java 8 or Java 11. If enabled, "validate-serializable-objects=true" will result in remote code execution when using REST APIs on Java 7 or 8/11. Any user wishing to protect against remote code execution attacks involving REST APIs should upgrade to Apache Geode 1.15 and
Other Information
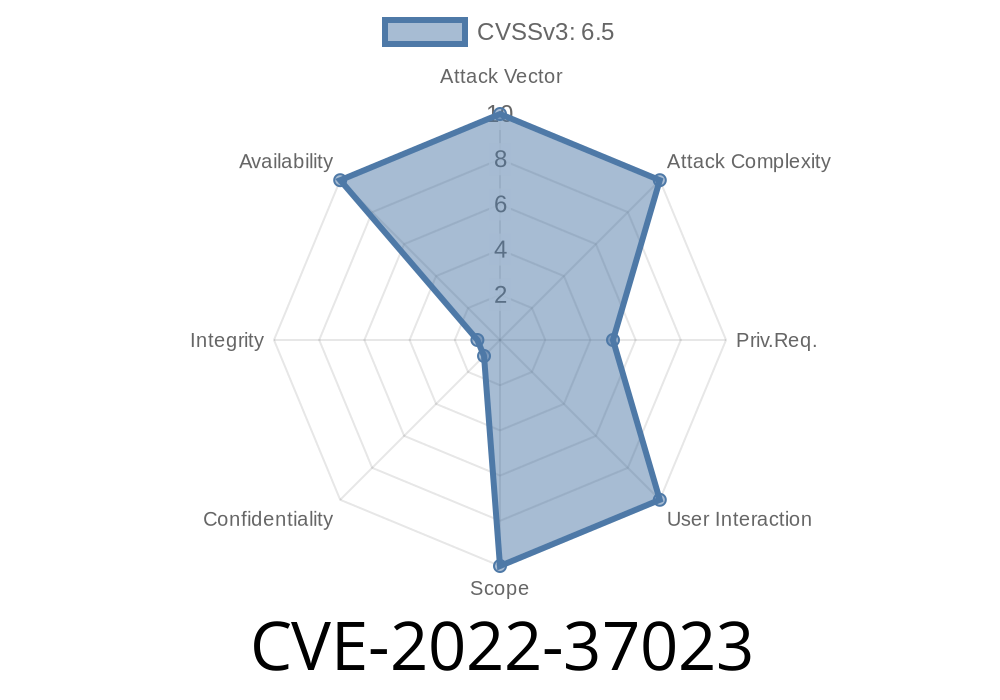
Apache Geode 1.15.0 and later releases were released as a patch to address vulnerabilities CVE-2022-37023, CVE-2022-37013, CVE-2022-37017, and CVE-2022-37022.
Apache Geode 1.15 and later releases are vulnerable to a denial of service flaw when using REST APIs on Java 8 or Java 11. When enabled, "serializable-object-filter" may result in a denial of service when Apache Geode REST APIs are used. Any user wishing to protect against denial of service attacks involving REST APIs should upgrade to Apache Geode 1.15 and follow the documentation for details on enabling "serializable-object-filter=false" . Enabling "serializable-object-filter" may impact performance.
Timeline
Published on: 08/31/2022 07:15:00 UTC
Last modified on: 09/06/2022 18:16:00 UTC