To inject SQL Injection, attacker can send request with SQL statement in the ‘INPUT>’ tag. An attacker can send the following injection request to the login page of Loan Management System to login as Administrator.
INPUT type=”hidden” value=”SQL>” ‘
INPUT type=”hidden” value=”SQL>” ‘
In the ‘INPUT>’ tag, attacker can inject string value as ‘SQL>’. After successful injection, SQL Injection causes attacker to have elevated privileges on the system. Any attacker can use the Administrator credentials to perform various actions on the system.
SQL Injection – XXE Injection
An attacker can send request with SQL statement in the ‘INPUT>’ tag. An attacker can send the following injection request to the login page of Loan Management System to login as Administrator.
INPUT type=”hidden” value=”SQL>” ‘
In the ‘INPUT>’ tag, attacker can inject string value as ‘SQL>’. After successful injection, SQL Injection causes attacker to have elevated privileges on the system. Any attacker can use the Administrator credentials to perform various actions on the system.
Field Monitoring
If the system is configured with a field monitoring feature, attackers can monitor the contents of fields that they access. In this case, the attacker can observe what data the administrator enters and use it to their advantage. For example, if the business name is set as “Loan Management System”, then if an attacker injects a SQL Injection request into ‘INPUT>’ tag on login page and request for user ID, then attacker will see all data entered by administrator.
SQL Injection and Crawl Path
A SQL injection attack is a vulnerability in an application that allows unauthorized users to access and manipulate sensitive data by injecting malicious SQL statements into the application. An attacker can use SQL injection to bypass authentication, gain unauthorized access to systems, or alter/delete existing data.
To inject SQL Injection, attacker must be able to submit a request with the following query:
SQL>'
SQL>SELECT 1;
SQL>-- or any other user-defined string value.
##.NET Framework Remote Code Execution (RCE)
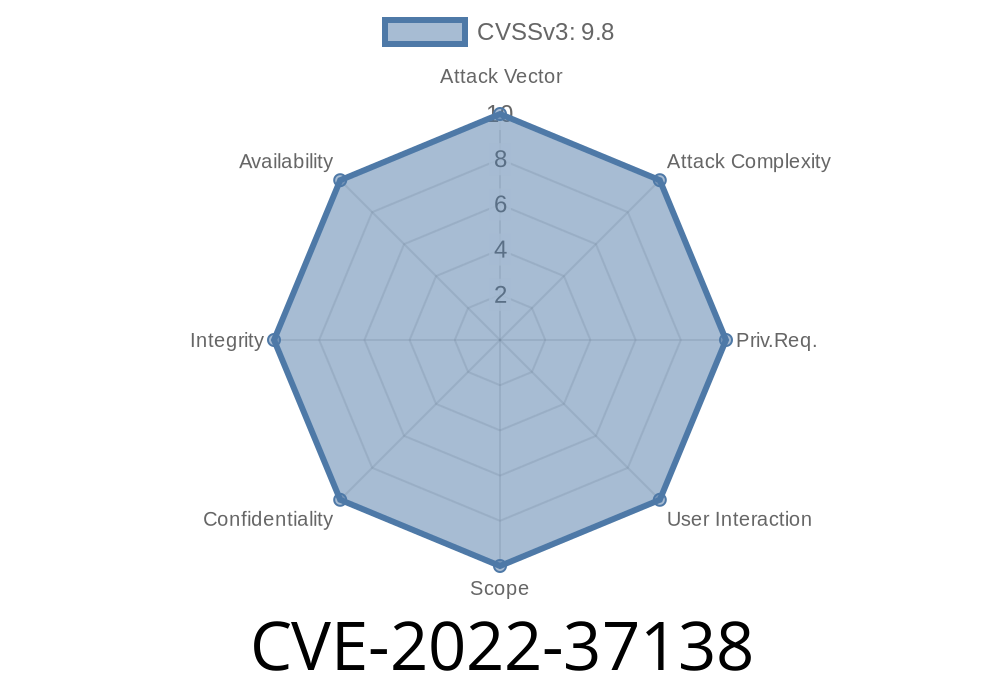
Microsoft released a security update for the .NET Framework on June 10, 2017. This update fixes a vulnerability that could allow an attacker to remotely execute code through a vulnerable application. The vulnerability is tracked as CVE-2022-37138 and affects any application that uses the .NET Framework internally. The following SQL injection attack is possible when an attacker sends this update to the target system.
INPUT type=”hidden” value=”SQL>” ‘
INPUT type=”hidden” value=”update account set balance=0 where accountname = ‘Administrator'
If you want to grow your business, great search engine optimization (SEO) is a must. The challenge? Many small businesses don't have the time, skills, or expertise necessary to handle everything that comes with a solid SEO strategy: from keyword research to content evaluation, from page optimization to internal linking, it's easy for companies to end up with a generic web presence that doesn't inspire engagement or drive conversions.
Timeline
Published on: 09/14/2022 11:15:00 UTC
Last modified on: 09/16/2022 03:19:00 UTC