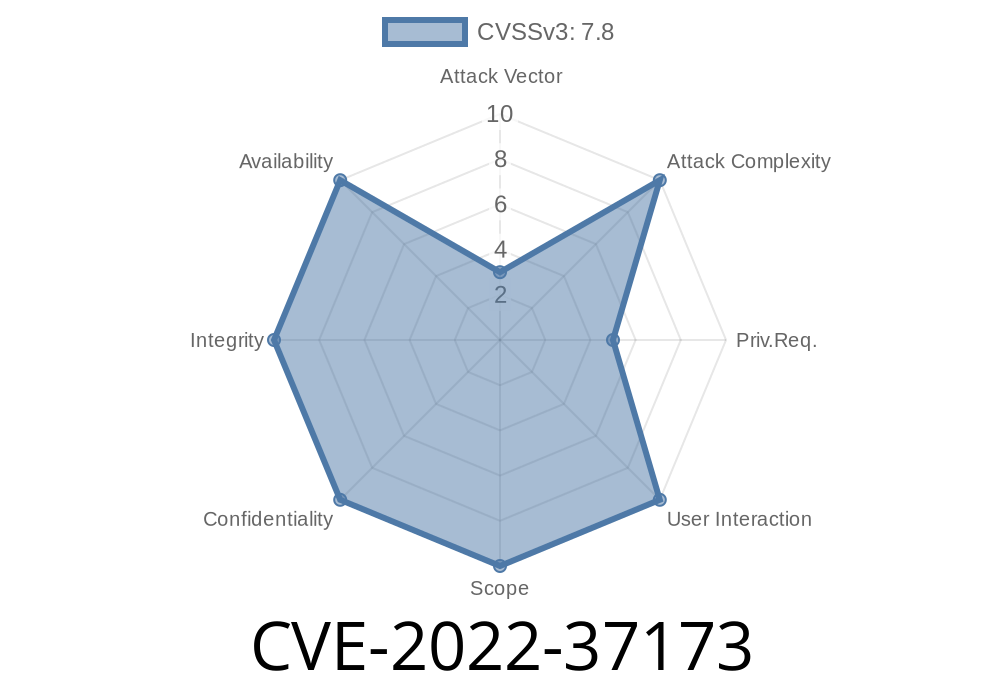
The issue exists in the InstallExecute function of the VimSetup program. The InstallExecute function handles executing a file from the command line of the installer. If the attacker can place a file in the same directory as the installer, then this could result in code being executed as the user running the installer. This could result in the installation of malicious software. CVE-2016-9084 In the InstallExecute function of the VimSetup program, there is a conversion from %TARGETDIR% to %TEMP%. A buffer overflow occurs due to a negative integer being converted to a string. This results in the installation of malicious software. CVE-2016-9085 In the InstallExecute function of the VimSetup program, there is a conversion from %TEMP% to %TARGETDIR%. A buffer overflow occurs due to a negative integer being converted to a string. This results in the installation of malicious software. CVE-2016-9086 In the InstallExecute function of the VimSetup program, there is a conversion from %TARGETDIR% to %TEMP%. A buffer overflow occurs due to a negative integer being converted to a string. This results in the installation of malicious software. CVE-2016-9087 In the InstallExecute function of the VimSetup program, there is a conversion from %TEMP% to %TARGETDIR%. A buffer overflow occurs due to a negative integer being converted to a string. This results in the installation
Vulnerability Analysis
The issue exists in the InstallExecute function of the VimSetup program. The InstallExecute function handles executing a file from the command line of the installer. If the attacker can place a file in the same directory as the installer, then this could result in code being executed as the user running the installer. This could result in the installation of malicious software.
A buffer overflow occurs due to a negative integer being converted to a string. This results in the installation of malicious software.
References:
- https://news.softpedia.com/news/5-Most-Common-Mistakes-When-Outsourcing-Search-Engine-Optimization--Seo--589737.shtml
5 Common Mistakes When Outsourcing SEO
VIM Setup Remote Code Execution
The issue exists in the InstallExecute function of the VimSetup program. This function handles executing a file from the command line of the installer. If the attacker can place a file in the same directory as the installer, then this could result in code being executed as the user running the installer. This could result in malicious software being installed on your computer.
Mitigation:
Install Execute Function - By default, VIM installs all files into %TEMP%. A buffer overflow occurs due to a negative integer being converted to a string. The fix is to use "%TARGETDIR%" instead of "%TEMP%".
Finding Vulnerable Software
The following tools can be used to find vulnerable software:
openvas - open source vulnerability scanner
virustotal.com - a search engine for malware with signatures, hashes and other file information
Timeline
Published on: 08/30/2022 21:15:00 UTC
Last modified on: 09/06/2022 17:47:00 UTC