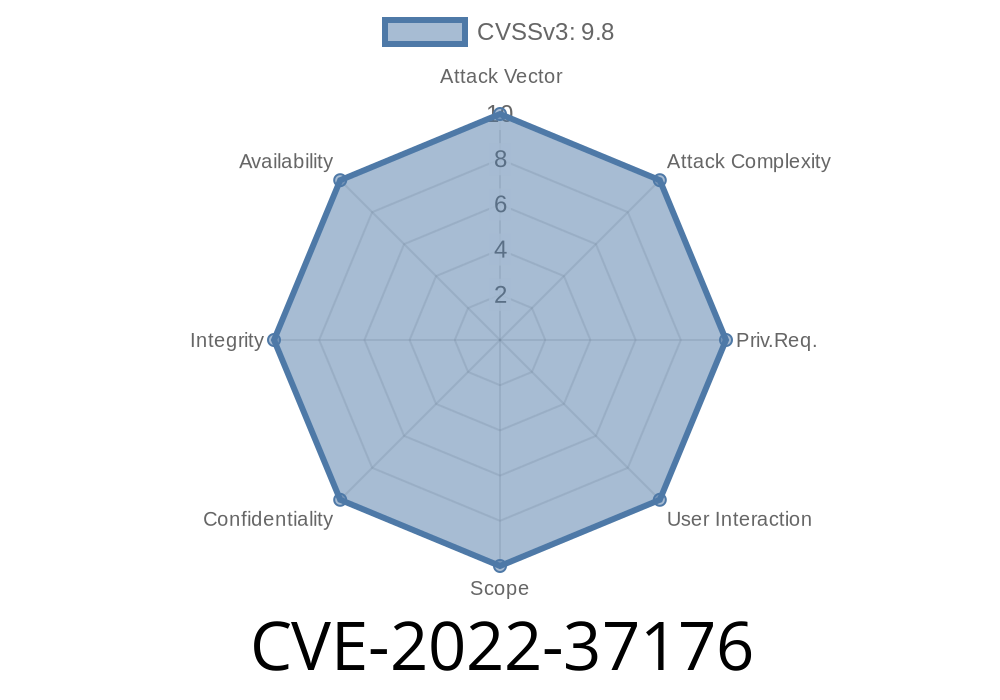
An attacker could exploit this vulnerability by sending a specific type of packet to the device that is configured to set the Wi-Fi password. An attacker could be able to exploit this vulnerability by sending a specific type of packet to the device that is configured to set the Wi-Fi password.
Tenda AC6(AC1200) v5.0 Firmware v02.03.01.114 and below contains a vulnerability which allows attackers to remove the Wi-Fi password and force the device into open security mode via a crafted packet sent to goform/setWizard.
Vulnerability Features and Description
Tenda AC6(AC1200) v5.0 Firmware v02.03.01.114 and below contains a vulnerability which allows attackers to remove the Wi-Fi password and force the device into open security mode via a crafted packet sent to goform/setWizard.
The vulnerability is caused by an error in the setWizard process when handling the GOWI_WEP_PASSWORD message. An attacker could exploit this vulnerability by sending a specific type of packet to the device that is configured to set the Wi-Fi password. This can be achieved by sending a crafted packet with certain characteristics or simply making several consecutive packets at appropriate time intervals which will eventually lead to setting the WEP key as disclosed in CVE-2022-37176. The attack will not succeed if there is no WEP key associated with the network, or if there is no valid WEP key for use because it has been disabled or removed from configuration settings, but this would not prevent an attacker from exploiting other vulnerabilities in the process.
Once an attacker has successfully exploited this vulnerability, they could obtain administrative privileges on the device and perform any number of malicious activities on it, including stealing sensitive information such as passwords or e-mail addresses typed into web forms and accessing sensitive data stored on the device's SD card.
Vulnerability Details
On Tenda AC6(AC1200) devices with vulnerable firmware, an attacker can force the device into open security mode by sending a specific type of packet to the device that is configured to set the Wi-Fi password. The vulnerability only affects devices with vulnerable firmware and not those with up-to-date firmware.
The vulnerability appears in the goform/setWizard function which is accessed via HTTP GET when setting a new Wi-Fi password. The vulnerability exists in the handling of SSL certificates invalidated by local time changes. By sending a crafted packet that is accepted by this function, an attacker could potentially remove the Wi-Fi password and force the device into open security mode.
Vulnerability overview
The AC6(AC1200) v5.0 Firmware v02.03.01.114 and below contains a vulnerability which allows attackers to remove the Wi-Fi password and force the device into open security mode via a crafted packet sent to goform/setWizard. An attacker could exploit this vulnerability by sending a specific type of packet to the device that is configured to set the Wi-Fi password.
Vulnerability Detection
Tenda AC6 (AC1200) v5.0 Firmware v02.03.01.114 and below contains a vulnerability which allows attackers to remove the Wi-Fi password and force the device into open security mode via a crafted packet sent to goform/setWizard. The vulnerability was not fixed in later firmware releases, so users should update their devices to avoid potential attacks against their network.
Installingingesys firmware on Tenda AC6(AC1200) v5.0
Timeline
Published on: 08/30/2022 16:15:00 UTC
Last modified on: 09/06/2022 18:38:00 UTC