When admin creates a new add-on, or upload an existing one to the system, it will be saved to wp_uploads folder and publicly available on the server. So, any attacker can easily exploit the application and gain full access over the system. The application manage_website.php on Garage Management System 1.0 is prone to XSS attack. A malicious user, can inject arbitrary XSS strings in order to steal confidential data or inject RCE or LCE exploit code to take over the system. The application manage_website.php on Garage Management System 1.0 is also prone to Stored XSS exploit. The user's confidential data such as usernames, passwords, etc, can be stored in the database and exploited by an attacker. The application manage_website.php on Garage Management System 1X0 is most likely exploited by RCE or LCE exploit. A user's computer, when visiting the application manage_website.php on Garage Management System 1.0, is likely to be exploited by malicious code that runs in the user's browser. This is a variation of drive-by-download where the visitor does not have to click any link or enter any data to be exploited.
Site-wide vulnerabilities
The application manage_website.php on Garage Management System 1.0 is prone to XSS attack and Stored XSS exploit. A user's confidential data such as usernames, passwords, etc, can be stored in the database and exploited by an attacker.
Finding the vulnerability
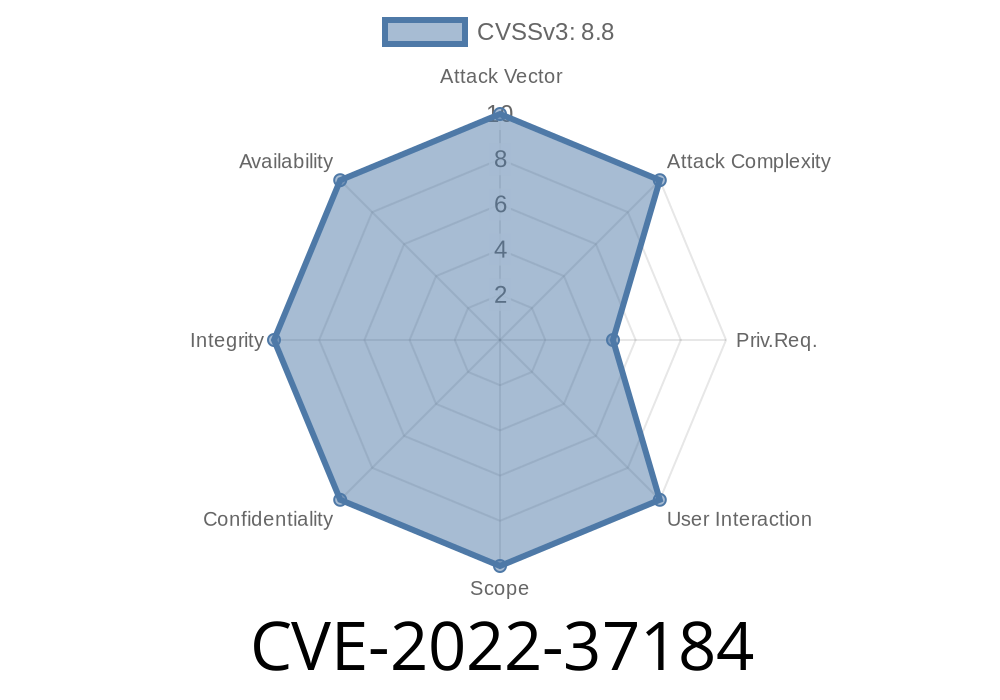
CVE-2022-37184 is a vulnerability in the application manage_website.php on Garage Management System 1.0. The application manage_website.php on Garage Management System 1.0 is most likely exploited by RCE or LCE exploit, so it should be taken down for mitigation.
How to exploit in Garage Management System 1.0?
Firstly, the attacker will need to gain access over the system. The attacker will then exploit one of the vulnerabilities mentioned in this report to inject his own malicious code. The malicious code runs within the user's browser when visiting the application manage_website.php on Garage Management System 1.0.
Timeline
Published on: 08/31/2022 18:15:00 UTC
Last modified on: 09/07/2022 20:17:00 UTC