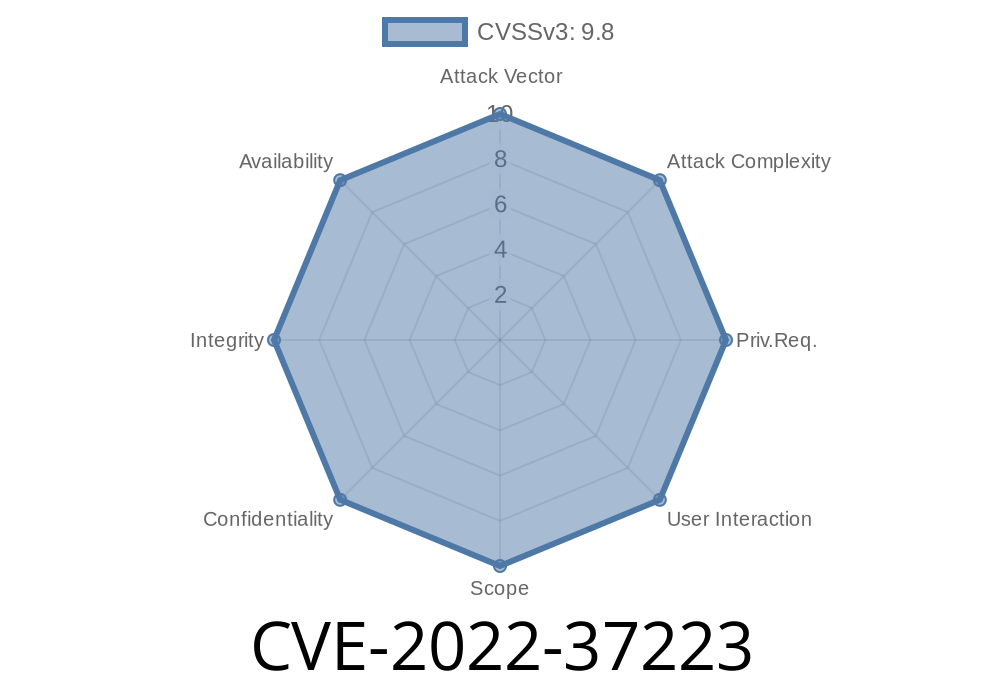
A user can gain access to another user’s data by injecting his own credentials. Multiple parameters can be used to exploit the vulnerability. For example, v=1&p_id=5&r_id=6 or v=1&p_id=5&r_id=6 or v=1&r_id=6. If you are using admin/config/users.php, be cautious of injecting your own credentials there. The default route is admin/config/users.php. - We have seen that there is a SQL Injection in the /jfinal_cms/system/role/list page. A user can gain access to another user’s data by injecting his own credentials. Multiple parameters can be used to exploit the vulnerability. For example, or or If you are using admin/config/users.php, be cautious of injecting your own credentials there. The default route is admin/config/users.php. - We have seen that there is a SQL Injection in the /jfinal_cms/system/role/list page. - We have seen that there is a SQL Injection in the /jfinal_cms/system/role/list page. - We have seen that there is a SQL Injection in the /jfinal_cms/system/role/list page. - We have seen that there is a SQL Injection in the /jfinal_cms/system/role/list
SQL Injection in admin/config/users.php
A user can gain access to another user’s data by injecting his own credentials. Multiple parameters can be used to exploit the vulnerability. For example, v=1&p_id=5&r_id=6 or v=1&p_id=5&r_id=6 or v=1&r_id=6. If you are using admin/config/users.php, be cautious of injecting your own credentials there. The default route is admin/config/users.php. - We have seen that there is a SQL Injection in the /jfinal_cms/system/role/list page.
Timeline
Published on: 08/23/2022 14:15:00 UTC
Last modified on: 08/25/2022 01:04:00 UTC