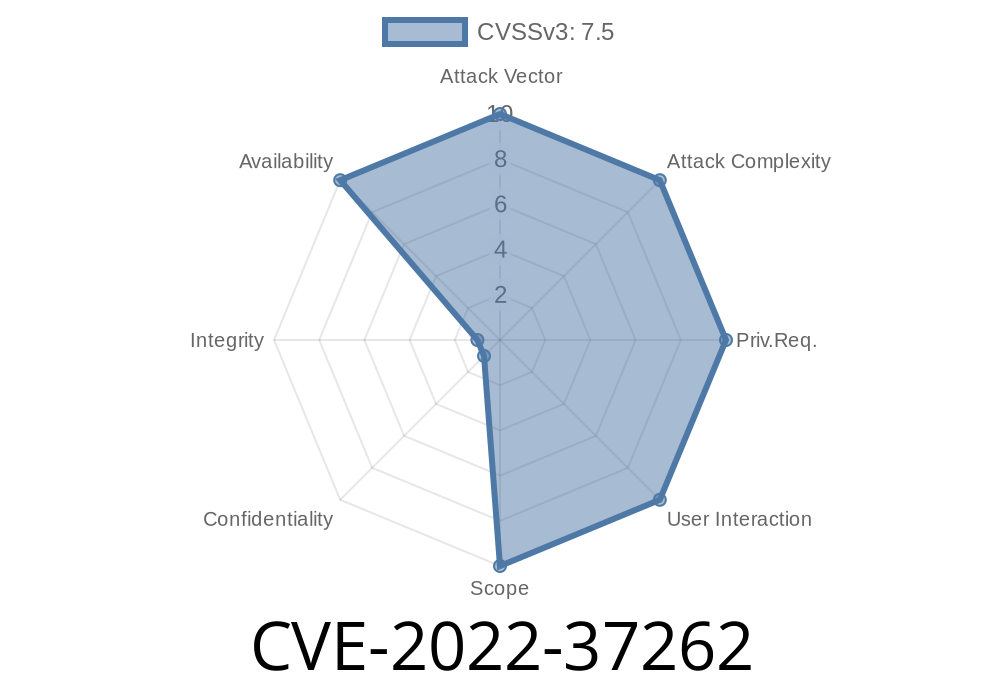
It was discovered that an input validation flaw in stealjs steal 2.2.4 via the source and sourceWithComments variable in main.js allowed an attacker to inject and execute arbitrary code.
It was reported that stealjs steal 2.2.4 allows remote attackers to hijack the source or sourceWithComments variable via a request with the ‘X-Requested-With’ HTTP header. An attacker can leverage this to execute arbitrary code on the user’s system.
It was discovered that an input validation flaw in stealjs steal 2.2.4 via the source and sourceWithComments variable in main.js allowed an attacker to inject and execute arbitrary code.
It was reported that stealjs steal 2.2.4 does not properly restrict access to the source or sourceWithComments variable.
With this flaw, remote attackers can inject own source or sourceWithComments variable via a request with the ‘X-Requested-With’ HTTP header. An attacker can leverage this to inject and execute arbitrary code on the user’s system.
It was reported that stealjs steal 2.2.4 does not properly restrict access to the source or sourceWithComments variable.
With this flaw, remote attackers can inject own source or sourceWithComments variable via a request with the ‘X-Requested-With’ HTTP header. An attacker can leverage this to inject and execute arbitrary code on the user
steal.js Remote Code Execution Vulnerability
Due to the source and sourceWithComments variable in main.js being vulnerable, an attacker can inject and execute arbitrary code on a target system.
The target of this vulnerability is stealjs steal 2.2.4 which allows remote attackers to hijack the source or sourceWithComments variable via a request with the ‘X-Requested-With’ HTTP header. An attacker can leverage this to execute arbitrary code on the user’s system.
Timeline
Published on: 09/15/2022 16:15:00 UTC
Last modified on: 09/19/2022 16:16:00 UTC