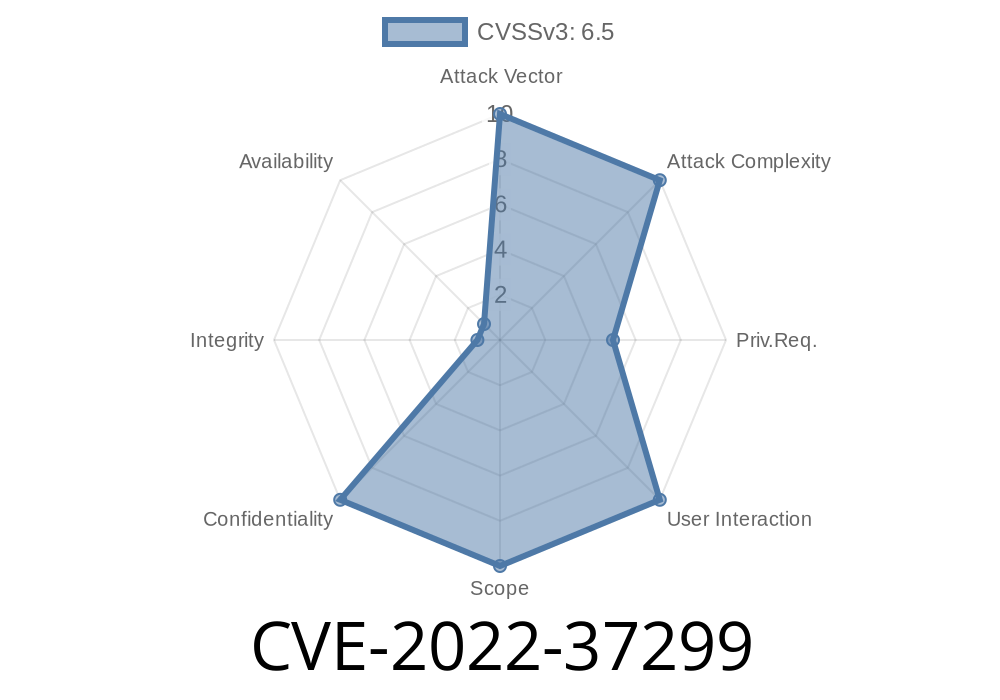
If a user has access to the /static/ueditor/php/ directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could
Shirne CMS: How an Attack works?
In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/. If a user has access to this directory and has permissions to edit files in this directory, an attacker could exploit the vulnerability. The Shirne CMS version affected is 1.2.0. In Shirne CMS, there is a directory called /static/ueditor/php/.
Shirne CMS: How an attacker would exploit the vulnerability
An attacker could exploit this vulnerability through the following means:
- A static file in /static/ueditor/php/ is allowed to read or write data in files, which are outside of its directory.
- An attacker can use the vulnerability to create a malicious PHP file that would allow arbitrary code execution.
Timeline
Published on: 09/09/2022 15:15:00 UTC
Last modified on: 09/10/2022 03:41:00 UTC