By exploiting this bug, an attacker can obtain full control over the device. This is a high risk vulnerability.
In the case of an exploited vulnerability, an attacker can establish a remote connection to the device and then obtain access to its shell. As soon as the attacker gains remote access to the device, he can install malicious software or hijack the process of the device and then obtain root access. At the moment, there are no reliable methods to protect against this vulnerability. Therefore, it is necessary to upgrade the firmware of the device as soon as possible.
In addition, users are advised to apply the standard rules for securing devices with firewalls and not to open suspicious sources of connections. What do you know about VDB-212412? Contact us on Twitter at and let us know.
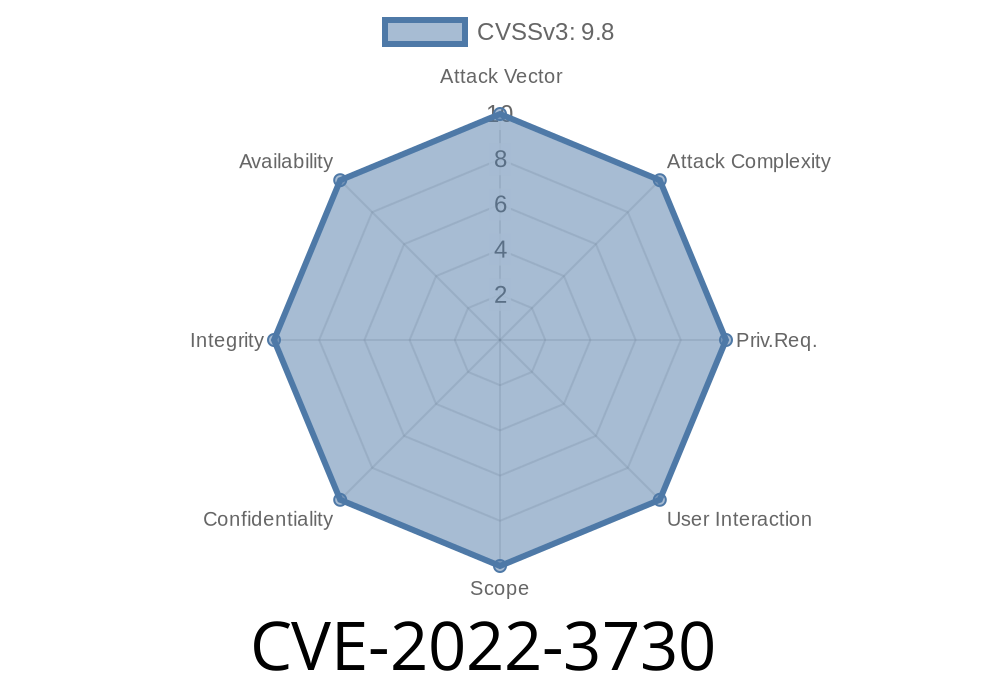
A critical vulnerability, which was classified as critical, was found in seccome Ehoney. Affected is an unknown function of the file /api/v1/attack/falco. The manipulation of the argument Payload leads to sql injection. It is possible to launch the attack remotely. The identifier of this vulnerability is VDB-212412.
By exploiting this bug, an attacker can obtain full control over the device. This is a high risk vulnerability.In the case of an exploited vulnerability, an attacker can establish a remote connection to the device and then obtain access to its shell. As soon as the attacker gains remote access to the device, he
Vulnerability Discovery and Description
In seccome Ehoney, there is a critical vulnerability. It was found in the file /api/v1/attack/falco. The manipulation of the argument Payload leads to sql injection. It is possible to launch the attack remotely.
VDB-221312
The vulnerability in the device can be exploited by sending a packet with the VDB-221312 identifier. In case of successful exploitation, an attacker can establish a connection to the device and then gain root access.
In addition, users are advised to apply the standard rules for securing devices with firewalls and not to open suspicious sources of connections. What do you know about VDB-212412? Contact us on Twitter at and let us know.
VDB-212412: How does seccome Ehoney work? seccome Ehoney is a platform on which you can achieve the goal of seccome. It enables the user to run calculations for the production of cookies and start generating codes for advertising. On the website, it is possible to configure webpage settings and monitor them from a remote location. The website also offers a home page that contains calculators and functions that enable users to generate codes in order to create new campaign or configure existing ones.
The vulnerability in this platform is found in an unknown function of the file /api/v1/attack/falco. The manipulation of the argument Payload leads to sql injection. It is possible to launch the attack remotely. There are known risks associated with this vulnerability, one of which might be launching attack remotely without authorization. The identifier of this vulnerability is VDB-212412.
Timeline
Published on: 10/28/2022 08:15:00 UTC
Last modified on: 10/31/2022 19:19:00 UTC