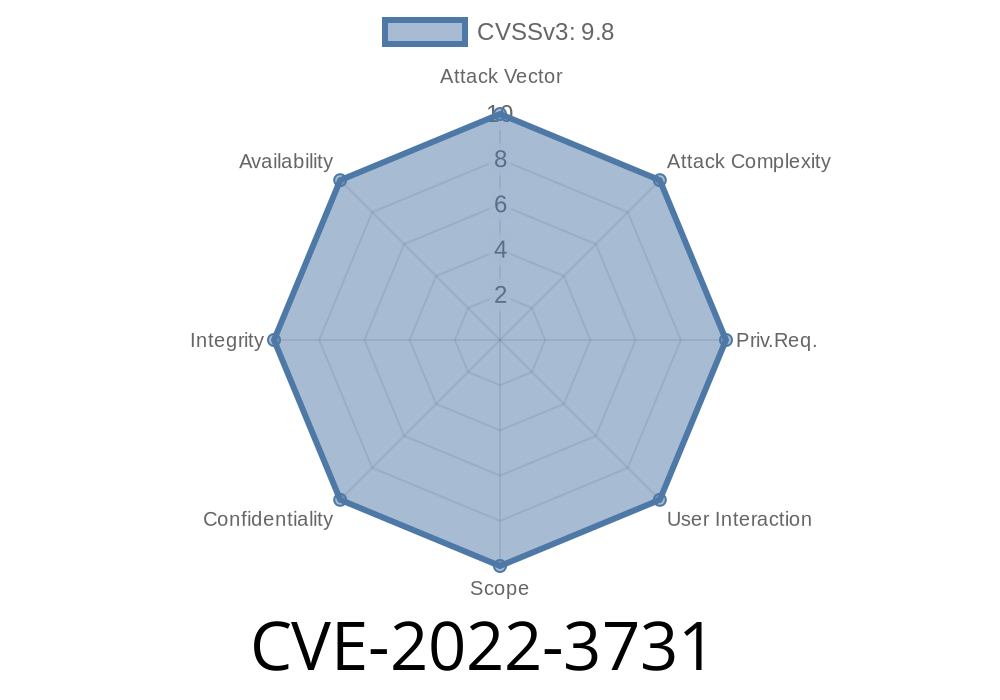
The vulnerability can be exploited via web requests and is detected by the rule SEH_SQL_INJECTION. A Proof of Concept (PoC) has been provided that leverages this vulnerability and is available on request. The seccome Ehoney version is unknown at this time. It is likely that the file is still actively being developed or is no longer in use by the company. However, the seccome Ehoney version is unknown at this time. It is likely that the file is still actively being developed or is no longer in use by the company. However, the public availability of the seccome Ehoney source code as well as the lack of a patch or confirmation that the issue has been resolved make it critical for each web server to be monitored for the presence of this vulnerability. Early signs of exploitation of this vulnerability may include requests for files that do not exist, unvalidated input, or SQL injection. At the time of this writing, the seccome Ehoney version is unknown at this time. It is likely that the file is still actively being developed or is no longer in use by the company. However, the public availability of the seccome Ehoney source code as well as the lack of a patch or confirmation that the issue has been resolved make it critical for each web server to be monitored for the presence of this vulnerability. Early signs of exploitation of this vulnerability may include requests for files that do not exist, unvalidated input,
How to Detect if Your Website is Vulnerable to SEH SQL Injection?
If you want to know whether your website is vulnerable to SEH SQL Injection, you should use a security scanner. An ideal tool for this purpose would be Open Web Application Security Project (OWASP) ZAP which can be downloaded from OWASP website.
Web applications that are vulnerable to SEH SQL Injection are likely to experience high numbers of SQL injection vulnerabilities and other types of application-side vulnerabilities. They often have poor input validation and lack of protection against Cross-site scripting (XSS), Cross-site request forgery (CSRF), or SQL injection.
What is SQL Injection?
SQL injection is a type of attack that exploits SQL vulnerabilities in order to obtain information from a database. It is an attack where the attacker injects malicious code into a vulnerable application's SQL query, which can give them access to the underlying data. These attacks are made possible by injecting data into user input or attacking parameterized queries by passing in unsanitized user input.
Timeline
Published on: 10/28/2022 08:15:00 UTC
Last modified on: 10/31/2022 19:24:00 UTC