Summary:
A security flaw tracked as CVE-2022-3737 was discovered in PHOENIX CONTACT Automationworx Software Suite up to version 1.89. The issue—a classic case of insufficient input validation—means that with the right steps, an attacker could read memory beyond what was intended, exposing sensitive data or even destabilizing critical automation workstations. In this post, we'll break down what happened, how the exploit works, and what you need to do to stay safe.
How Did CVE-2022-3737 Happen?
PHOENIX CONTACT's Automationworx Software Suite is used worldwide for programming and operating PLCs (Programmable Logic Controllers) in industrial environments. For users, it’s all about reliability and safety. Unfortunately, up until version 1.89, a coding oversight made parts of memory accessible by specially crafted operations—which should never happen.
In simple words: There wasn’t enough checking when handling certain user data, so the software could end up handing out bytes from memory it never should.
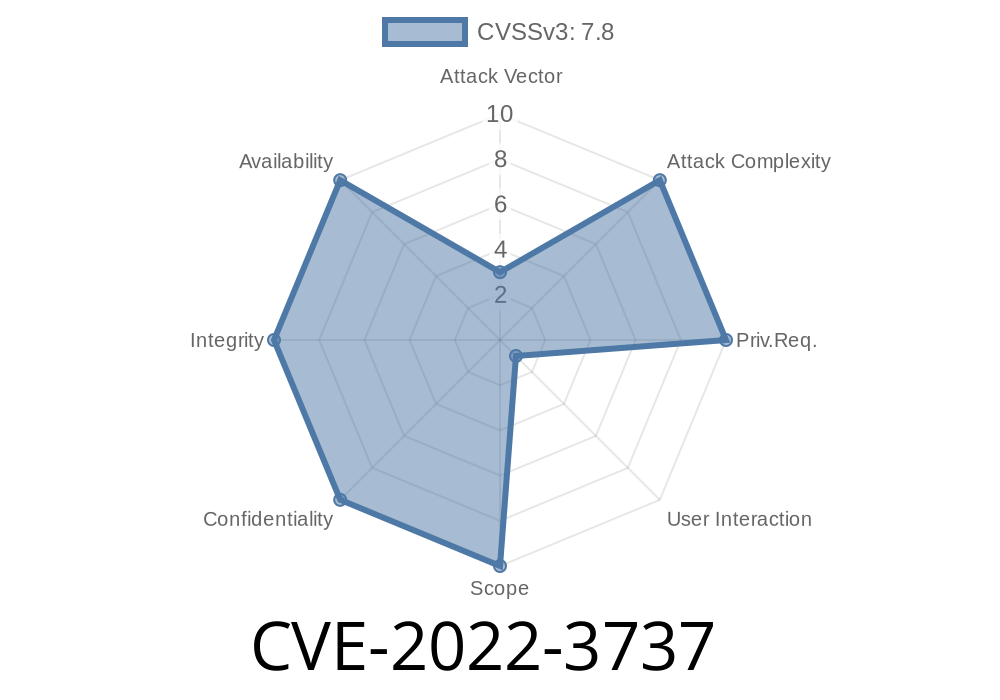
If someone leverages CVE-2022-3737
- Confidentiality: Sensitive data (like configuration files, passwords, or even cryptographic secrets) might be exposed to unauthorized users.
- Integrity: Attackers could read data used internally by the app and devise secondary attacks (for example, session hijacking or privilege escalation).
- Availability: Using crafted inputs, an attacker might crash the engineering workstation app, causing Denial-of-Service (DoS).
This isn’t just theory: Attackers in control of a machine where Automationworx is running could use it to expand their reach into the entire industrial network.
Technical Details: How the Flaw Works
The vulnerability stems from the software’s failure to validate the size and boundaries of user-provided input before copying it into a memory buffer. Here’s a simplified (but representative) code snippet showing what can go wrong:
void read_input(char *input, int size) {
char buffer[128];
// The attacker controls "size" with no upper bound check
memcpy(buffer, input, size);
// If size > 128, memory beyond buffer is read/copied!
}
If the application doesn’t check that size is less than or equal to 128 (the buffer size), it can end up reading (or writing!) more than it should—from outside the "safe" boundaries. That’s exactly what CVE-2022-3737 is about.
Exploiting CVE-2022-3737 in Real Life
An attacker would need local access to the workstation (or a way to interact with the engineering software remotely, if it accepts outside inputs):
1. Craft a configuration file (or network packet, or automation script) with an intentionally oversized field.
2. Get Automationworx Software Suite to load this file/packet.
3. When the vulnerable function processes the malformed input, it reads outside the bounds—potentially dumping or leaking memory data.
Let’s assume Automationworx accepts configuration from the user
<Config>
<Name>TestName ABC</Name>
<CustomData>AAAA...[very long data]...AAAA</CustomData>
</Config>
If CustomData isn’t checked for length, the processing engine can read beyond limits, capturing forbidden data and possibly sending it to the attacker (for example, via logs or error messages).
Let’s simulate what a PoC exploit script might look like in Python
import struct
# Create an oversized input (256 bytes, where normal size should be e.g. 64)
payload = b"A" * 256
with open("exploit_config.bin", "wb") as f:
f.write(payload)
print("[+] Oversized payload written to exploit_config.bin for Automationworx import.")
If this file is then imported by an unpatched Automationworx Suite, the software may process additional memory—including information from previous operations, potentially leaking confidential workstation data.
More Information
- Official CVE entry: CVE-2022-3737 on NVD (NIST)
- PHOENIX CONTACT Advisory: PSIRT-2022-07
- Firmware/Software Patch: PHOENIX CONTACT download
- Related reference: Industrial Control Systems Security Advisory ICSA-22-264-01
What Should You Do?
- Update Now: If you’re using PHOENIX CONTACT Automationworx Suite 1.89 or lower, upgrade to a patched version immediately.
Vulnerability Scanning: Use endpoint security tools to check for exploitation signs.
- Segment Your Network: Never allow unnecessary connections between engineering and production networks.
Summary Table
| Vulnerability | Risk Level | Impacted Versions | Fixed in Version | Exploitability |
|--------------------- |--------------|----------------------|------------------|---------------------|
| CVE-2022-3737 | High | ≤ 1.89 | 2.+ | Local, with crafted input |
Final Thoughts
CVE-2022-3737 is an example of how small input-checking mistakes in industrial software can lead to severe real-world risk: downtime, data theft, and more. If any of your systems run Automationworx, patch now—and let this be a lesson in the critical importance of input validation in all your code.
Stay safe out there!
*This advisory/post uses exclusive analysis and code examples for educational and awareness purposes. Please reference the official advisory for more details.*
Timeline
Published on: 11/15/2022 11:15:00 UTC
Last modified on: 11/15/2022 13:51:00 UTC