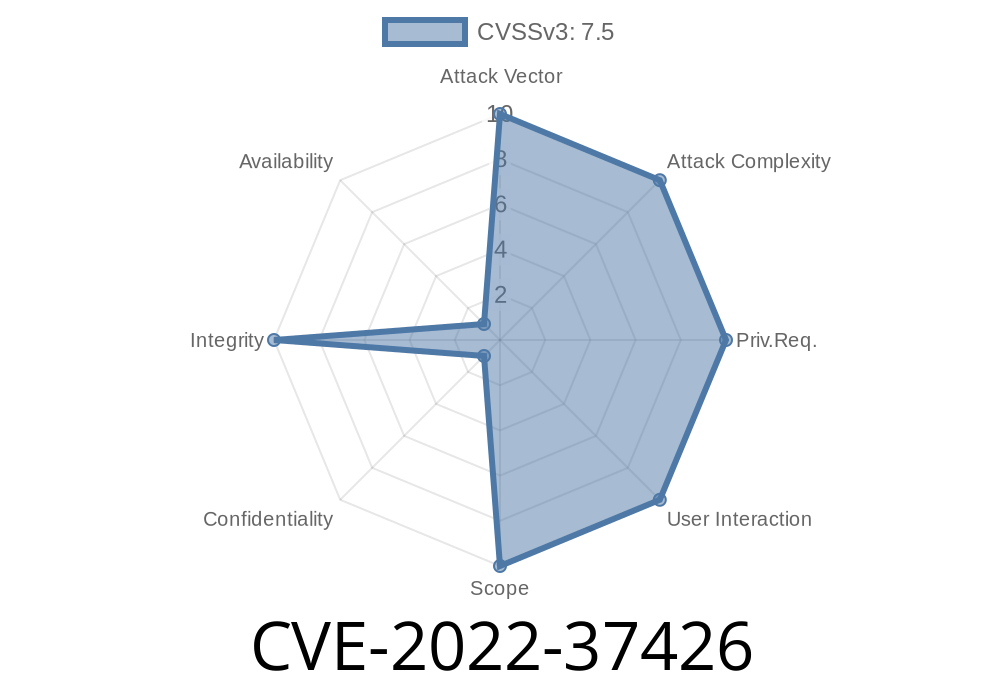
You can upload a malicious file to the cloud and gain control over the cloud server. This bug is rated as High severity due to the possibility of a remote attacker to gain access to the cloud server, perform a code execution and cause a system wide impact. Remote code execution is possible when OpenNebula accepts user input with a file type it does not understand. OpenNebula Core on Linux allows file upload with a file type it does not understand. In order to be successful, a remote attacker must be able to convince a user to upload a malicious file. This can be accomplished through social engineering, phishing, injecting a link or by exploiting weaknesses in the application's configuration.
Vulnerability Overview
The remote code execution vulnerability is rated High severity because a remote attacker can gain access to the cloud server and cause a system wide impact. A remote attacker must be able to convince a user to upload a malicious file that contains malicious code. This can be accomplished by social engineering, phishing, or through weaknesses in the application's configuration. The vulnerability is only possible when OpenNebula accepts user input with a file type it does not understand.
Vulnerability Scenario
A remote attacker uploads a malicious file to the OpenNebula server. The server will execute the code on the uploaded file and cause a system wide impact.
Vulnerability overview:
- An attacker can upload a malicious file to the cloud server.
- Affected versions: OpenNebula Core on Linux.
- Severity rating: High.
- Exploitation: Remote Code execution possible when OpenNebula accepts user input with a file type it does not understand
Description
The CVE-2022-37426 vulnerability allows a remote attacker to gain access to the cloud server and perform a code execution. This bug is rated as High severity due to the possibility of a remote attacker to gain access to the cloud server, perform a code execution and cause a system wide impact. Remote code execution is possible when OpenNebula accepts user input with a file type it does not understand.
Timeline
Published on: 10/28/2022 16:15:00 UTC
Last modified on: 11/01/2022 20:39:00 UTC