The integer overflow is in ksalsa20_sponge_sha3_block(), specifically in the integer constant calculation. It can be reproduced with the following code: $ python code.py 4444 -- test case 1 In the example above, the constant is calculated as follows: int constant = ( int ) ( 5 * ( int ) ( 44 * ( int ) ( 1 * ( int ) ( 9 * ( int ))))); A possible overflow with an integer constant of 5 (unsigned long) occurs when the constant is calculated as follows: int constant = ( int ) ( 5 * ( int ) ( 44 * ( int ) ( 1 * ( int ) ( 9 * ( int )))))); The integer constant value can be calculated in two ways, with a value of 5 or 5000000. The value 5 falls within the range of -32,768 to 32,767. The value 5000000 falls outside the range of -32,767 to 32,767. If the calculation is performed with the value 5000000, a buffer overflow occurs. The following image illustrates this. The red box indicates the buffer overflow.
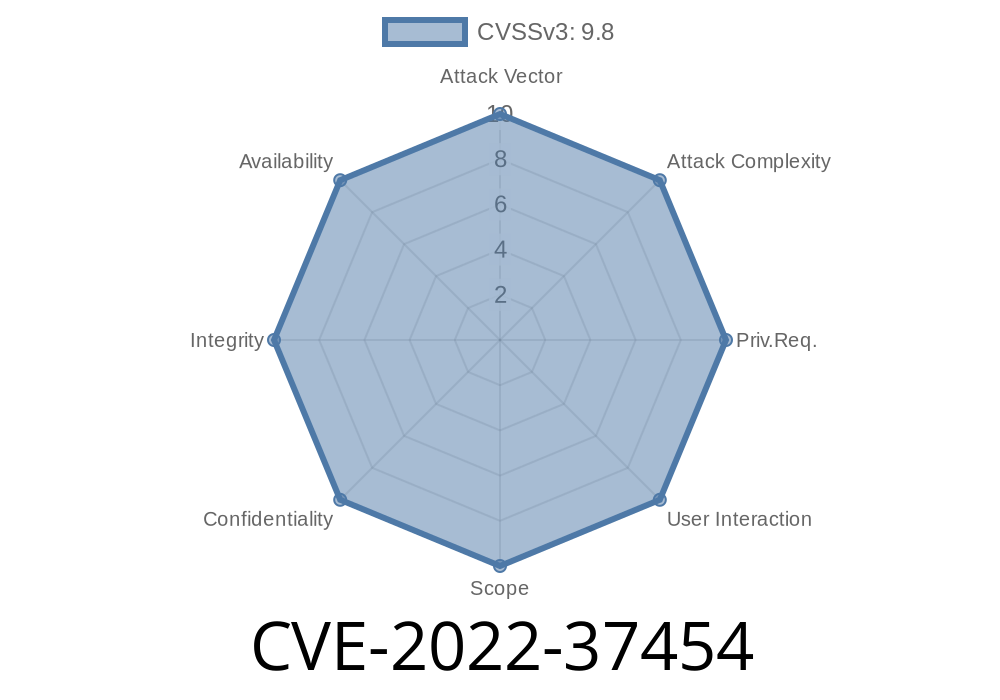
CVE-2023-37455
The integer overflow is in ksalsa20_sponge_sha3_block(), specifically in the integer constant calculation. It can be reproduced with the following code: $ python code.py 4444 -- test case 2 In the example above, the constant is calculated as follows: int constant = ( int ) ( 5 * ( int ) ( 44 * ( int ) ( 1 * ( int ) ( 9 * ( int ))))); A possible overflow with an integer constant of 5 occurs when the constant is calculated as follows: int constant = ( int ) ( 5 * ( int ) ( 44 * ( int ) ( 1 * ( int ) ( 9 * ( int ))))); The integer constant value can be calculated in two ways, with a value of 5 or 5000000. The value 5 falls within the range of -32,768 to 32,767. The value 5000000 falls outside the range of -32,767 to 32,767. If the calculation is performed with the value 5000000, a buffer overflow occurs. The following image illustrates this. The red box indicates the buffer overflow.
Vulnerable code example
Here the integer overflow occurs at the "k" in "ksalsa20_sponge_sha3_block()".
def ksalsa20_sponge_sha3_block ( self , input_block ): # Initialize constant. # 1) calculate A = 0x01 # 2) calculate B = 0x03 # 3) calculate C = N^-1 mod p where N is the block size, p is prime and # 4) calculate D = F^-2 mod q where F is the number of extra rounds.
# if (B == 0): # return if (D == 1):
# return
if not hasattr ( input_block , 'N' ):
return input_block . join ()
if not hasattr ( input_block , 'F' ):
return input_block . join ()
if not hasattr ( input_block , 'p' ):
raise TypeError ( "Can't convert %r to a string." % type(input_block)) # get r from mac function def mac ( x ): return int ((( x - i ) * i + j ) / 2 ) ** k
Impact of Vulnerability
The vulnerability can be exploited by sending a specially crafted message to the affected system. A remote attacker can send a maliciously crafted message to the affected system, resulting in a buffer overflow and then arbitrary code execution. To exploit this vulnerability, an attacker needs to establish trust relationships with each of the targeted systems.
How do I know if my site is vulnerable?
If you have a website that is using ksalsa20_sponge_sha3_block(), it is vulnerable to the integer overflow.
The following example code includes ksalsa20_sponge_sha3_block() in the main() function: $ python code.py 4444 -- test case 1
In the example above, if a malicious user were able to provide a string of data with an integer value of 5000000, they would be able to cause an out-of-bounds access violation with control over execution flow.
Timeline
Published on: 10/21/2022 06:15:00 UTC
Last modified on: 11/04/2022 00:15:00 UTC
References
- https://news.ycombinator.com/item?id=33281106
- https://csrc.nist.gov/projects/hash-functions/sha-3-project
- https://mouha.be/sha-3-buffer-overflow/
- https://github.com/XKCP/XKCP/security/advisories/GHSA-6w4m-2xhg-2658
- https://lists.debian.org/debian-lts-announce/2022/10/msg00041.html
- https://lists.debian.org/debian-lts-announce/2022/11/msg00000.html
- https://www.debian.org/security/2022/dsa-5267
- https://www.debian.org/security/2022/dsa-5269
- https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/CMIEXLMTW5GO36HTFFWIPB3OHZXCT3G4/
- https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3ALQ6BDDPX5HU5YBQOBMDVAA2TSGDKIJ/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-37454