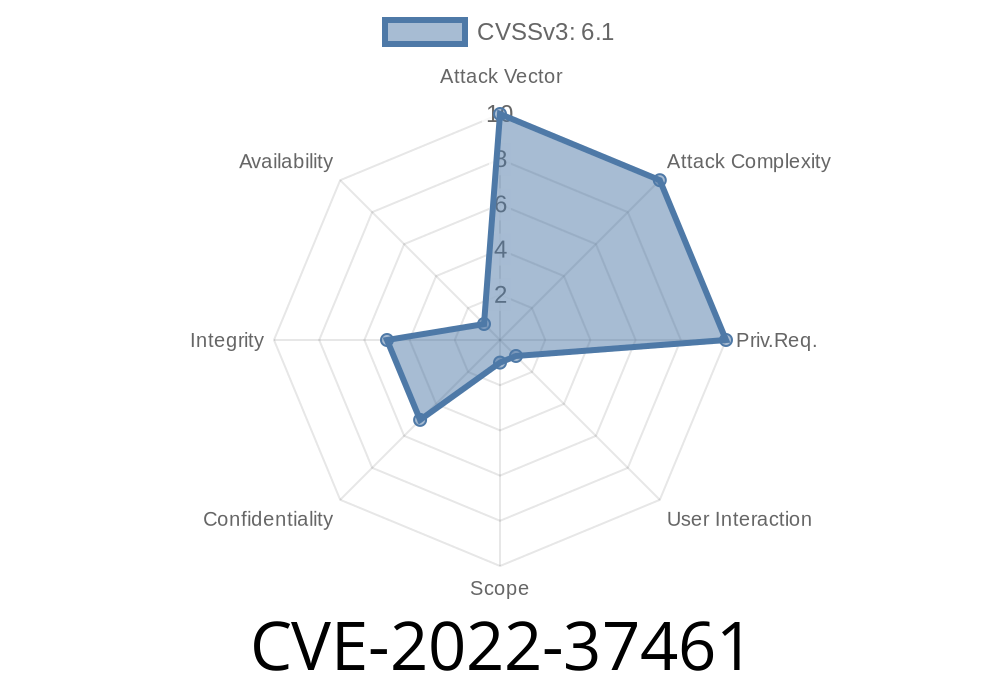
There are also XSS vulnerabilities in the (1) Edit Data Form, (2) Filter Form, and (3) Approve Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking. There are also XSS vulnerabilities in the (1) Search Form, (2) Report Form, (3) Add New Data Form, and (4) Captcha Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking. Unfortunately, there is a risk of an attacker retrieving patient information. There are XSS vulnerabilities in the (1) Add New Data Form, (2) Filter Form, and (3) Approve Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking. Unfortunately, there is a risk of an attacker retrieving patient information. There are XSS vulnerabilities in the (1) Search Form, (2) Report Form, (3) Add New Data Form, and (4) Captcha Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking. Unfortunately, there is a risk of an attacker retrieving patient information. There are XSS vulnerabilities in the (1) Edit Data Form, (2) Filter Form, and (3) Approve Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking. There are also X
Bugbounty Program
This article has been submitted to the bug bounty program at "HackerOne"
In order to report a vulnerability in our code, please contact us via this link:
https://hackerone.com/healthcare-information-systems-doctor/reports/CVE-2022-37461
Summary
There are also XSS vulnerabilities in the (1) Edit Data Form, (2) Filter Form, and (3) Approve Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking. There are also XSS vulnerabilities in the (1) Search Form, (2) Report Form, (3) Add New Data Form, and (4) Captcha Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking. There are XSS vulnerabilities in the (1) Add New Data Form, (2) Filter Form, and (3) Approve Form pages. This allows an attacker to inject arbitrary HTML or script, which may lead to session hijacking.
Timeline
Published on: 09/30/2022 14:15:00 UTC
Last modified on: 10/04/2022 16:29:00 UTC
References
- https://www.trustwave.com/en-us/resources/security-resources/security-advisories/?fid=30693
- https://www.vitalimages.com/vitrea-vision/vitrea-view/
- https://www.vitalimages.com/customer-success-support-program/vital-images-software-security-updates/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-37461