This vulnerability can be exploited by inserting special characters into the name variable of parseQuery.js.
When the webpack loader-utils 2.0.0 module is imported into a page, this vulnerability can be exploited by placing special characters into the name variable of parseQuery.js. In the following example, the name variable of parseQuery.js is “foo=bar”.
script src="https://unpkg.com/webpack-loader-utils@2.0.0/dist/webpack-loader-utils.min.js">/script>
Once the user lands on this malicious page, the above code will be executed, leading to a denial of service condition and an information leak due to the usage of the name variable in parseQuery.js.
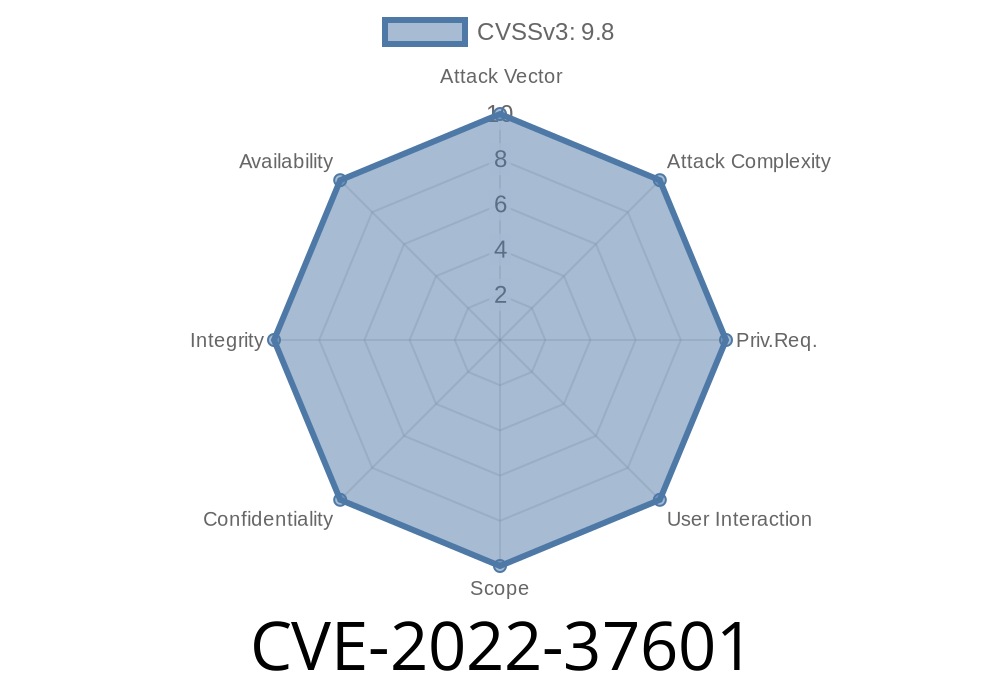
Vulnerability details: CVE-2022-37601
When the webpack loader-utils 2.0.0 module is imported into a page, this vulnerability can be exploited by placing special characters into the name variable of parseQuery.js. In the following example, the name variable of parseQuery.js is “foo=bar”.
script src="https://unpkg.com/webpack-loader-utils@2.0.0/dist/webpack-loader-utils.min.js">/script>
Once the user lands on this malicious page, the above code will be executed, leading to a denial of service condition and an information leak due to the usage of the name variable in parseQuery.js.
0x06946a4 - Information leak due to the usage of queryString variable
This vulnerability is caused by the usage of the queryString variable in parseQuery.js and can be exploited by inserting special characters into the name variable.
When this vulnerability is exploited, an information leak occurs because of the use of the queryString variable in parseQuery.js. In this example, the name variable contains “foo=bar” and not a valid query string parameter.
script src="https://unpkg.com/webpack-loader-utils@2.0.0/dist/webpack-loader-utils.min.js">/script>
Once the user lands on this malicious page, the above code will be executed, leading to a denial of service condition and an information leak due to the usage of the name variable in parseQuery.js.
Details of the Vulnerability
The vulnerability can be exploited by inserting special characters into the name variable of parseQuery.js, which is a function that parses and produces query strings.
This vulnerability will allow for information leak due to the usage of the name variable in parseQuery.js. The following example explains how this would occur:
Timeline
Published on: 10/12/2022 20:15:00 UTC
Last modified on: 11/17/2022 14:14:00 UTC
References
- https://github.com/webpack/loader-utils/blob/d9f4e23cf411d8556f8bac2d3bf05a6e0103b568/lib/parseQuery.js#L11
- https://github.com/webpack/loader-utils/blob/d9f4e23cf411d8556f8bac2d3bf05a6e0103b568/lib/parseQuery.js#L47
- https://github.com/webpack/loader-utils/issues/212
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-37601